In this episode we will make an analysis of exposed Industrial Control System (ICS) devices in Russia and United States from military perspective. What is the best way to spy on foreign exposed critical infrastructure? How to do espionage of strategic places? What exploit will be the most profitable? What groups are behind foreign offensive operations? I hope to answer these and other questions in the article.
Last research about Bedpage and human trafficking is accessible from below link

Disclaimer
No device has been hurt during research.
Introduction
We live in interesting times, you can remotely connect to your fridge or start a vacuum from your phone. Nowadays everything goes directly to the Internet even the most fragile devices in different facilities. I have already proofed that you can find and pinpoint buildings and places that are responsible for critical operations for the community.

Damaging these devices might result in interruptions of critical services like electricity, water or waste management. In also concerns government and military facilities, emergency services, transportation services and other mentioned in CISA advisories.
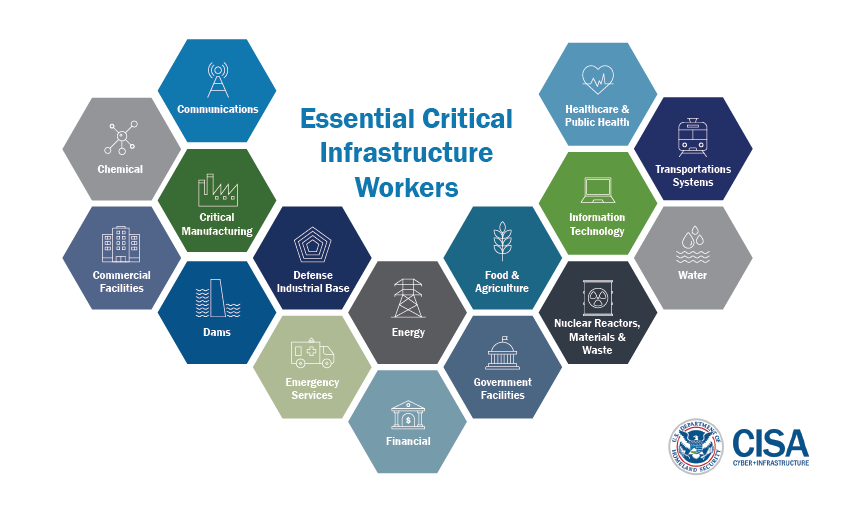
I will share this picture once again, it tells a lot about difficulties in securing whole country and it's critical infrastructure. We have 16 sectors that must to work constantly to provide necessary services and keeping cities and country safe and self-sufficient.
Everything would be perfect if everyone will care of his own country but life is not that easy and unfortunately we see cyber attacks on foreign critical infrastructure. Of course it's not that easy and I have no inside knowledge about reason of the attacks but normal people suffer at the end of the day of this political games.
Russia and United States of America are countries that are known from their offensive activities on foreign critical infrastructure. We will take a look on groups behind the past attacks and later on we impersonate them and examine exposed devices in critical infrastructure of both countries.
self props
NSA and CISA released joint advisory where they mentioned ꓘamerka.
Shodan,[2] Kamerka [3]), are creating a “perfect storm” of 1) easy access to unsecured assets, 2) use of common, open-source information about devices, and 3) an extensive list of exploits deployable via common exploit frameworks

Show of strength
Currently both countries are engaged in offensive cyber operations against themselves and other nations. I strongly suppose that even now Russians might exfiltrate confidential documents from US servers or reverse. Espionage is mostly done via offensive cyber activities and there are thousands cases where someone stole projects, design or secret documents from the enemy.
In the past both countries conducted offensive cyber operations regarding critical infrastructure in foreign countries.
United States of America
Major organizations responsible for US national security are Central Intelligence Agency (CIA), National Security Agency (NSA, also known as Equation Group), United States Cyber Command (USCYBERCOM) and Cybersecurity & Infrastructure Security Agency (CISA) which takes care of protecting domestic assets. In addition their offensive capabilities are backed up by Israel or The Netherlands. They usually get a green light for different offensive operations according Forbes report.
The secret authorization — issued sometime in 2018 — offered the U.S. spy agency more freedom to both conduct cyber operations and choose its target, without the White House’s approval, the report said. - https://www.forbes.com/sites/siladityaray/2020/07/15/report-cia-conducted-cyber-attacks-against-iran-russia-after-secret-trump-order-in-2018/#62ccf1304600
Additional source revealed insight about this operations for New York Times.
“It has gotten far, far more aggressive over the past year,” one senior intelligence official said, speaking on the condition of anonymity but declining to discuss any specific classified programs. “We are doing things at a scale that we never contemplated a few years ago.” - https://www.nytimes.com/2019/06/15/us/politics/trump-cyber-russia-grid.html
The biggest publicly disclosed cyber operation made by United States on foreign critical infrastructure is of course Stuxnet. There are plenty of articles about this attack and one of the most interesting ins accessible below
https://ccdcoe.org/uploads/2018/10/Falco2012_StuxnetFactsReport.pdf
Obviously, they have to defend their own critical infrastructure from enemies, which constantly tries to break in different networks and perform espionage activities. It's known that Iran, North Korea, China and Russia conducted hacking operations against United States and what's more, some of them touched critical infrastructure. I will just present couple quotes about the adversaries and their capabilities to damage US infrastructure.
China has the ability to launch cyber attacks that cause localized, temporary disruptive effects on critical infrastructure—such as disruption of a natural gas pipeline for days to weeks—in the United States.
Russia has the ability to execute cyber attacks in the United States that generate localized, temporary disruptive effects on critical infrastructure—such as disrupting an electrical distribution network for at least a few hours—similar to those demonstrated in Ukraine in 2015 and 2016. Moscow is mapping our critical infrastructure with the long-term goal of being able to cause substantial damage.
Iran uses increasingly sophisticated cyber techniques to conduct espionage; it is also attempting to deploy cyberattack capabilities that would enable attacks against critical infrastructure in the United States and allied countries.
These words come from Worldwide Threat Assessment published by the US Intelligence Community.
https://www.dni.gov/files/ODNI/documents/2019-ATA-SFR---SSCI.pdf
One of the example of such attack could be network breach of Wolf Creek Nuclear Operating Corporation, based in Kansas or incident in Rye Brook Dam in New York.


However actors did not reach the critical devices itself but they had a capability to perform such attacks. In second case, Russians gained access via spear phising with fake resumes.
Russian Federation
Russia has many groups specialized in different field of cyber espionage and offensive operations. Some of them work exclusively on disinformation, psychological operations, election influence or hacking private corporations and government organizations. Regarding critical infrastructure, the ones we know are Dragonfly, Berserk Bear (aka Dragonfly 2.0), Allanite (Palmetto Fusion), Energetic Bear, Sandworm (ELECTRUM), Xenotime(?) and to protect GosSOPKA has been established. Each of this group is described in details by Dragos
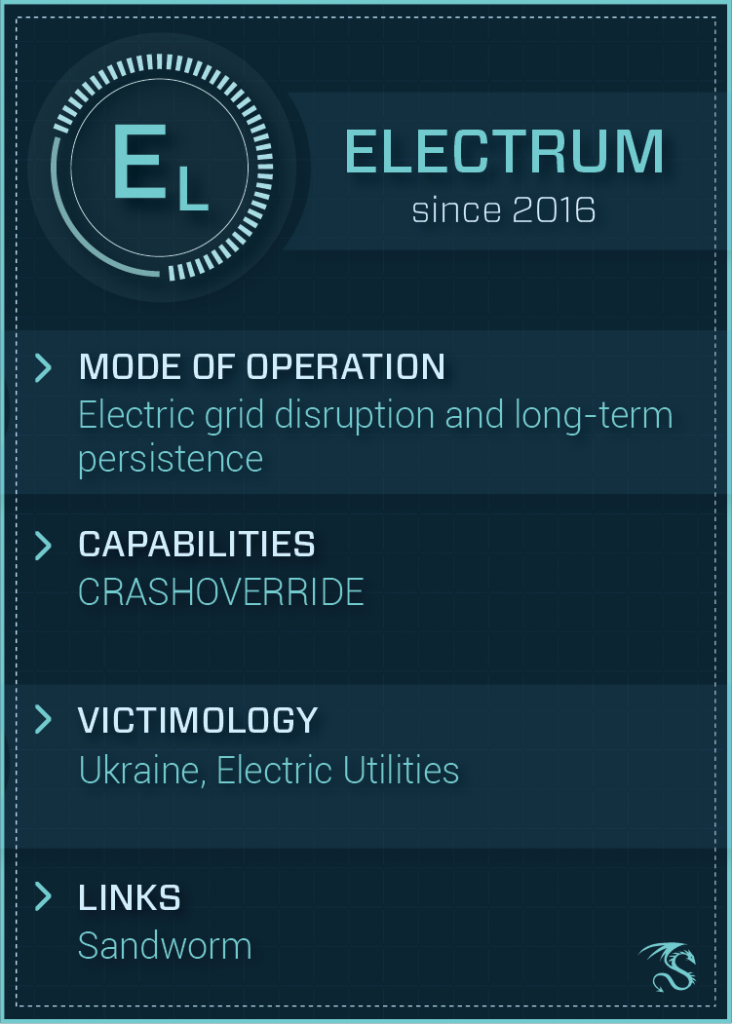
They proved their offensive cyber capabilities causing blackout in Ukraine - in 2015 and 2016, and (according Crowdstrike) attacking petrochemical plant in 2017 in Saudi Arabia. They have been connected to tools like CRASHOVERRIDE (INDUSTROYER), TRITON (TRISIS), BLACKENERGY or HAVEX.
You can read full insight into CRASHOVERRIDE below
https://www.dragos.com/wp-content/uploads/CRASHOVERRIDE.pdf
The Ukrainian power grid incident, in my opinion, is the biggest achievement for Russian state sponsored hackers targeting critical infrastructure. Around 230 thousands of people had no electricity for period from 1 to 6 hours. After deeper investigation it turned out that they wanted to make a blackout that would last weeks or months. Some people think that Ukraine is just a playground for Russian groups and they were testing their methodology and tools to catch a bigger fish later, i.e. attack on US energy infrastructure.
Another significant cyber operation took place in undisclosed period
Hackers working for Russia claimed “hundreds of victims” last year in a giant and long-running campaign that put them inside the control rooms of U.S. electric utilities where they could have caused blackouts, federal officials said. They said the campaign likely is continuing.
The Russian hackers, who worked for a shadowy state-sponsored group previously identified as Dragonfly or Energetic Bear, broke into supposedly secure, “air-gapped” or isolated networks owned by utilities with relative ease by first penetrating the networks of key vendors who had trusted relationships with the power companies, said officials at the Department of Homeland Security.
“They got to the point where they could have thrown switches” and disrupted power flows, said Jonathan Homer, chief of industrial-control-system analysis for DHS. - https://www.wsj.com/articles/russian-hackers-reach-u-s-utility-control-rooms-homeland-security-officials-say-1532388110
In addition
Then they began stealing confidential information. For example, the hackers vacuumed up information showing how utility networks were configured, what equipment was in use and how it was controlled. They also familiarized themselves with how the facilities were supposed to work, because attackers “have to learn how to take the normal and make it abnormal” to cause disruptions, said Mr. Homer. - https://www.wsj.com/articles/russian-hackers-reach-u-s-utility-control-rooms-homeland-security-officials-say-1532388110
Their activities does not end on US, they attack almost any of their 'enemies' to gather data about how specific devices work or general infrastructure plans. I think that every country is afraid of potential damage that any of these groups can cause to critical infrastructure. Couple months ago German intelligence warned about Russians attempts to threat to critical infrastructure.

Also CISA warns of Russian groups that target critical infrastructure sectors.

From other side I haven't heard about any publicly disclosed attacks that would cause disruption of infrastructure in Russian Federation. From previously linked article we know that US got approval for their operations and allegedly plant cyber-time bombs in critical infrastructure in Russia but both of the parties remain silent about it except one statement that I was able to find.
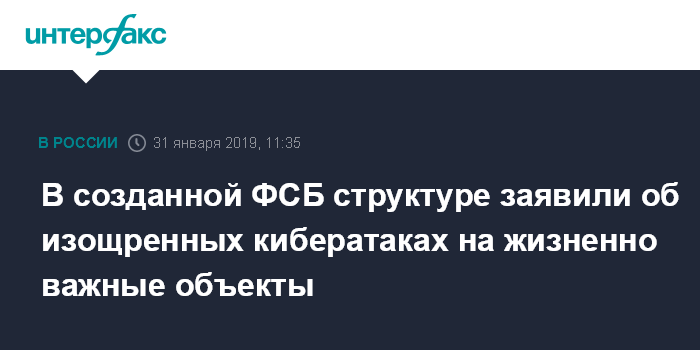
“Practically all major computer epidemics of the last decade have affected our country. In addition, Russian information systems, primarily critical infrastructure, are subject to sophisticated and targeted attacks from abroad,” Murashov said during his speech at Infoforum-2019. In his opinion, this is "the reverse side of total informatization." - https://translate.google.com/translate?hl=&sl=auto&tl=en&u=https%3A%2F%2Fwww.interfax.ru%2Frussia%2F648542
They also have a significantly smaller amount of exposed ICS devices to the Internet but it's not a factor that makes attacks harder. However, most energy grid substations in Russia work manually so it is nearly impossible to remotely cause service disruptions. Only big cities like Moscow or ST Petersburg uses newer more automated solutions.
