Ladies and Gentleman, I'm pleased to announce that Open Source Surveillance has been finished and it's free to register for a demo version.
TL;DR
I've published demo version of real-time intelligence gathering tool, free to register for everyone. It contains only three modules - Flickr, Surveillance Cameras and Road Traffic, with no extra features. Full version is almost ready, but is planned to be released publicly in mid September at the latest.

If you are urgently in need of full access, feel free to write me an email.
Direct link to registration
https://demo.os-surveillance.io/login/auth0
In this article, I will explain basic functionalities, we go through first search, as well as present real world use cases from my previous research.
First things first, to get familiar with the tool, please read all posts related to the topic.
- Introduction

2. Social media module

- Geolocation
- Missing people
- Espionage
- Monitor critical facilities
- Track riots
3. Public & Surveillance and Internet exposed cameras

- Espionage on critical infrastructure
- Hacking cameras with public exploits
4. Events and transportation

- Real time transportation systems
- Vessels & Planes & Trains & Traffic & Road incidents
At the beginning, I want to thank all Patreon subscribers for the last couple months. With your help, I was able to constantly update the tool, setup proper infrastructure and share it with everyone right now. Part of the funds, were donated to the Ukraine Army. Thank you.

Also feel free to join official Offensive OSINT Discord server
You can ask questions about the tool or OSINT in general and I will be more than happy to help.
Introduction
I can't believe it's already fifth season of Offensive OSINT, paraphrasing Community - "Four seasons and a movie", this is the last season of Offensive OSINT, which focuses on the OSS and I'm not sure if it will be finished.
Alpha version was released at the end of January and around 300 people signed up for the project, what is very satisfying based on my advertising and amount of Twitter followers.
I have met interesting people and made a solid connections in variety field of cyber security and intelligence. In addition, since first release, Open Source Surveillance went through completely new phase including graphical interface, modules & sources or backend stability.
Enough of the story, let's talk about the tool finally.
Open Source Surveillance is a real-time intelligence gathering system based on particular location. Currently, it supports 18 different sources:
- Social Media
- Flickr
- Snapchat
- Youtube
- Vkontakte
- Strava
- Sportstracker
- Alltrails
- Networks
- Wifi
- Cell towers
- Bluetooth
- Events
- Crimes
- Amber Alerts
- Public Cameras
- Weather
- Street
- Surveillance
- Traffic
- IoT
- MQTT
- Printers
- Internet exposed cameras
- Screenshots
- RTSP
- Amcrest
- Netwave
- HikVision
- Dlink
- Dahua
- Blueiris
- Geohttpserver
- Mobotix
- Avtech
- Motioneye
- Vulnerabilities
- Proxyshell
- Bluekeep
- Industrial Control Systems
- Bacnet
- Tridium Niagara
- Fuel tanks
- Nordex wind turbines
- IPC@CHIP from Beck
- Red Lion Controls
- OMRON
- IEC 60870-5-104
- Siemens
- Modbus
- Building Operation Workstations by Schneider Electric
- NMEA protocl
Last four use Shodan to detect open or vulnerable devices in specific location.
Why? Who will use it?
I was asked these questions multiple times, and there are many potential use cases for the tool, depends of your circle of interests. As you might read in the previous articles, this system can be used to support variety of law enforcement and OSINT investigations in terms of missing people or general public safety.
In addition, you can find precise movements of former top Biden official

or track russian position and military facilities
Tracking Russian positions & military installations via Vkontakte and looking for military bases in Strava never been easier. These features have been added to the Open Source Surveillance #osint #intelligence https://t.co/ZkycoGwL6Z pic.twitter.com/7mpzRDTKGC
— Offensive OSINT (@the_wojciech) February 26, 2023
Search for amazon warehouses by correlating public Wifi names (described in Introduction article)
There is also a cyber security side of the tool, very well known from Kamerka. You can find vulnerable or completely unsecured open cameras, Internet of Things or Industrial Control system devices on specific territory. However, we are all aware that this is only IP based location, which not exactly gives precise results, so you have to use variety of techniques to make sure device is located in the place you think it is.