After this a quite long introduction of both groups, we can move on to the actual research about exposed devices.
Disclaimer
I am aware that hacking critical infrastructure is process that takes months or even years. Same with espionage, it is constant passive and active observation of satelite images, discovering networks or preparing exploits.
My research is limited to show Internet facing devices that might be located in critical infrastructure and exposed valuable information that might be used in later stage of the attack.
Methodology
Research focuses on Initial Access according to MITRE ATT&CK® for Industrial Control Systems and on following techniques:
Sandworm actors exploited vulnerabilities in GE's Cimplicity HMI and Advantech/Broadwin WebAccess HMI software which had been directly exposed to the internet.
It often happens that additional services are running on the server that operates industrial device. Different kind of VPNs, Remote Desktop Protocols and other that might be vulnerable and used to gain initial access.
XENOTIME utilized remote desktop protocol (RDP) jump boxes to move into the ICS environment
BAD RABBIT can utilize exposed SMB services to access industrial networks
Everything has been done with help of ꓘamerka GUI which allows to scan for Internet exposed devices, locate them and gather other information.
ꓘamerka supports around 110 ICS, 80 medical and 25 IoT devices. I collected information on ~83k devices in United States and ~15k in Russia.
You can find fork of the tool somewhere in the github or dm me for access to private repository.
Internet exposed devices in critical infrastructure in United States of America and Russian Federation
We know about offensive capabilities and operations conducted by both countries but espionage techniques are always kept in secret. Different agencies focus on satellite images, network reconnaissance and maybe there is also part to check for exposed devices and target ones that are located in critical infrastructure.
First, lets take a look on the map with exposed devices and compare both countries in this aspect.
ꓘamerka detected ~4,5k exposed devices in Russia.
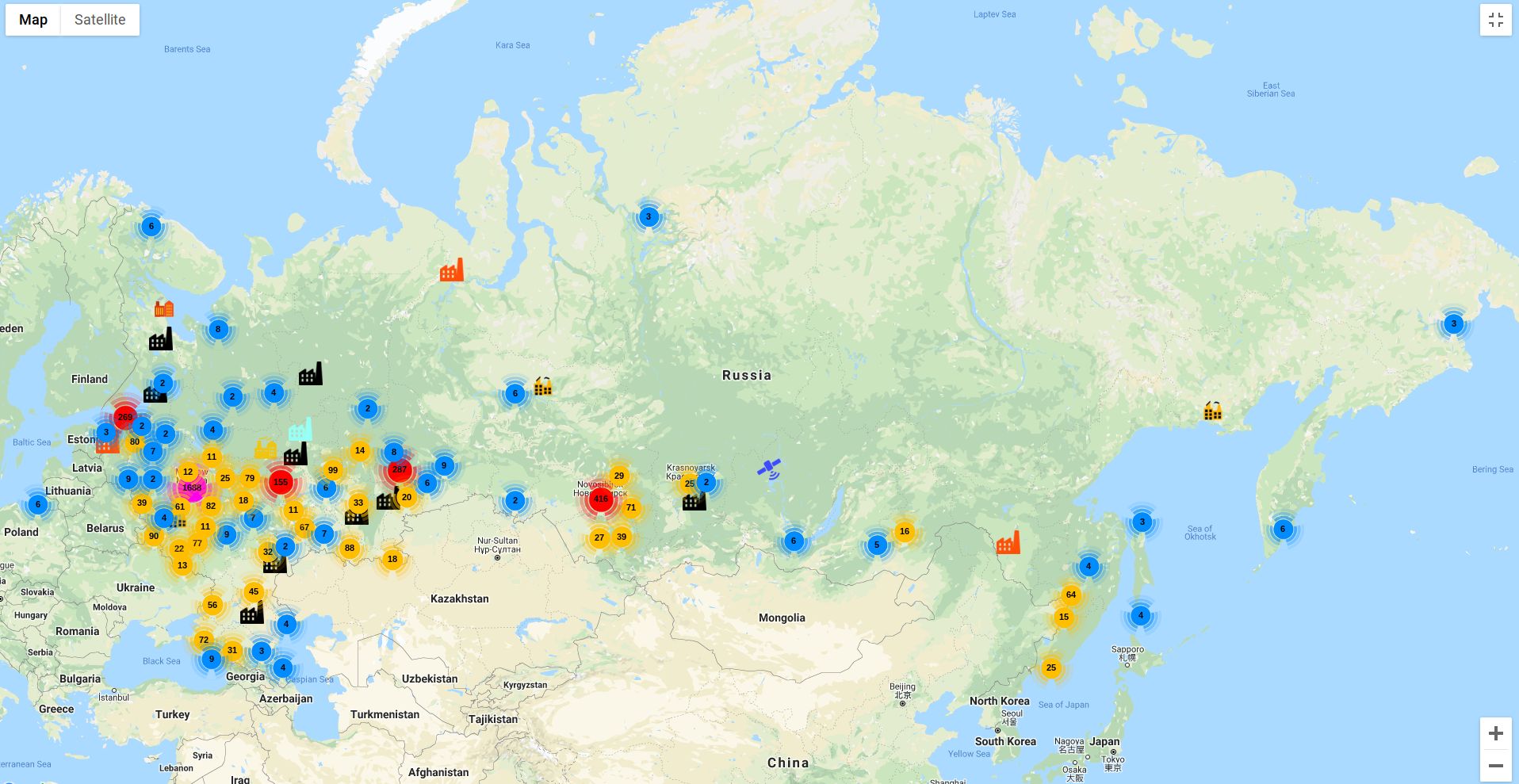
Results in Russia are not accurate for some devices, there are plenty of honeypots.
and ~83k in United States of America.
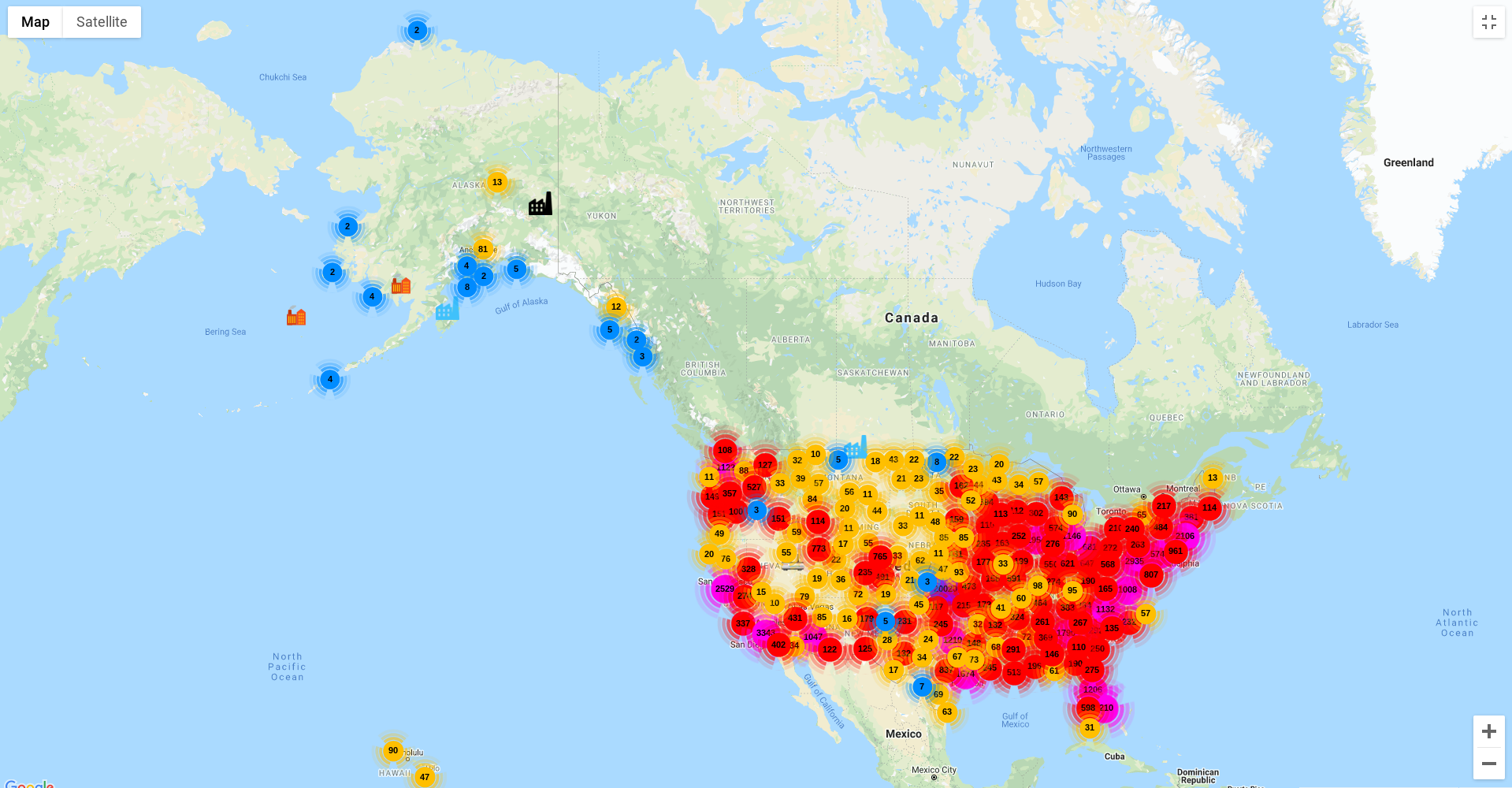
ꓘamerka is device oriented rather than host, it means it detects any potential devices on each machine. For example if on one machine port 1911 (Niagara Fox) and 4911 (Niagara Fox Secure) and 47808 (BACnet) operates, ꓘamerka detects it as 3 different devices running on the machine.
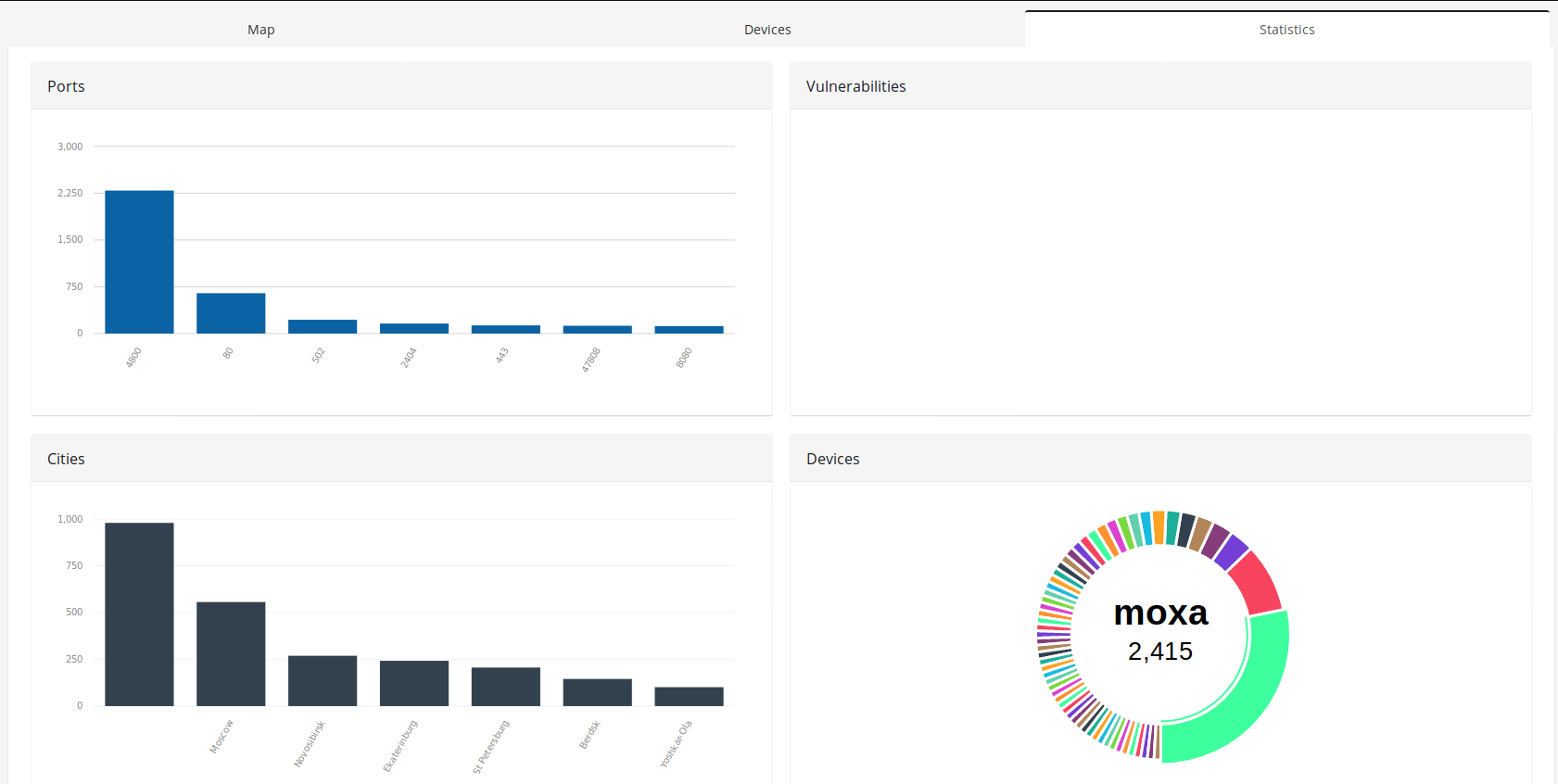
The most used devices in Russia are Moxa (2415) Moxa HTTP panel (713), Modbus (205), IEC (160) and BACnet (124).
As stated before, there is no way to state precise amount of exposed devices in Russia without time consuming review and exclude honeypots.
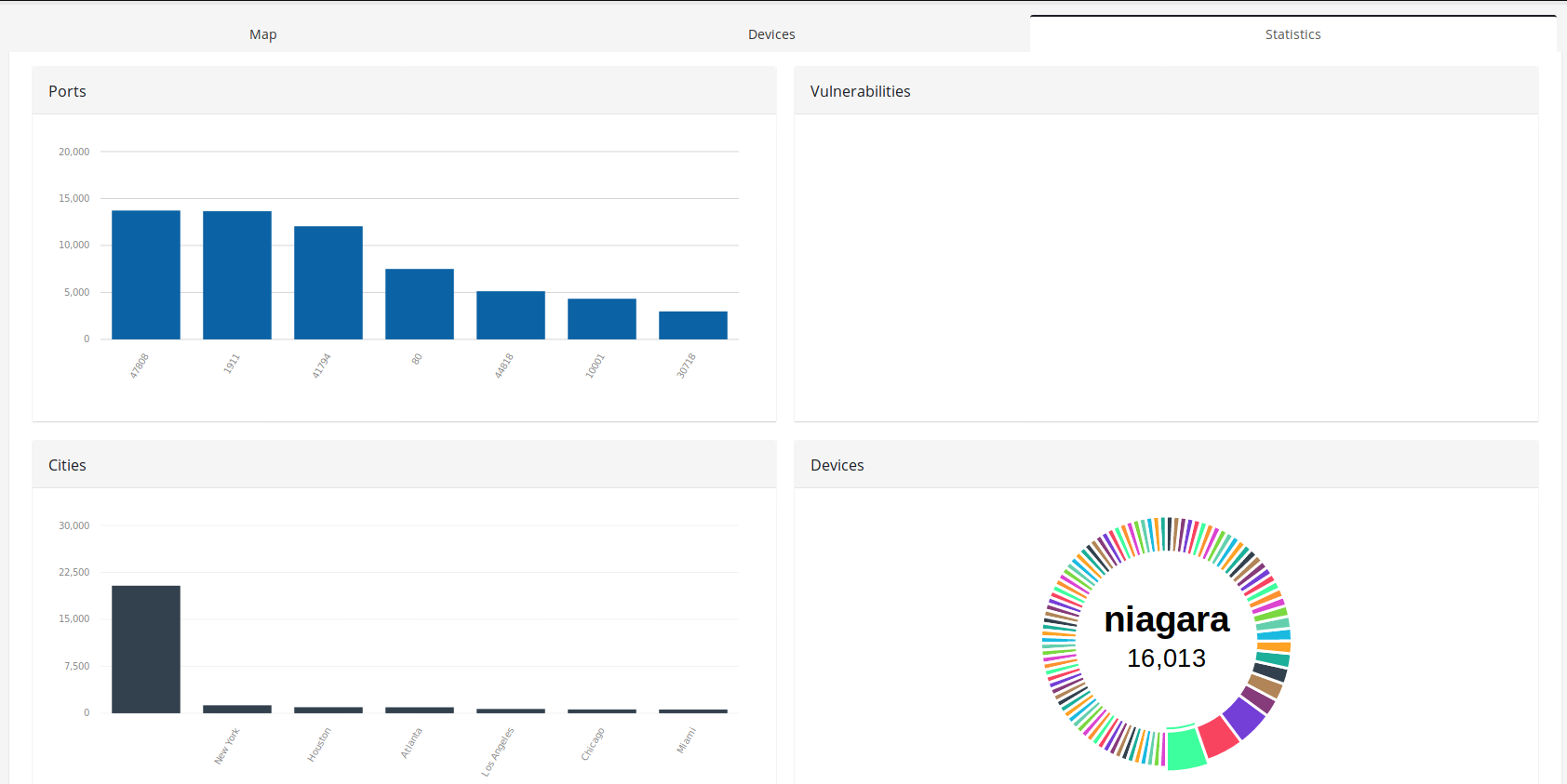
In United States, the most popular exposed devices are Niagara Fox (16013), Crestron (14596), BACnet (13721), Lantronix (5196) and EthernetIP (5121)
I did examine big majority of these devices and was able to find examples that operate in critical infrastructure and compromising them might be problematic for national security.
Transportation sector
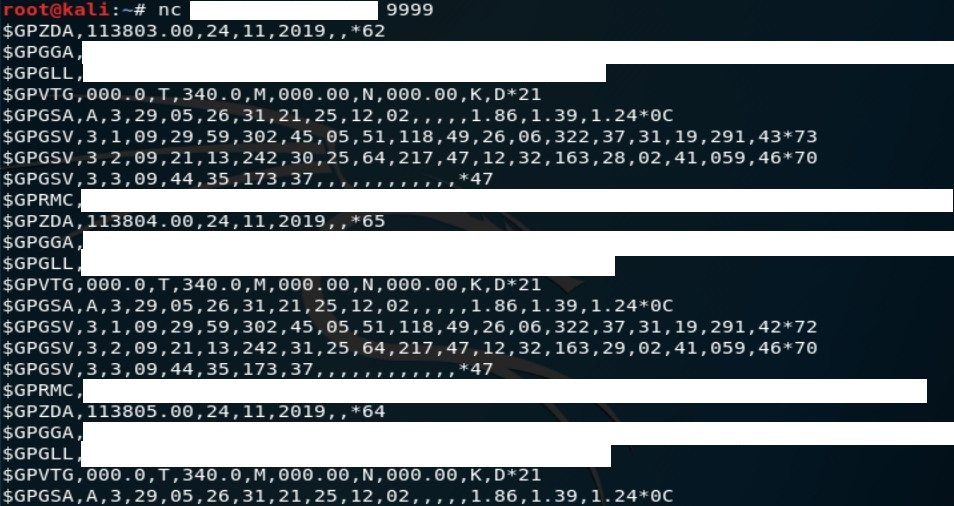
First thing I want to present is NMEA (National Marine Electronics Association) protocol that points to strategic places. It is mostly used to provide communication between marine electronics like autopilots or GPS receivers but it is also used in land in transportation sector.
Query: $GPGGA
United states
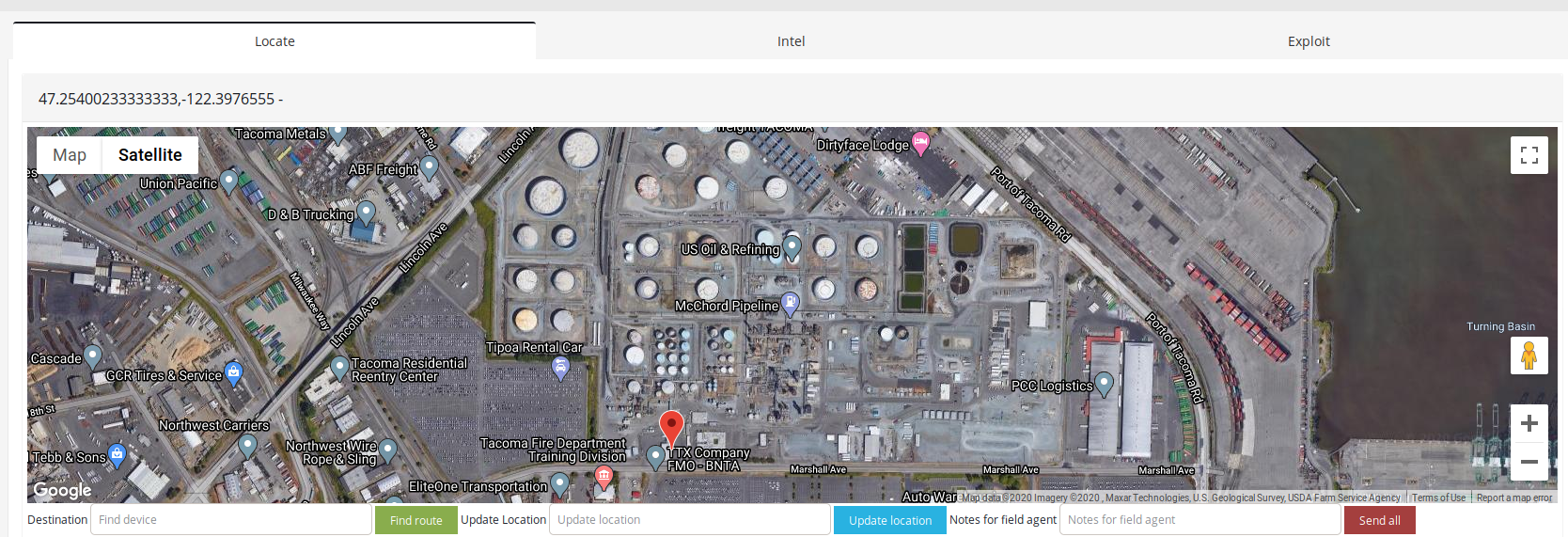
- US Oil & Refining, Tacoma, Washington
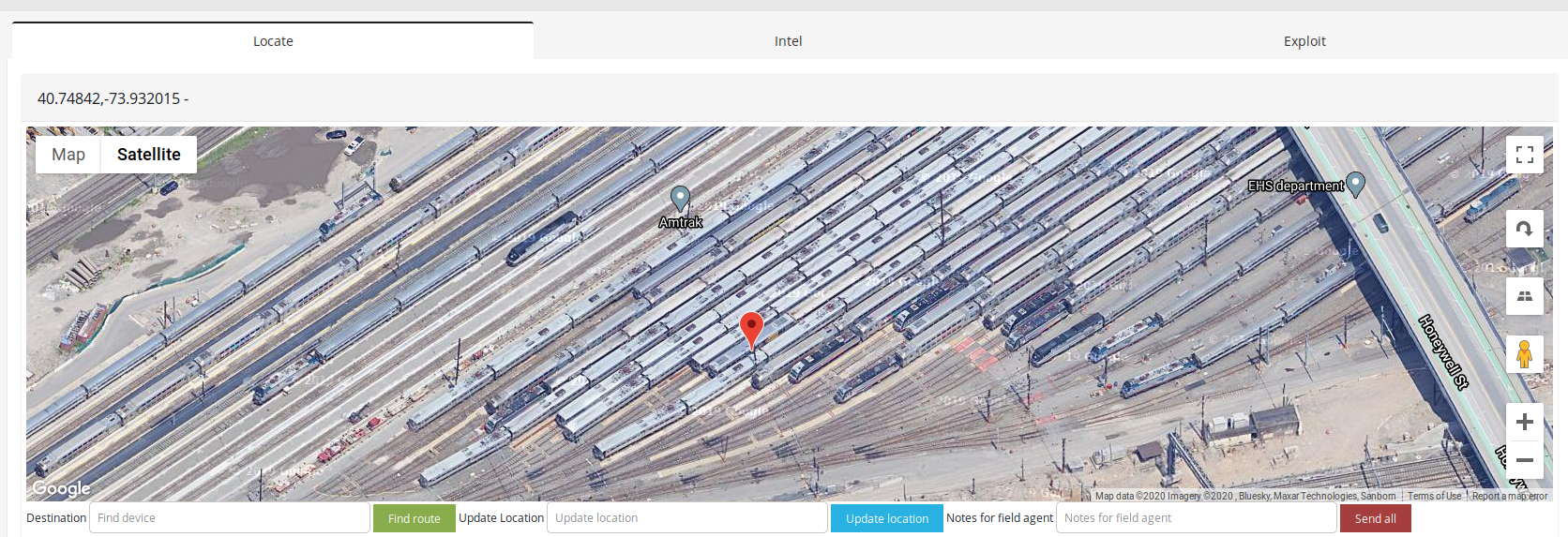
- Amtrak Railroads, New York
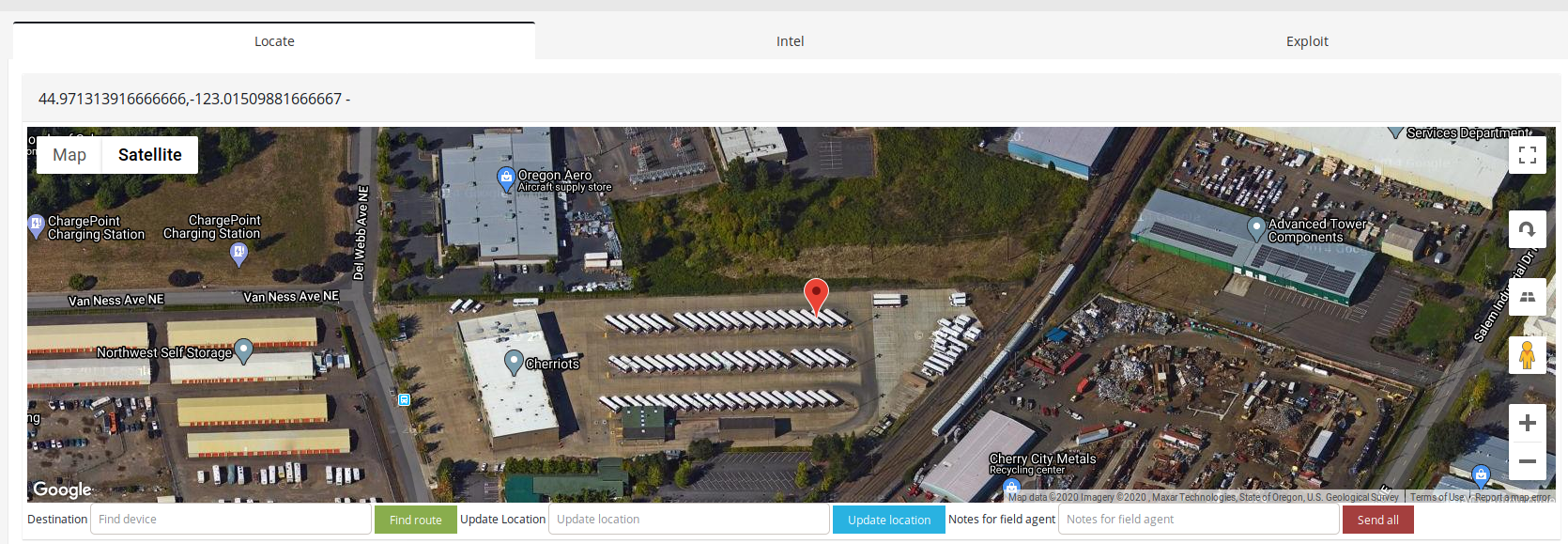
- Cherriots parking lot, Salem, Oregon
- Unspecified building, Pleasure Point, California
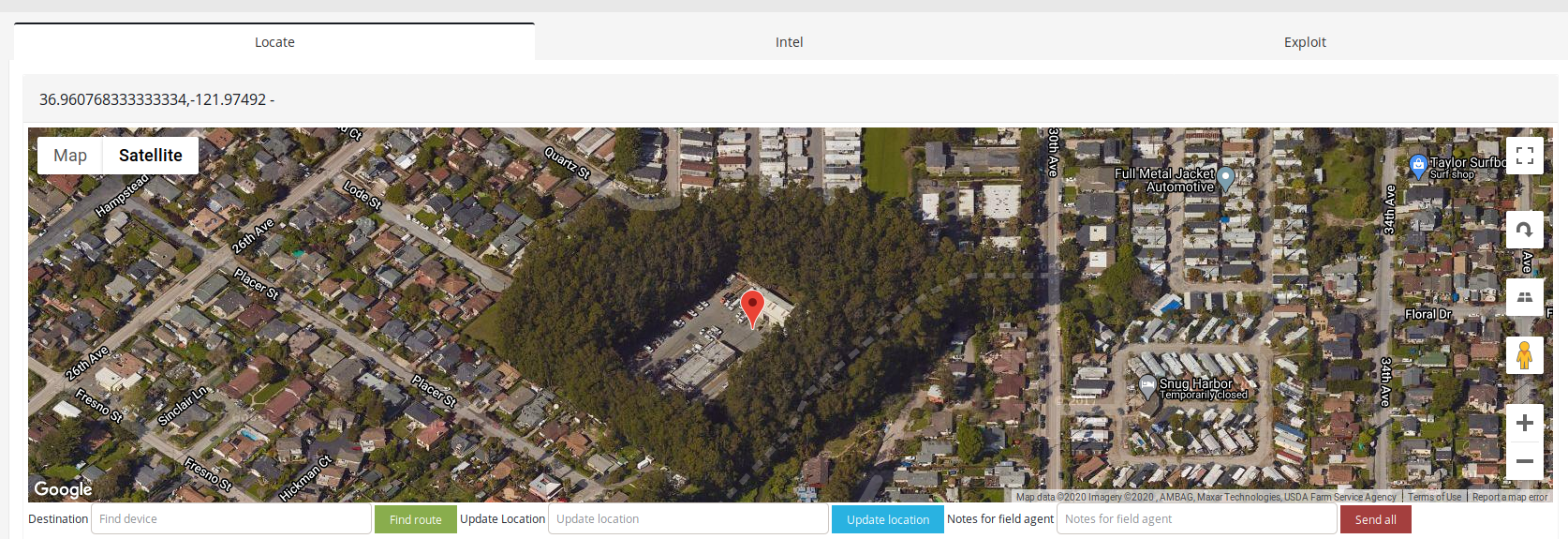
There are 101 devices operating NMEA protocol in United States pointing to exact spots like fire departments, parking lots, bay and other.
Russia
There are only 6 devices using NMEA in Russia which point to random places with no actual value for intel gathering.
- Zhilotkovo, random place
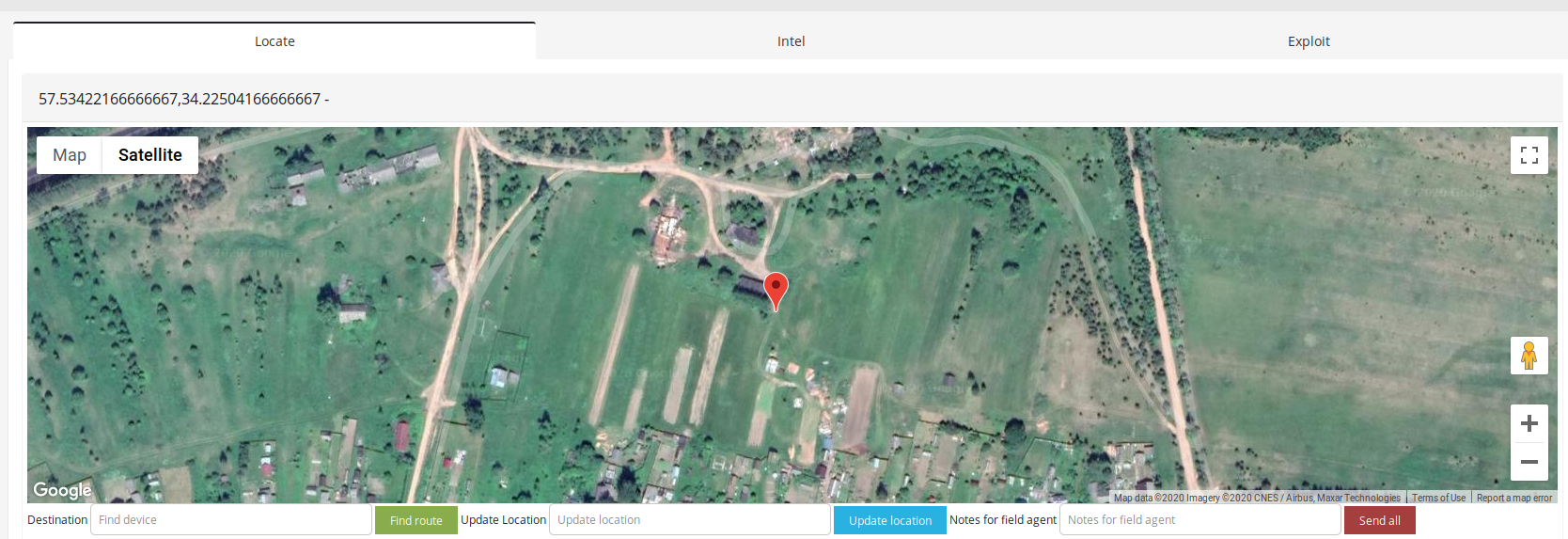
- Rostov na donu, unspecified building
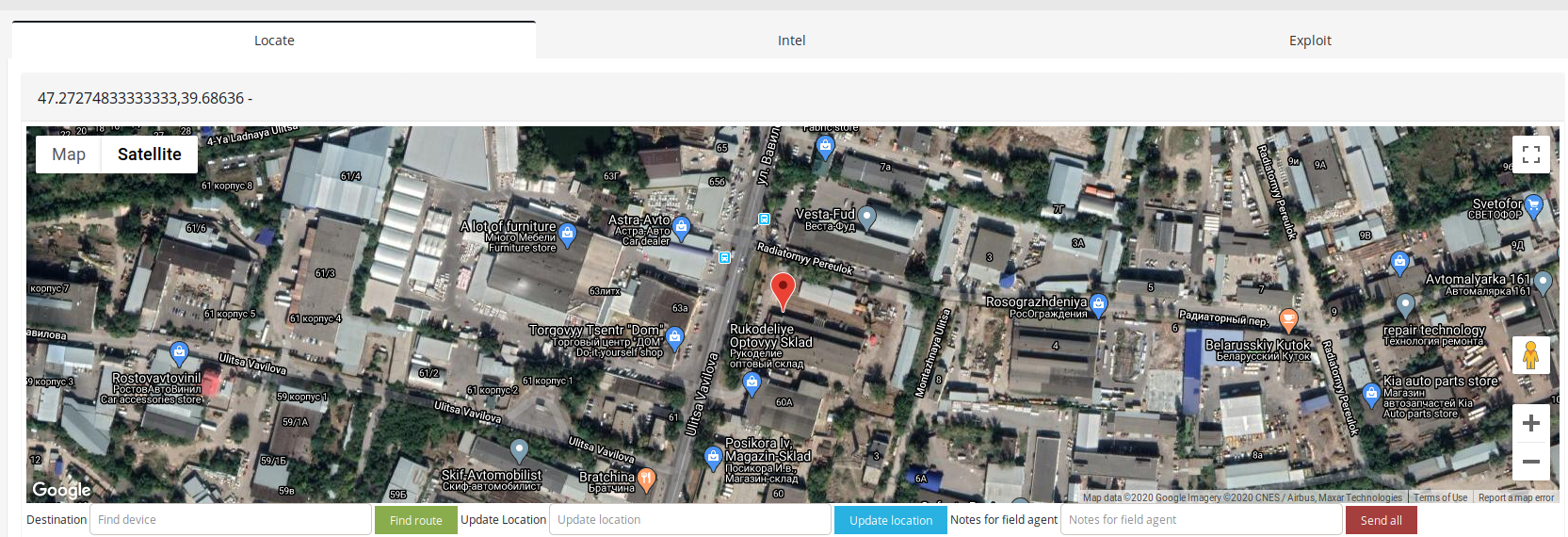
Why is this important? Because in some cases you can connect to the device and if it supports input mode you can tamper the data.

Exposed Human Machine Interface & Meters