Monitoring different social medias during protests, tracking crimes or Amber Alerts and cross reference it with live footage from cameras, protect critical facilities in the city, on the ground and Internet, ensure public safety and support analysts in the OSINT investigations, that's the main role of Open Source Surveillance.
Demo version
For now, I can release only demo due to ongoing legal paperwork, and technical limitations. However, when I sort things out, I hope to share full version with everyone.
This version is limited to three modules - Flickr, Road Traffic and Surveillance Cameras. First module is self explanatory and it's taken from Explore Map functionality.
Surveillance Cameras uses Open Street Map and Overpass API, you can find more about it in s04e07. You can't get a footage from camera, since it's most probably closed circuits, but during investigations it's good to know where such cameras might be located.
Road Traffic is based on Google, and it's part of the bigger Transportation module, which includes also Vessels, Planes, Incidents and Amtrak trains.

Quick tutorial
After register, you will be greeted with following screen
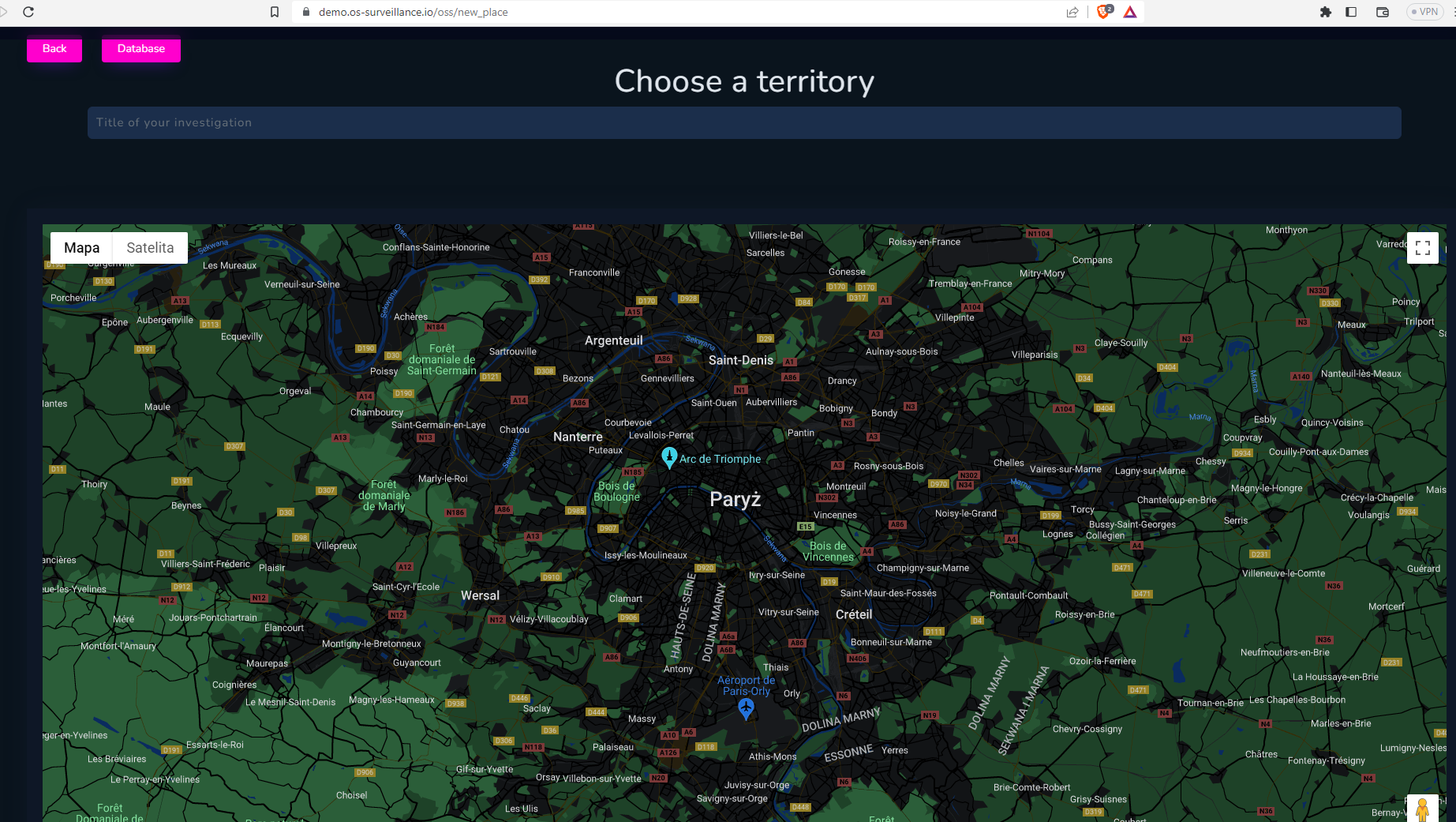
First thing to do is to add new territory to investigate, and name it properly.