HMIs are treasure trove for of information about device itself and how facility works. Collected data can be used for spearphishing, gaining direct access or getting acquainted with infrastructure.
According MITRE ATT&CK® for Industrial Control Systems, Screen Capture were used by Dragonfly, APT33 and ALLANITE during collection process.
Adversaries may attempt to perform screen capture of devices in the control system environment. Screenshots may be taken of workstations, HMIs, or other devices that display environment-relevant process, device, reporting, alarm, or related data. These device displays may reveal information regarding the ICS process, layout, control, and related schematics. In particular, an HMI can provide a lot of important industrial process information. Analysis of screen captures may provide the adversary with an understanding of intended operations and interactions between critical devices.
Other relevant aspect of gathering information from HMIs is using the information for spearphishing. If you can build trust with recipient and give him real insider information then it will be more probably he will open malicious attachment. This method is one of the most common to gain initial access and was used by many APT including ones that target critical infrastructure.
In addition, alerts from US CERT describe case when attackers were looking, accessed and made screenshots of HMIs.

The threat actors targeted and copied profile and configuration information for accessing ICS systems on the network. DHS observed the threat actors copying Virtual Network Connection (VNC) profiles that contained configuration information on accessing ICS systems. DHS was able to reconstruct screenshot fragments of a Human Machine Interface (HMI) that the threat actors accessed.
United States
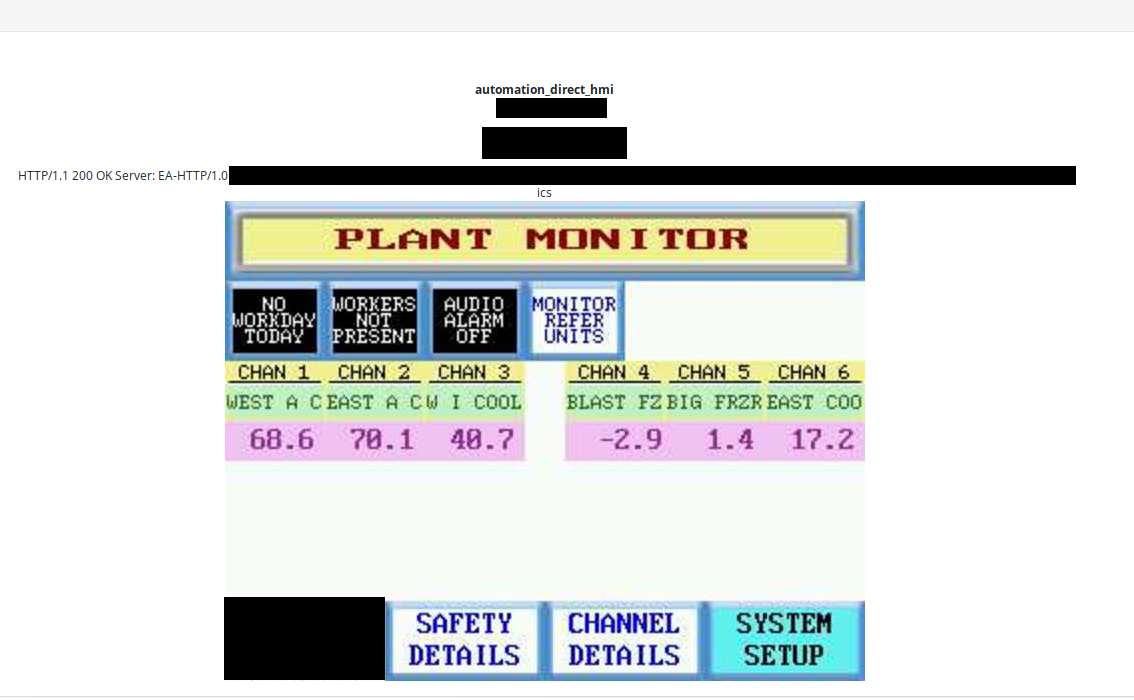
Unfortunately there are still plenty of Internet facing Human Machine Interface operating in different sectors. The most popular one is Automation Direct and if not properly secured it exposes screens and possibility to remote connection.
- Exposed passwords (PIN codes) in Plant monitor system, unknown location
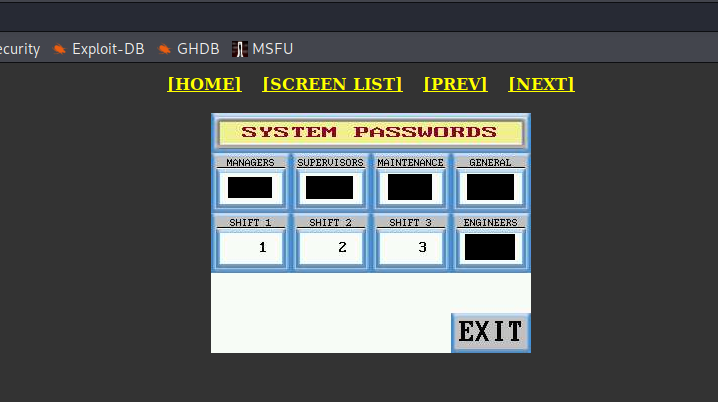
- Exposed email addresses in HMI
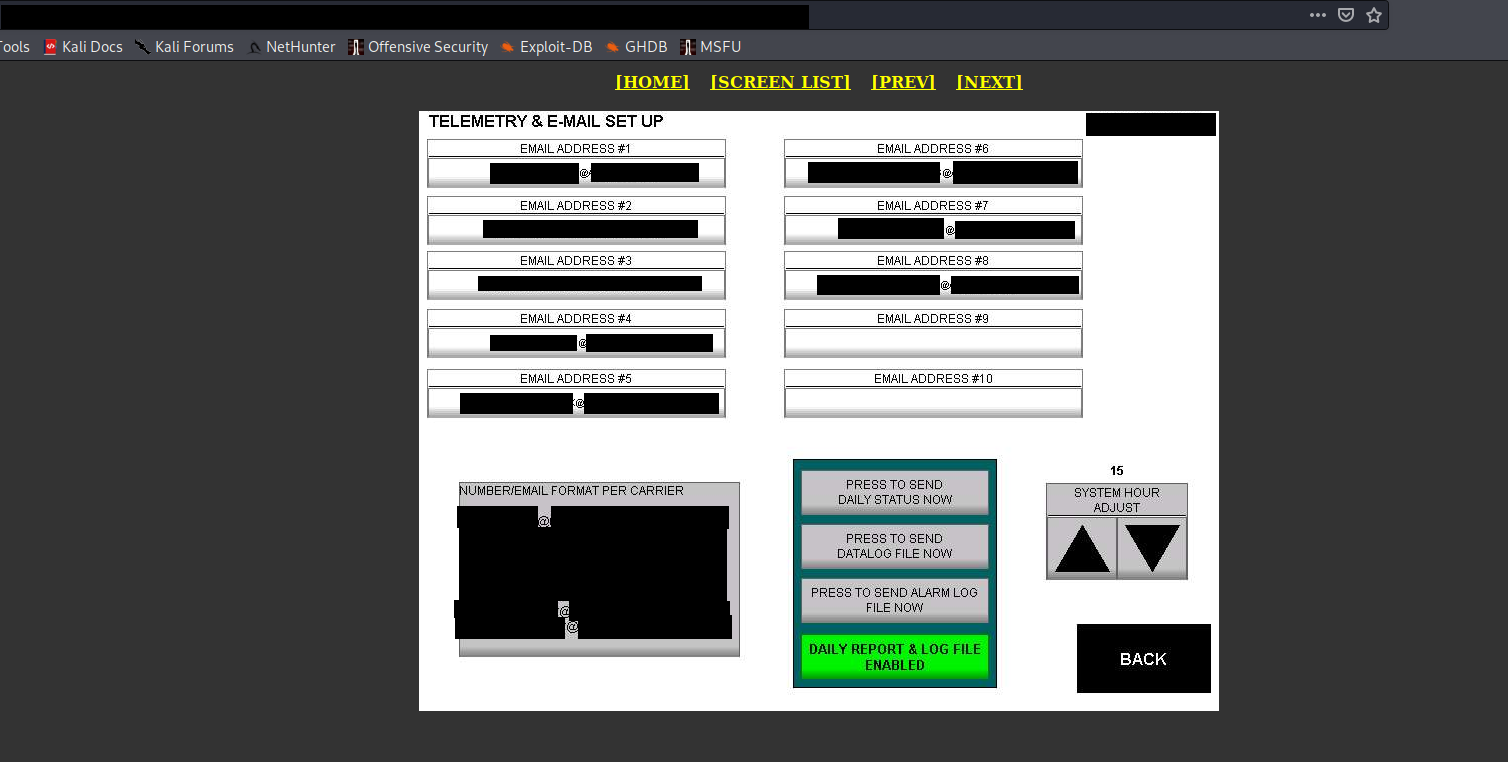
That's also kind of things that APTs look for. Perfect possibility to phishing when you have a passwords or email addresses to convince recipient or impersonate someone whom he trusts.
As stated before, almost any sector is affected and expose at least one device to the Internet.
- Waste Water Treatment Plant, Camden, New York
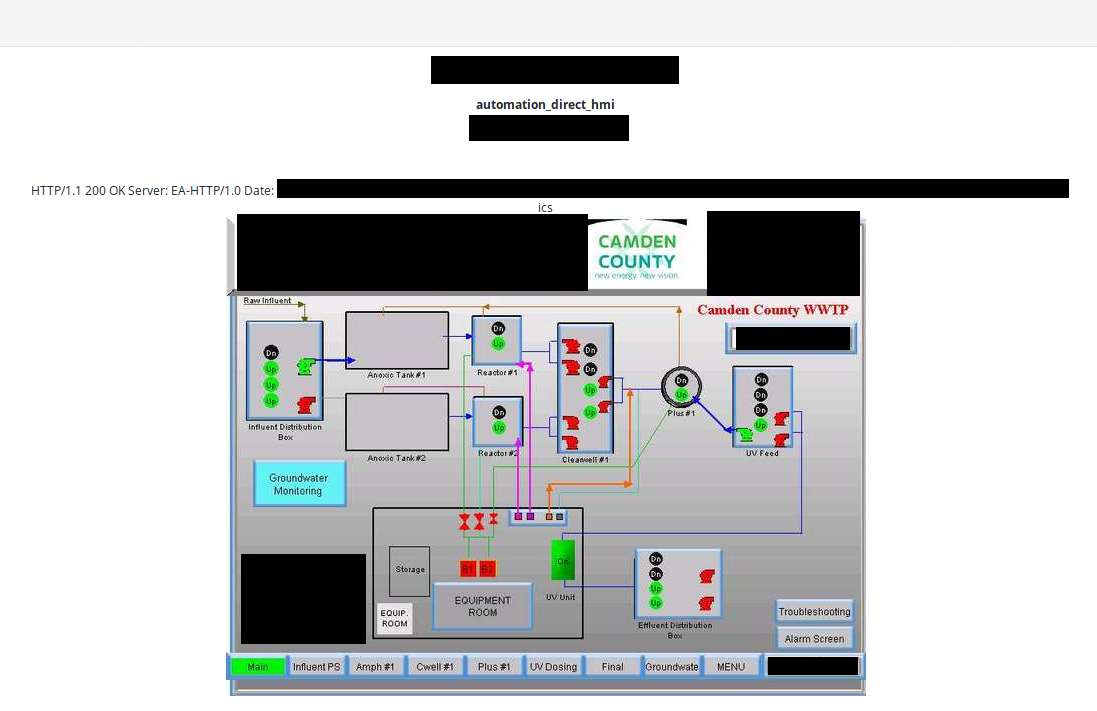
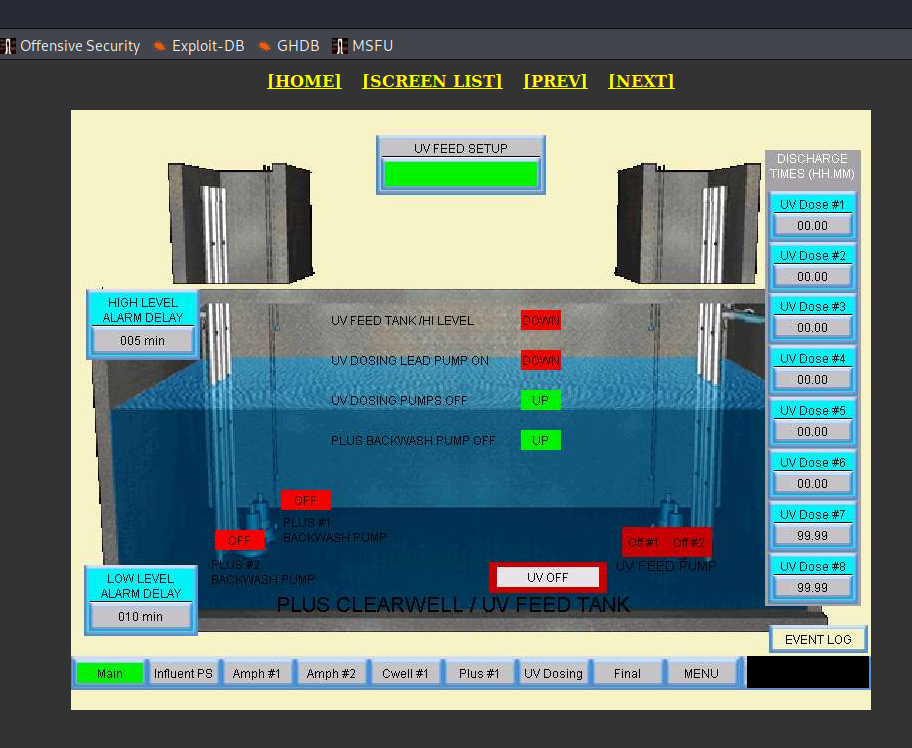
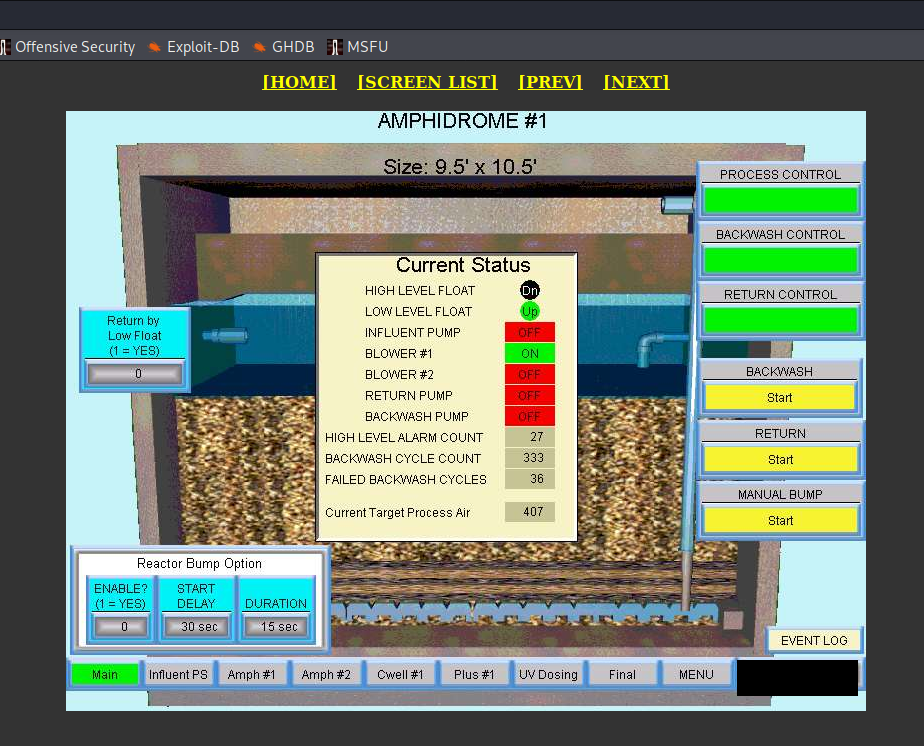
Based on the diagram, I think it might be exact place where device is located or responsible for operating. It's beautiful facility.