and we are ready to proceed, below is a main screen of the tool, where whole action takes place.
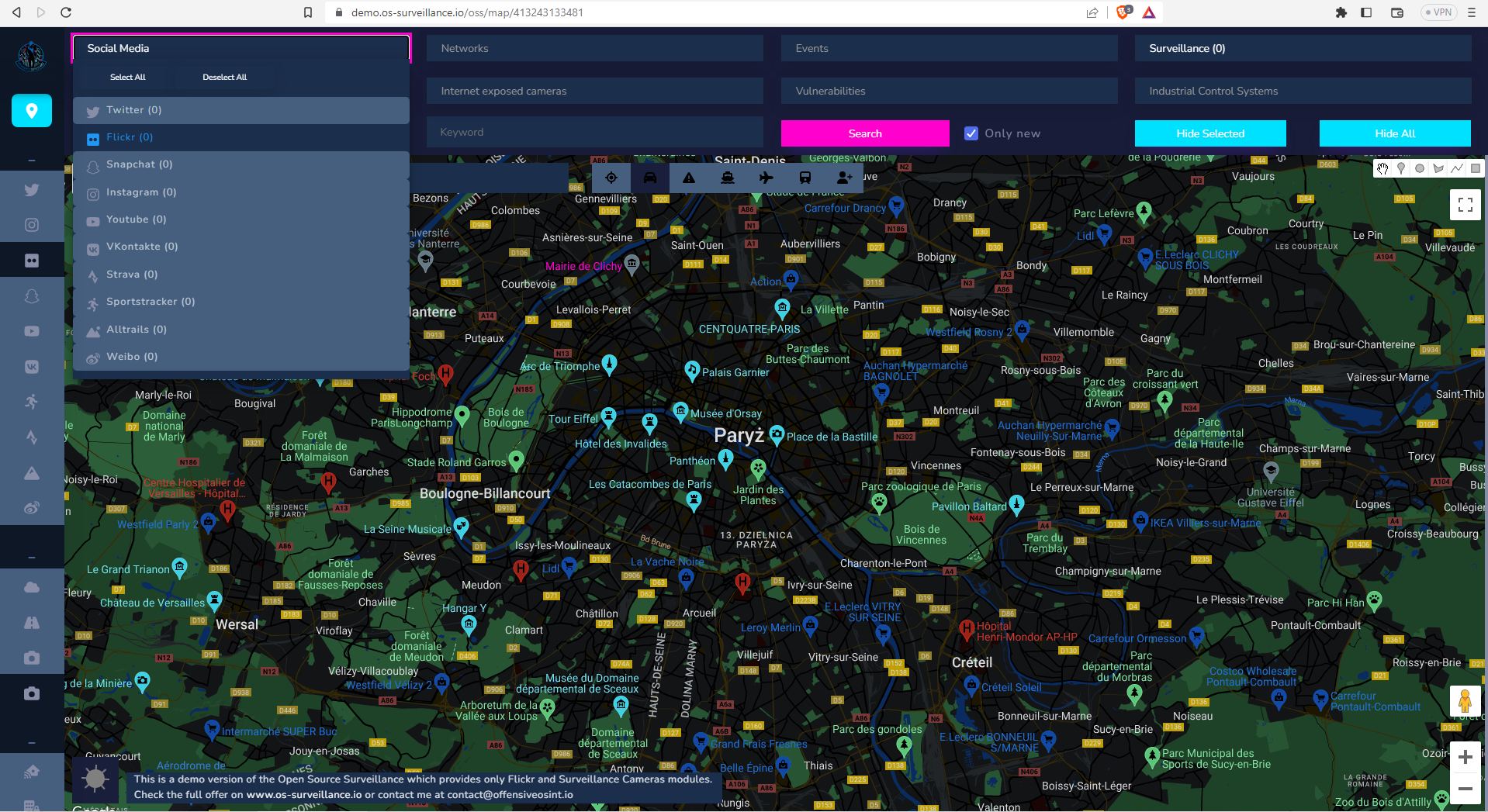
Top menu is separated by modules, first is Social Media where you can pick only Flickr, you will discover rest on your own.