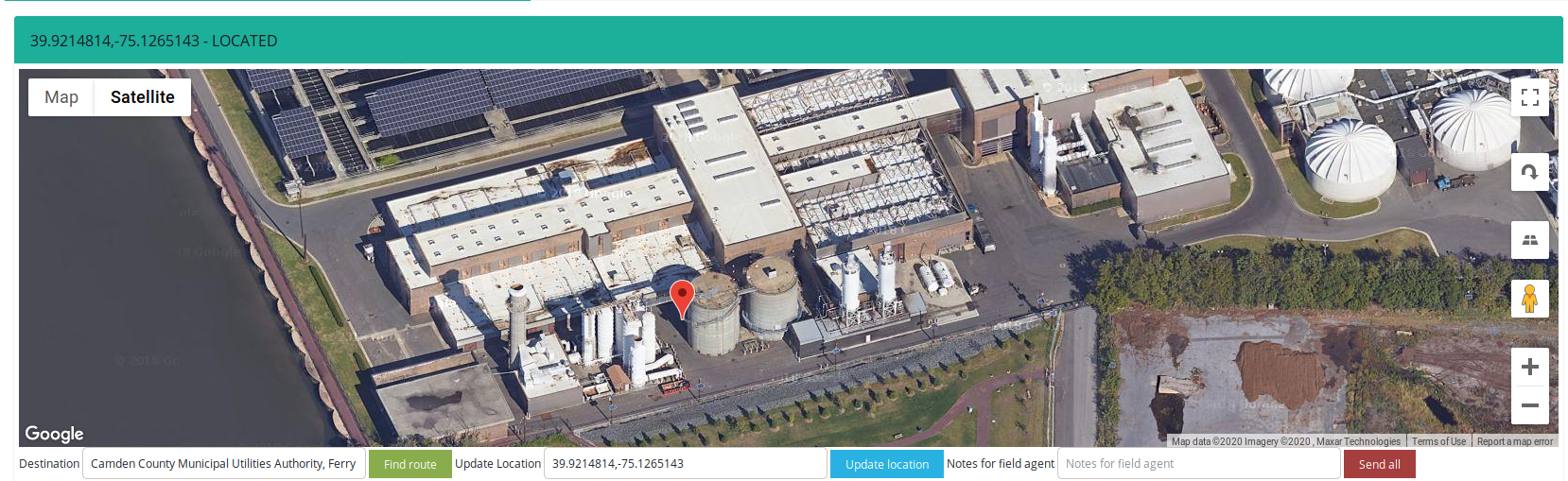
The capacity of the wastewater treatment plant is 100,000 gallons per day. We currently average around 18,000 gallons per day when the schools are in secession and about 9000 gallons per day on holidays and weekends. The wastewater plant also has a back up generator for emergency power. - https://www.camdencountync.gov/departments/public-works/waste-water-treatment-plant
- Grit Pit Groundwater Treatment System in Fort Carson, Colorado
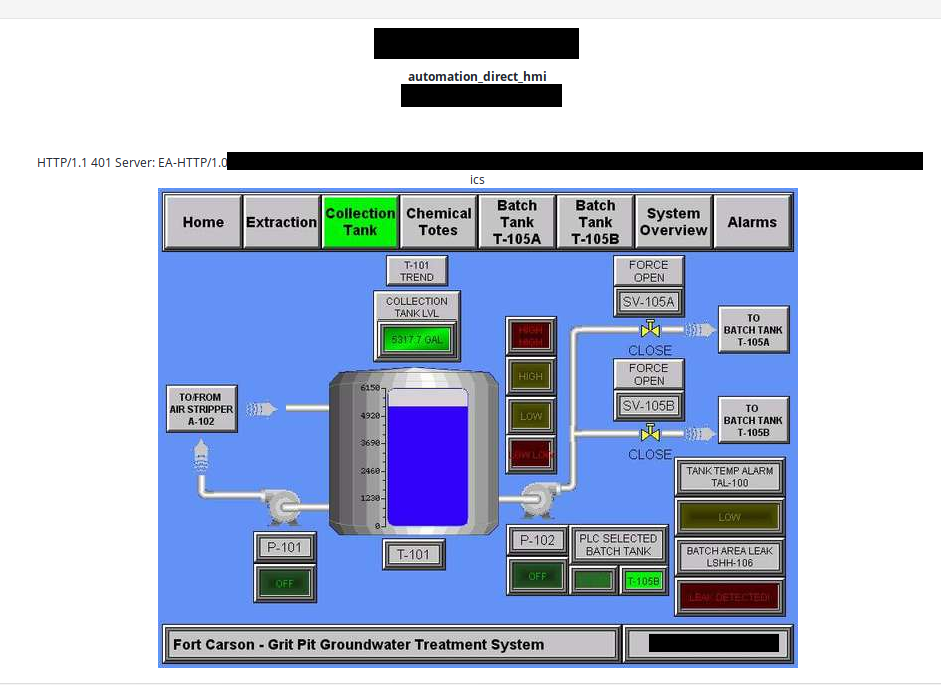
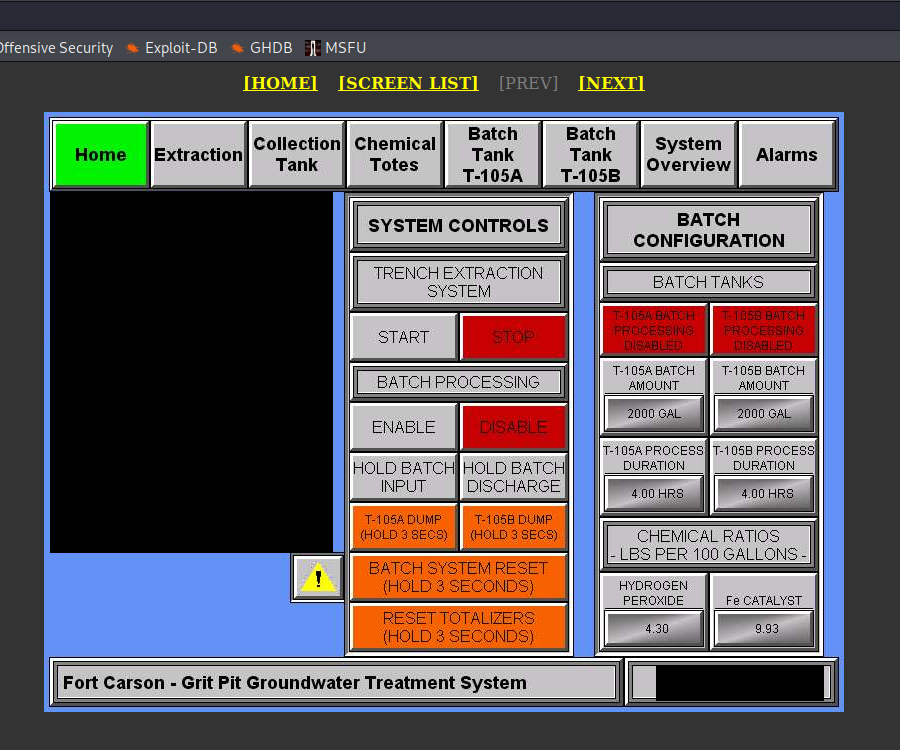
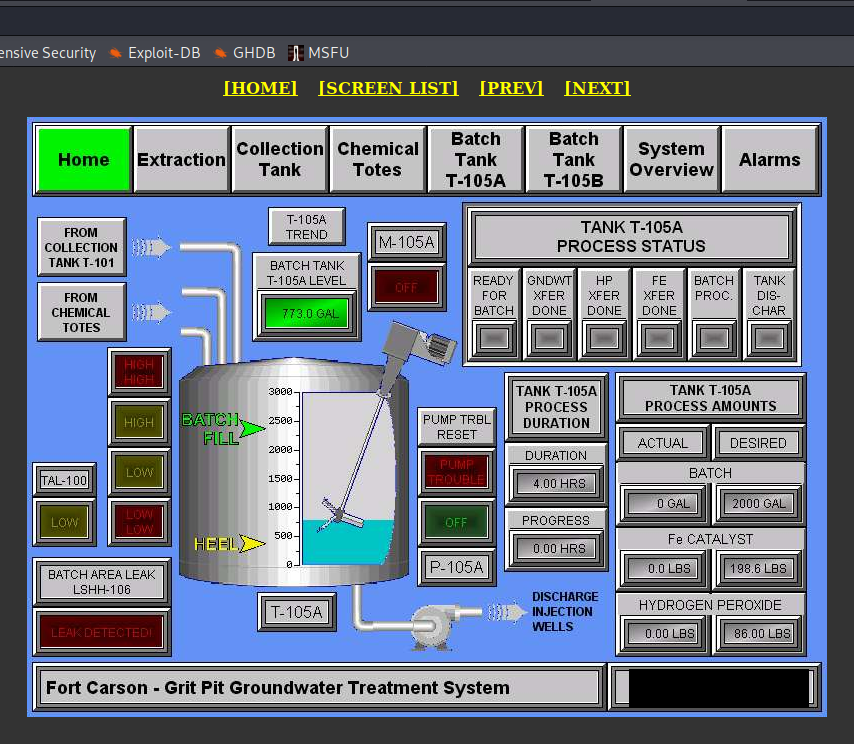
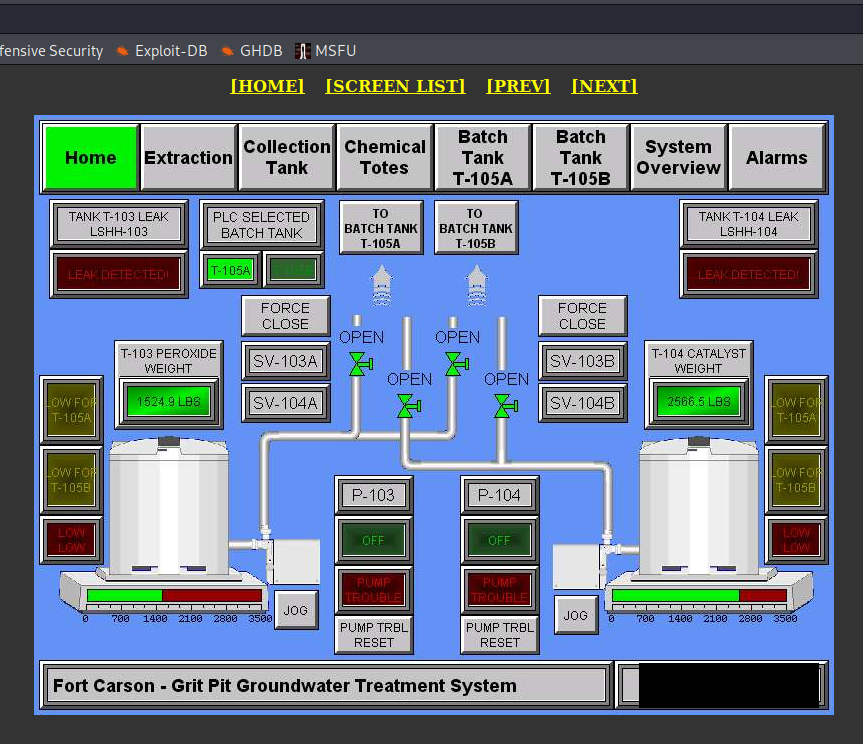
Fort Carson is one of the military bases in United States.
Some activities and practices over the years caused contaminants to enter the soil and groundwater at Fort Carson sites. However, aggressive remediation has been successful enough to allow the Army's mission to continue uninterrupted. - https://www.army.mil/article/203002/colorados_fort_carson_creatively_tackles_environmental_restoration
It does not often happens when you have insight to the infrastructure in enemy's military base. As article states it's important place to make military activities uninterrupted.
- Ship Navigation via VNC
- Terminal, Granite City, Illinois
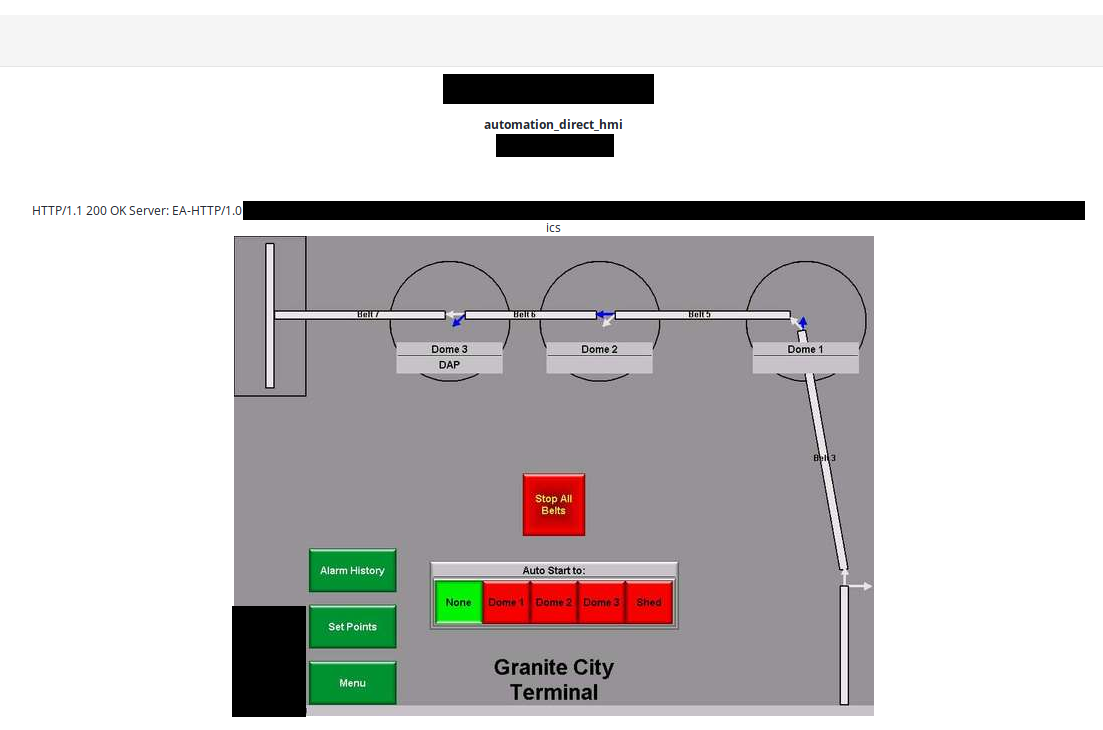
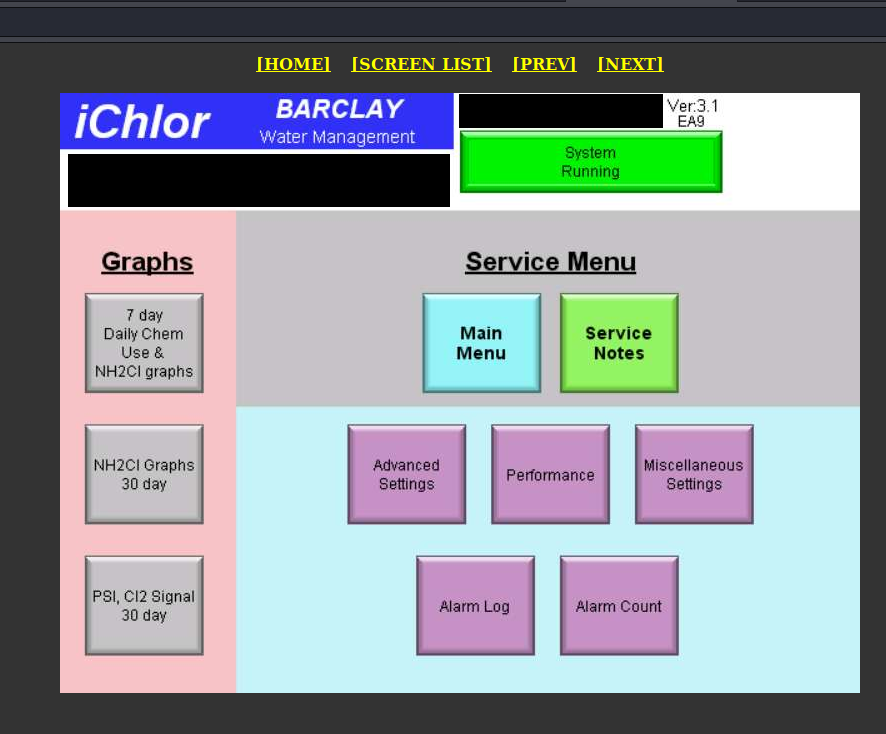
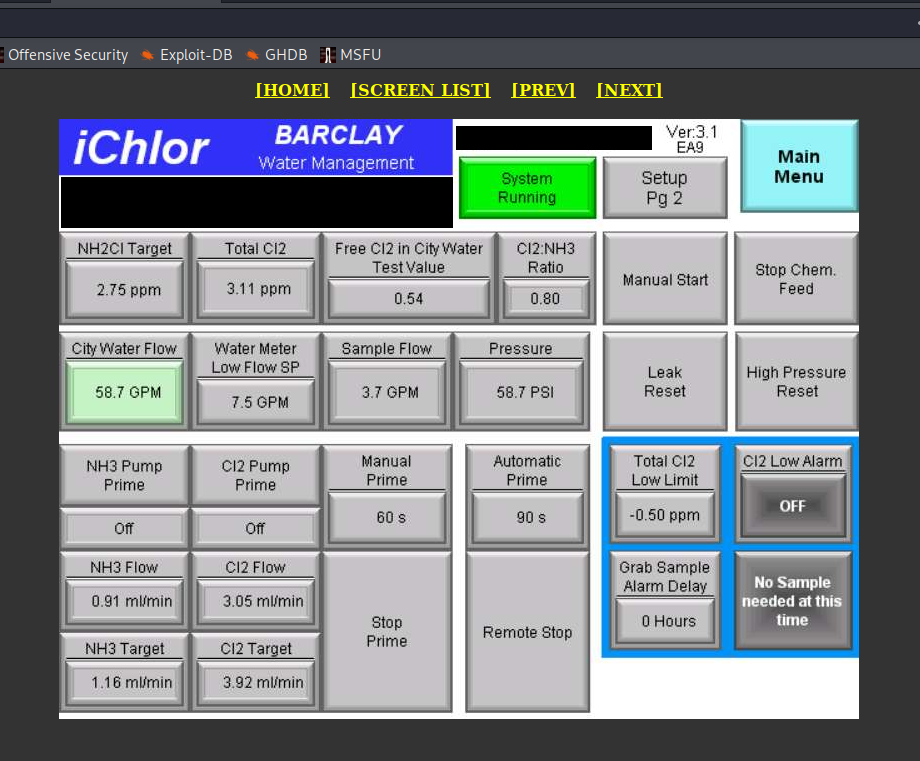
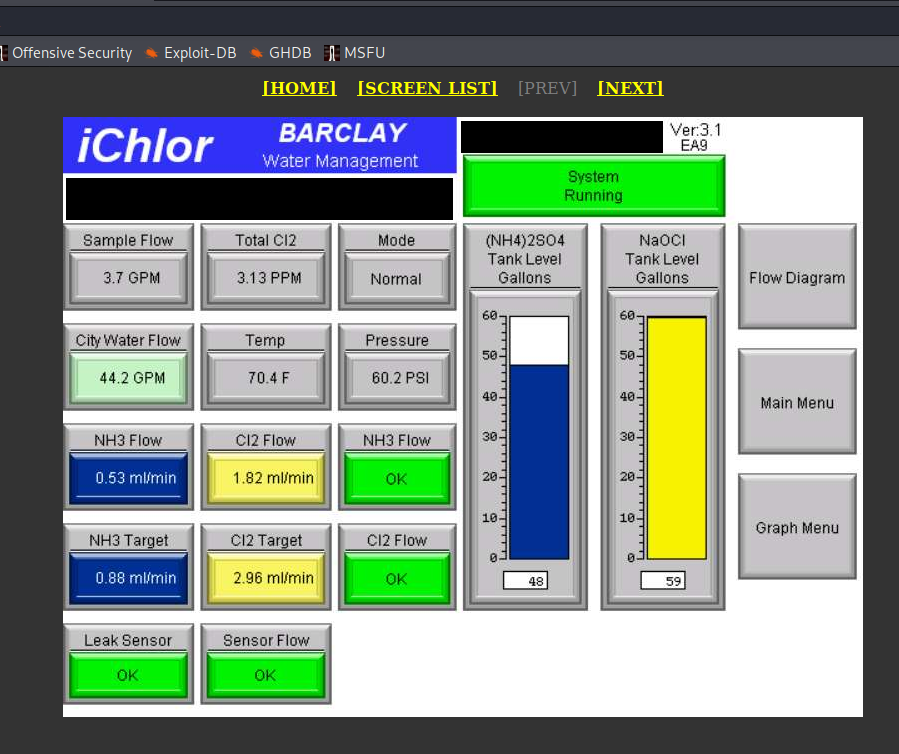
We have no doubts about geolocation. HMI diagram perfectly reflects whole facility.
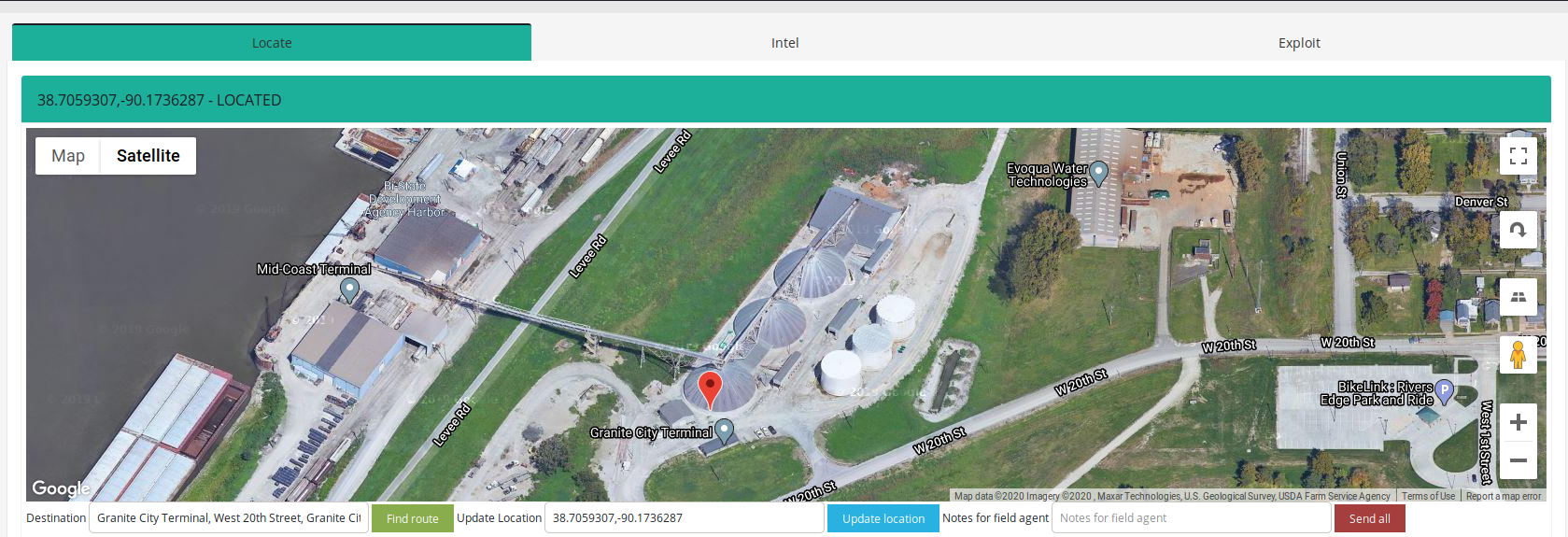
Located in the heart of the United States on the Mississippi River, the Tri-City Regional Port District provides a variety of services and facilities that support the transfer of goods by barge, rail, and truck throughout the region and to international destinations. This special-purpose unit of local government is charged with developing the southwestern Illinois economy by creating and maintaining a multi-purpose port district.

It's another strategic place in transportation sector. Disrupting service of the terminal would cost lot of money and destabilize transport of goods.