When you picked your modules, click on the map and put the marker on the location you want to search, next click "Search" and after couple seconds, results will be presented on the map. Request time depends on 3rd party service and amount of findings from the specific module.
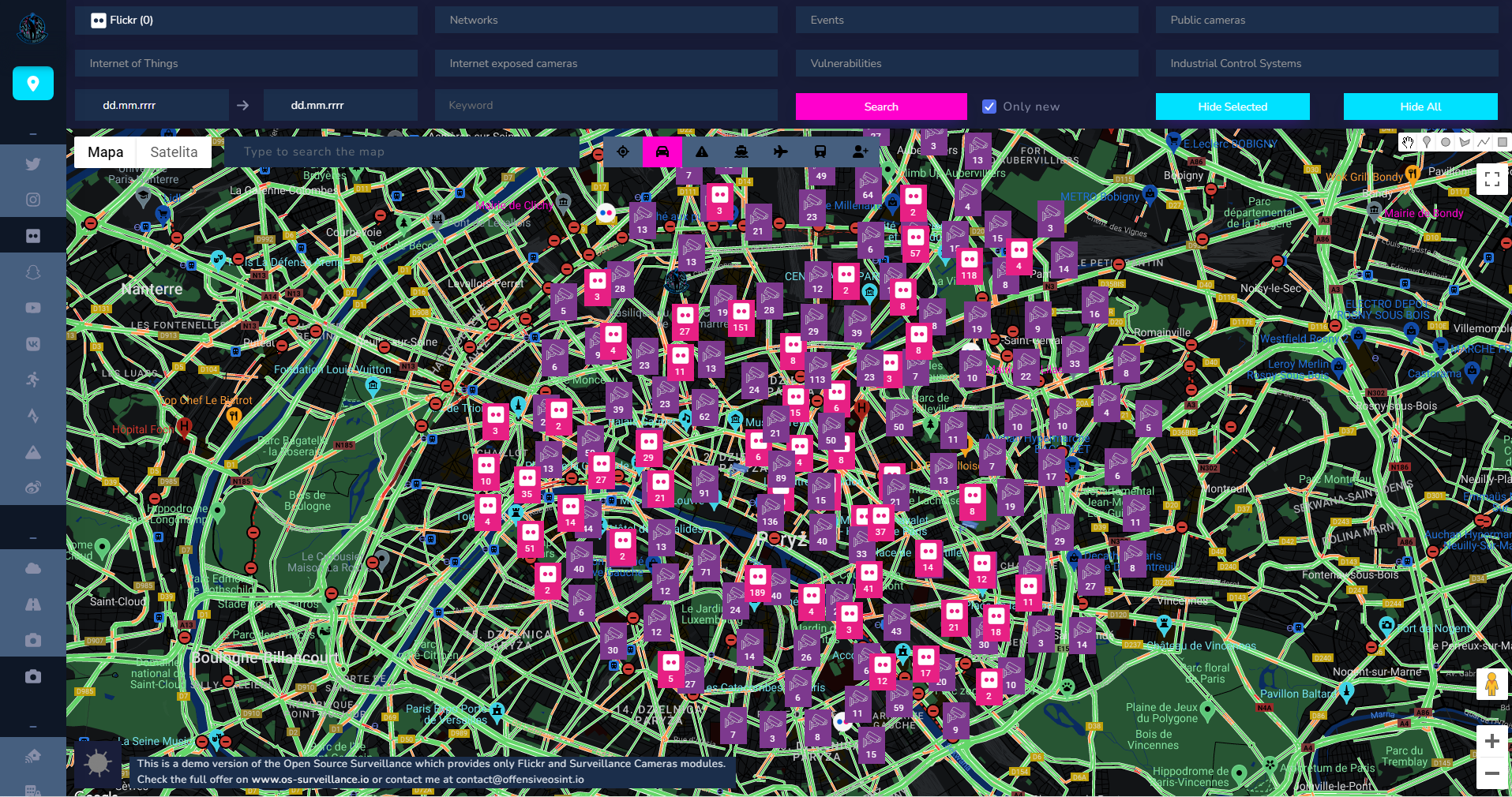
When "Only new" field is marked, then it will ignore findings that are already in database and show only new ones. It was created for monitoring purposes, because every day new new activities on social media appears, and it was to look only for fresh ones.
Then you can look for some places where photos and surveillance cameras have been detected.
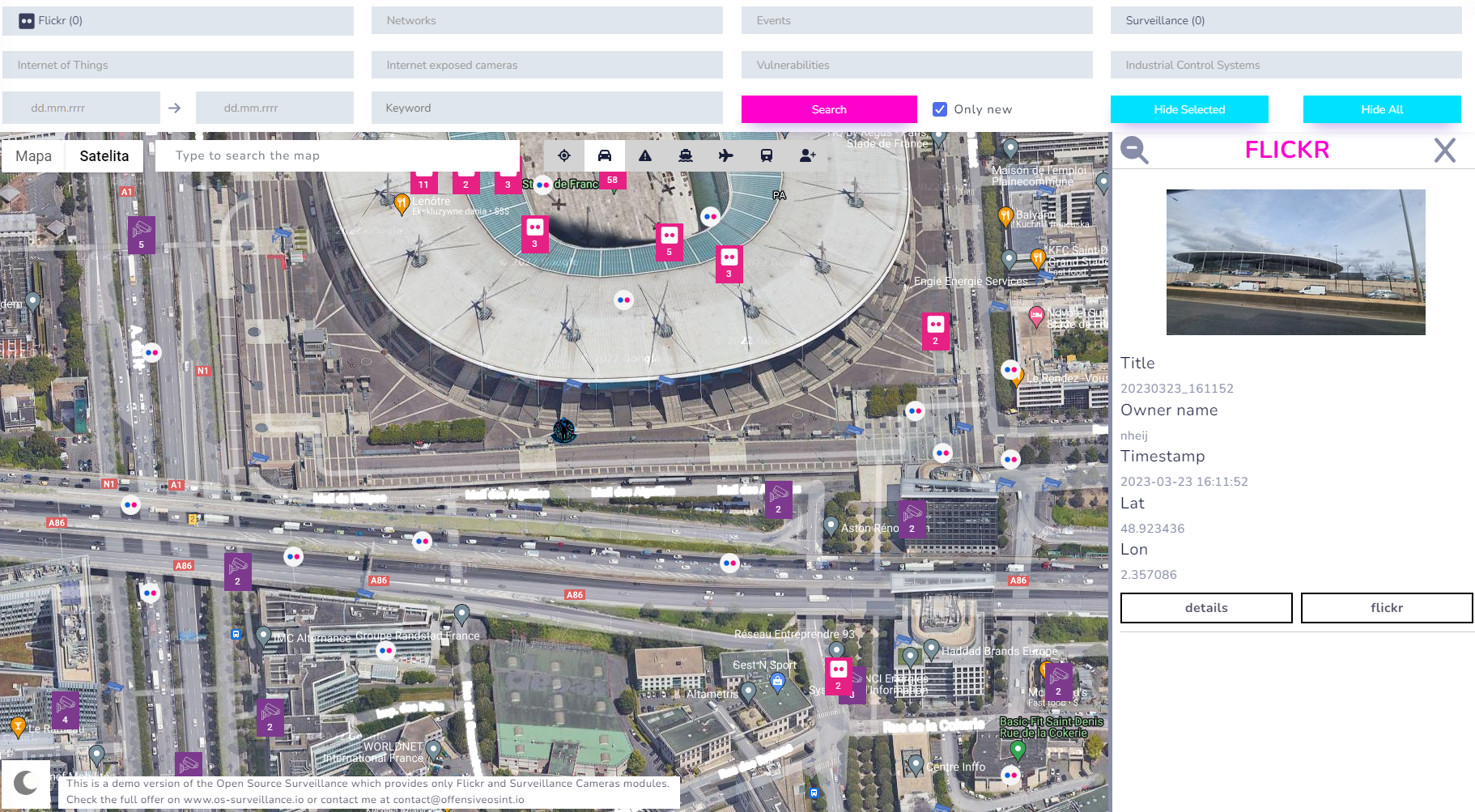
It's worth to add that you have separate view, including statistics, for every category and details about each finding with geolocation as shown below
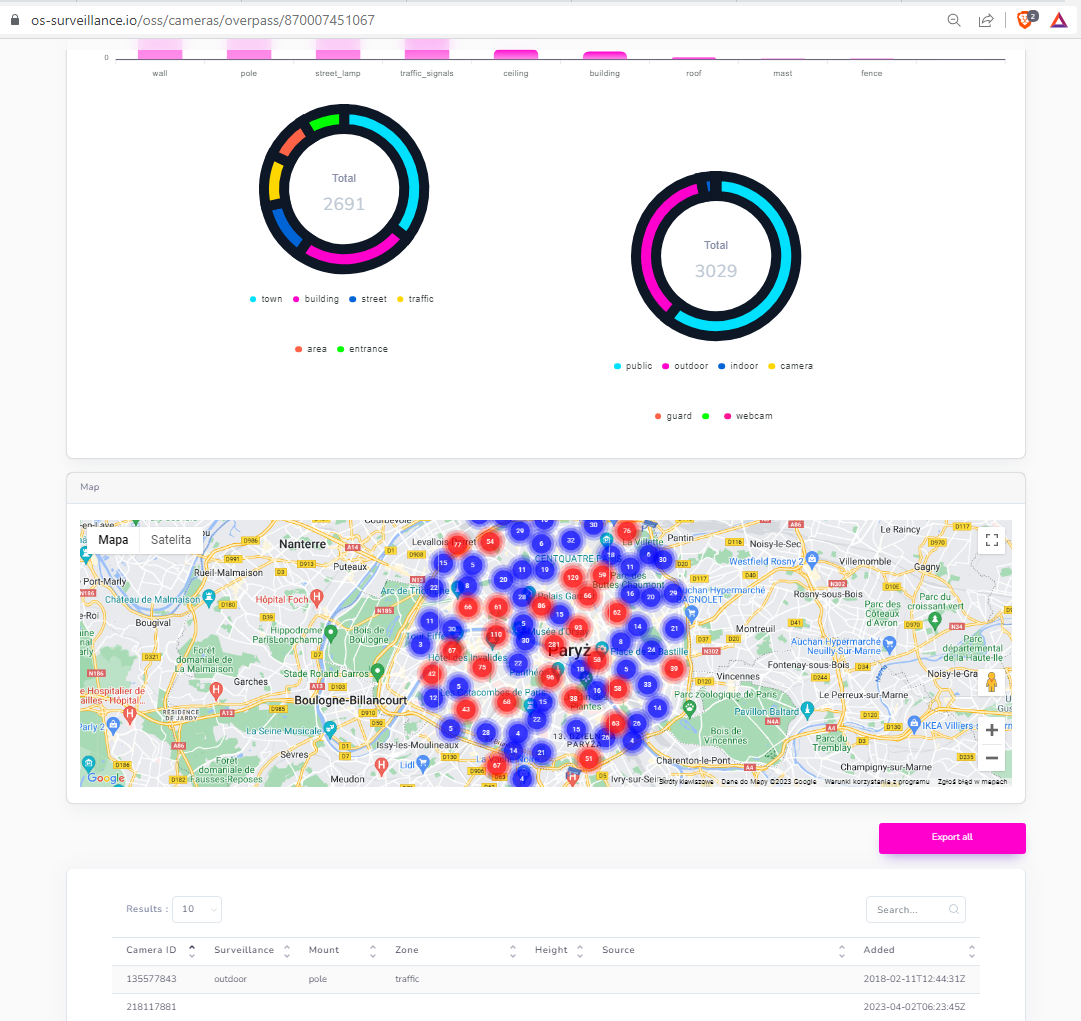
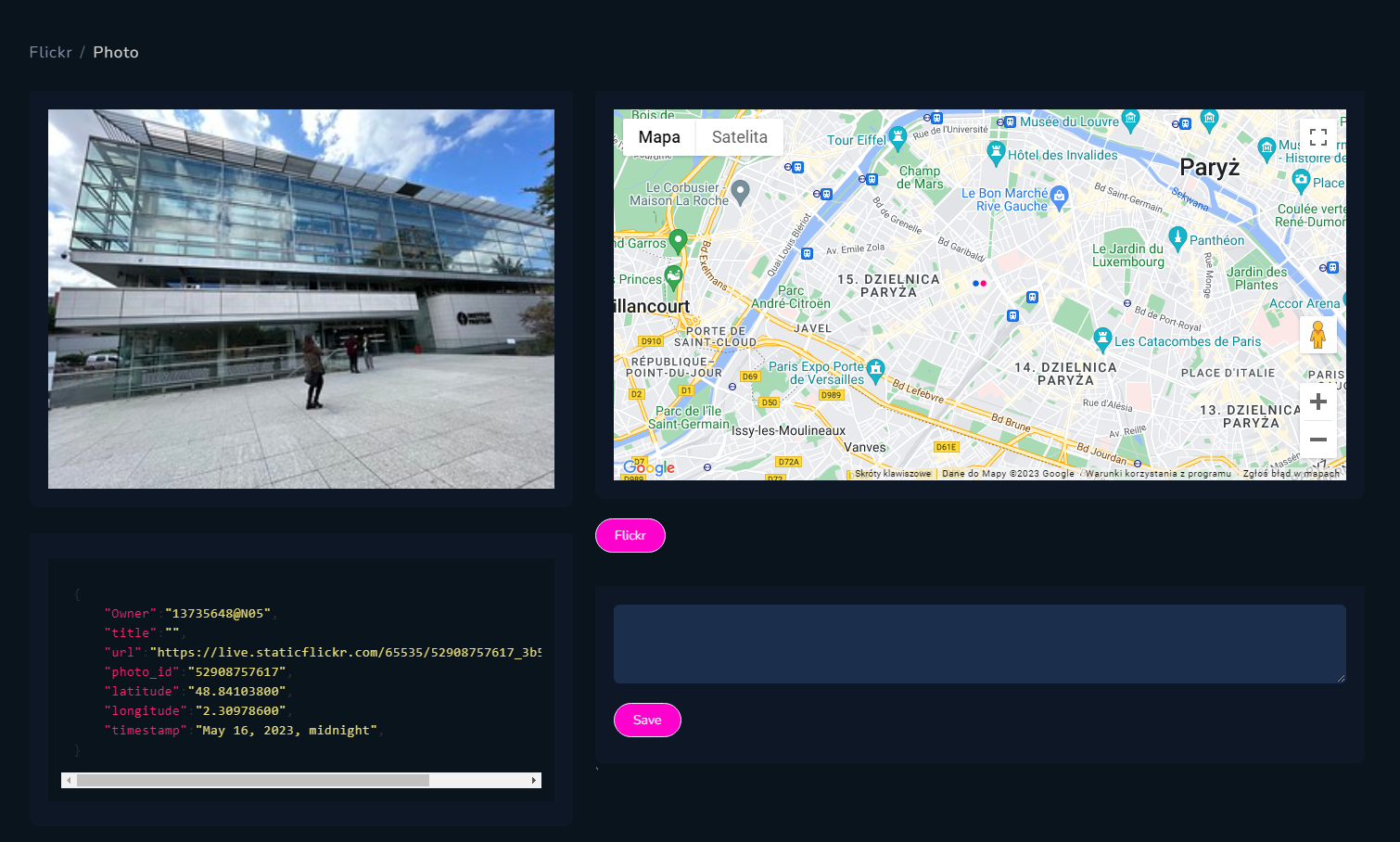
And that's it, you can research whole world with these two modules in demo version.
It looks drastically different when every module was run against this same location
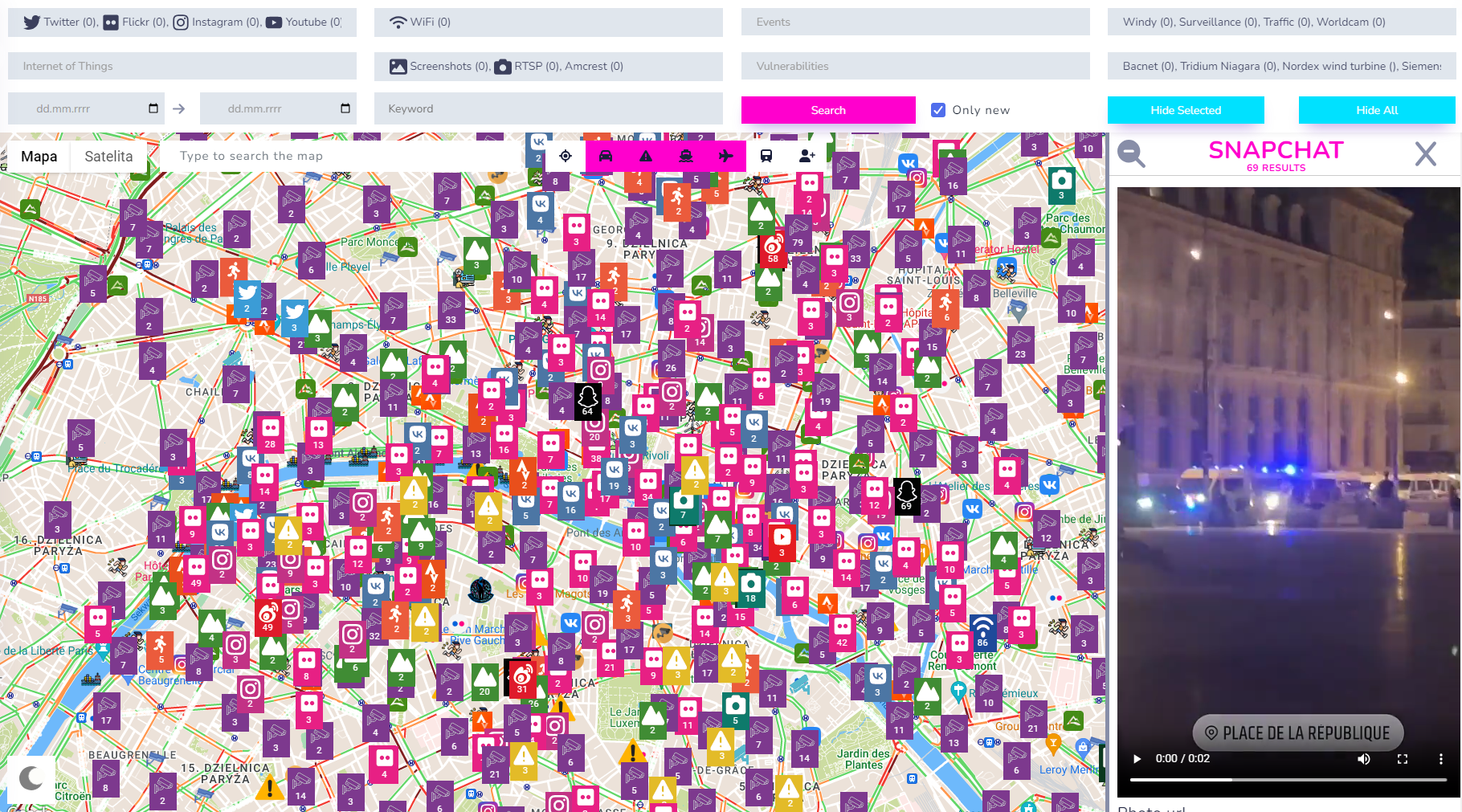
Full version also supports search based on keyword or date range. It makes investigation much easier when looking for events in specific timeframe.
Moreover, some modules like Amber Alerts, Amtrak Trains, Crimes and Traffic Cameras work only for United States, so map can have even more data to investigate.
Next steps
Product is not 100% ready, it needs more work on the frontend as well as improved code on the backend and infrastructure changes, but it's stable, quite fast and reliable, you can always compare results from the tool with original source by directly requesting it, like from Flick Explore feature.
However, until it will be fully ready, I need some feedback from you how to improve it, that's why I decided to publish demo version.
You can sign up for full access by contacting me. Planned release mid September or sooner.