- Earth Engine, unknown location
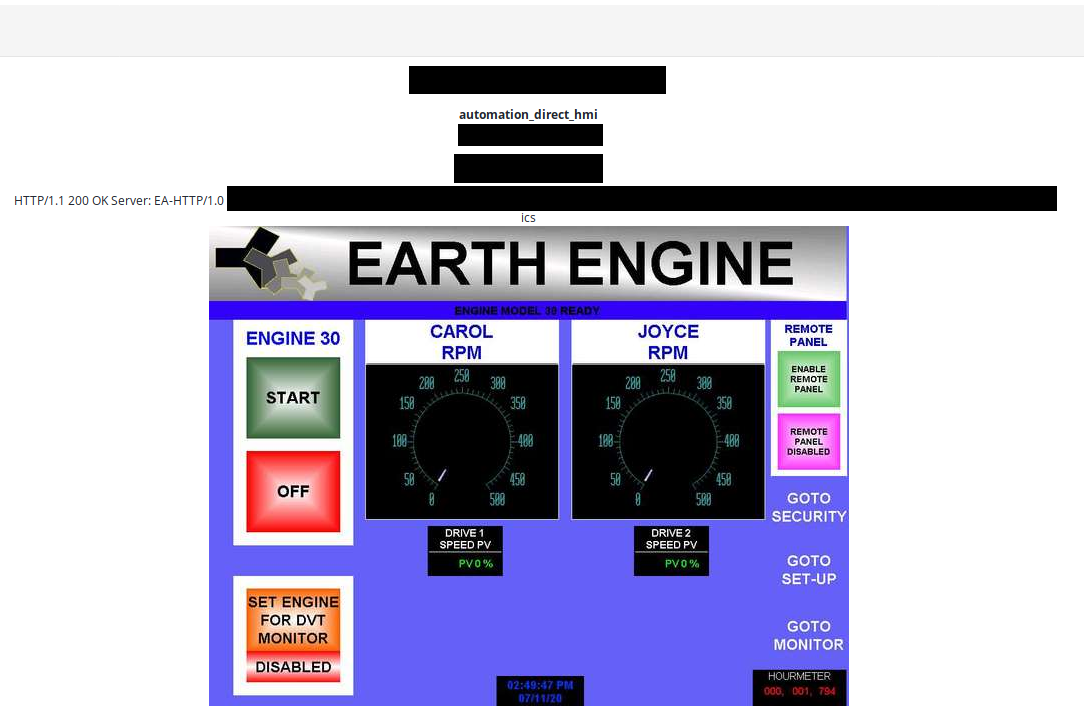
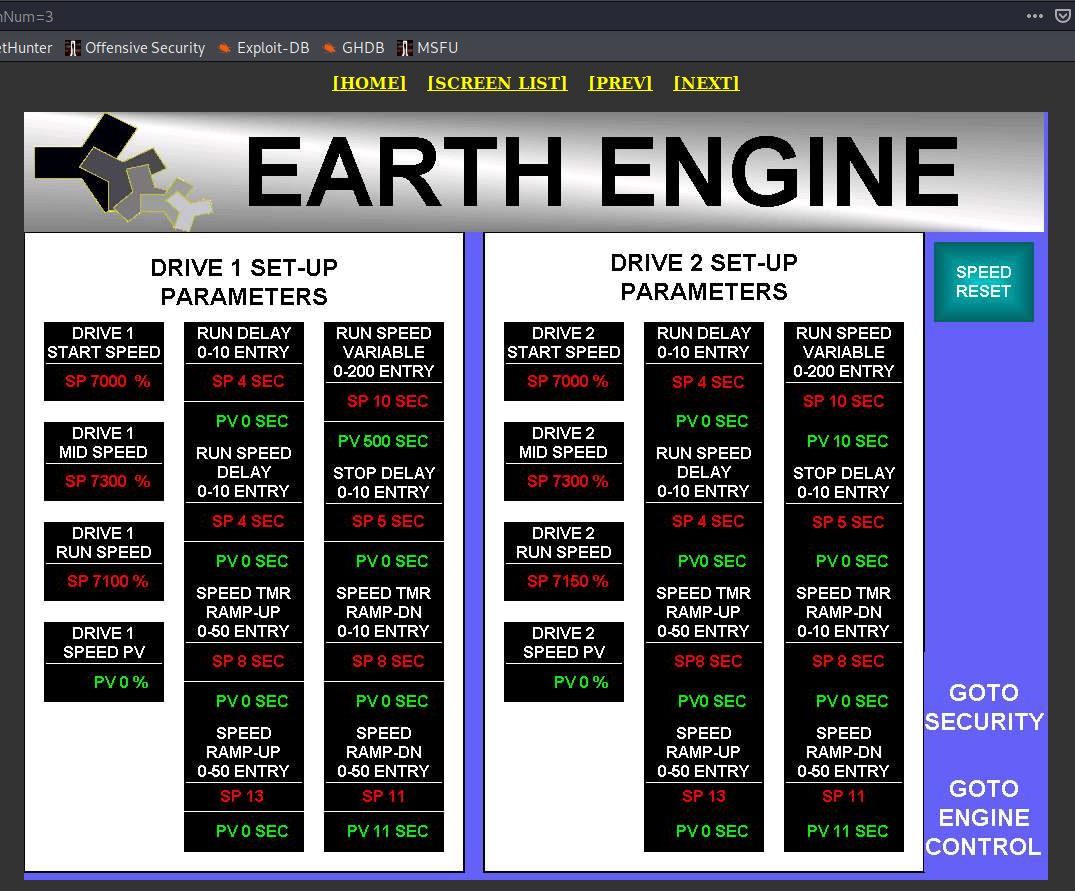
It's hard to estimate how many of these devices exist in the world but I strongly believe that only few have been made for commercial purposes. It produces clean energy with help of Asymmetrical Magnetic Propulsion. Moreover it does not produce heat, requires no combustion and does not use any fossil fuels.
You can find demonstration of this device on below video
In addition, we can gain more insight via exposed camera
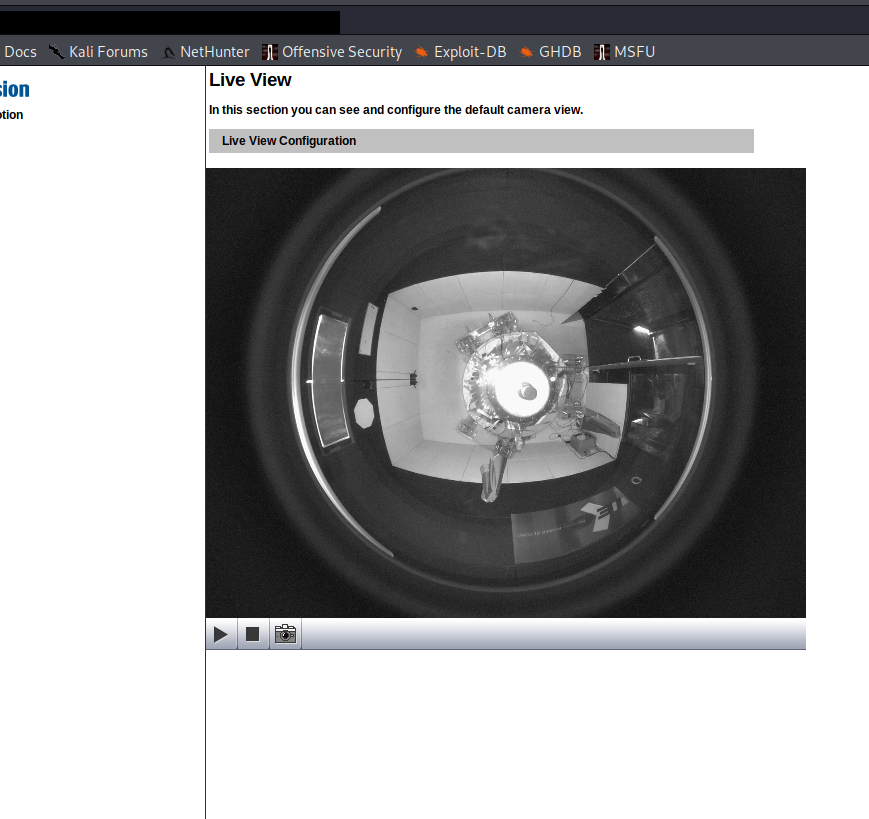
I think it records the device, see the IEC sticker?
It was model 30, publicly disclosed and commercial one, however another device is also exposed to the Internet. It's model h44 and there are completely no information about this model on the vendor website or in the Internet.
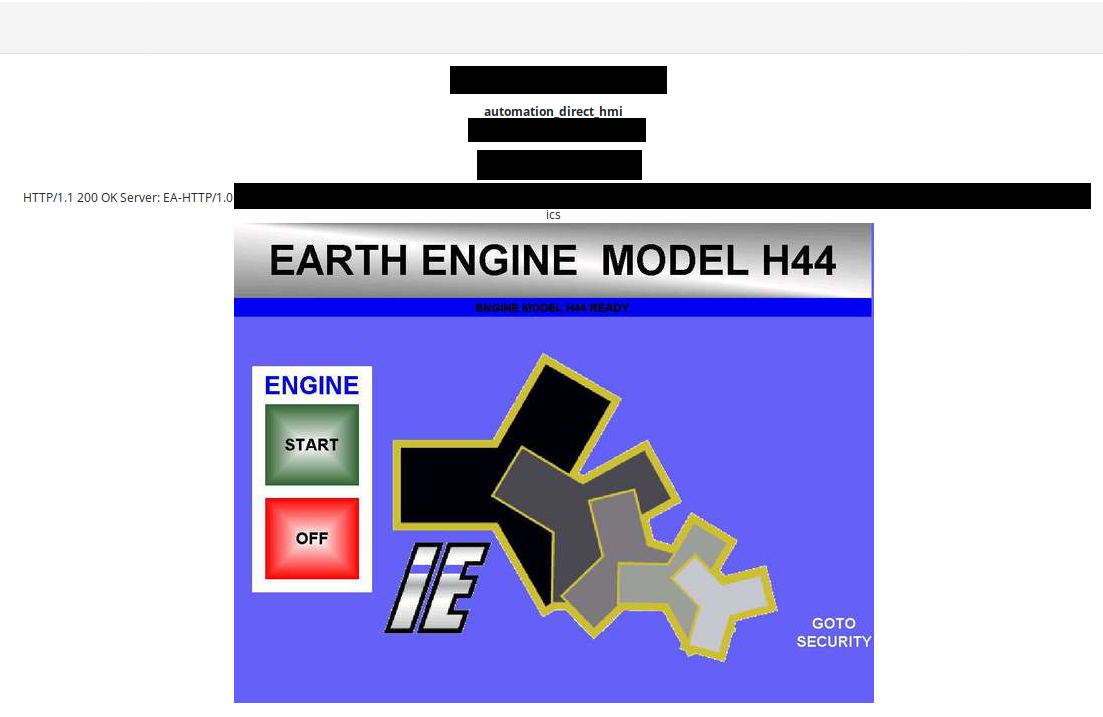
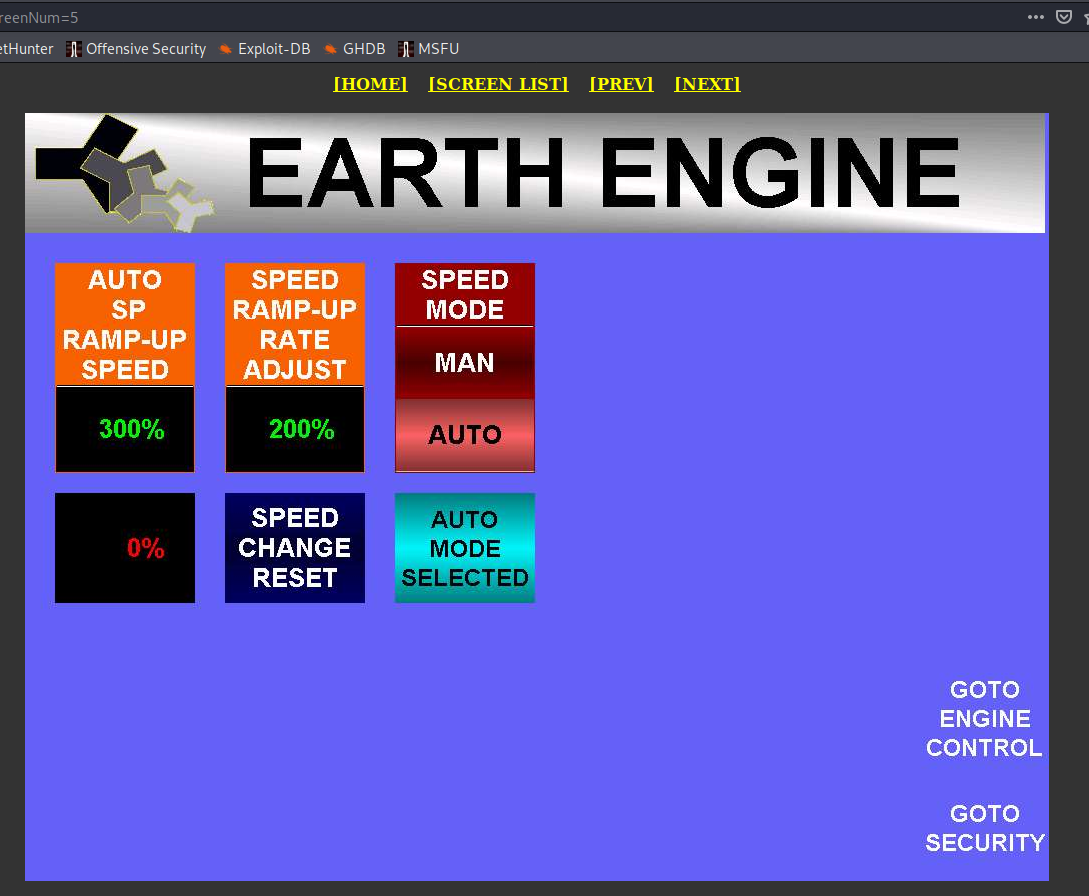
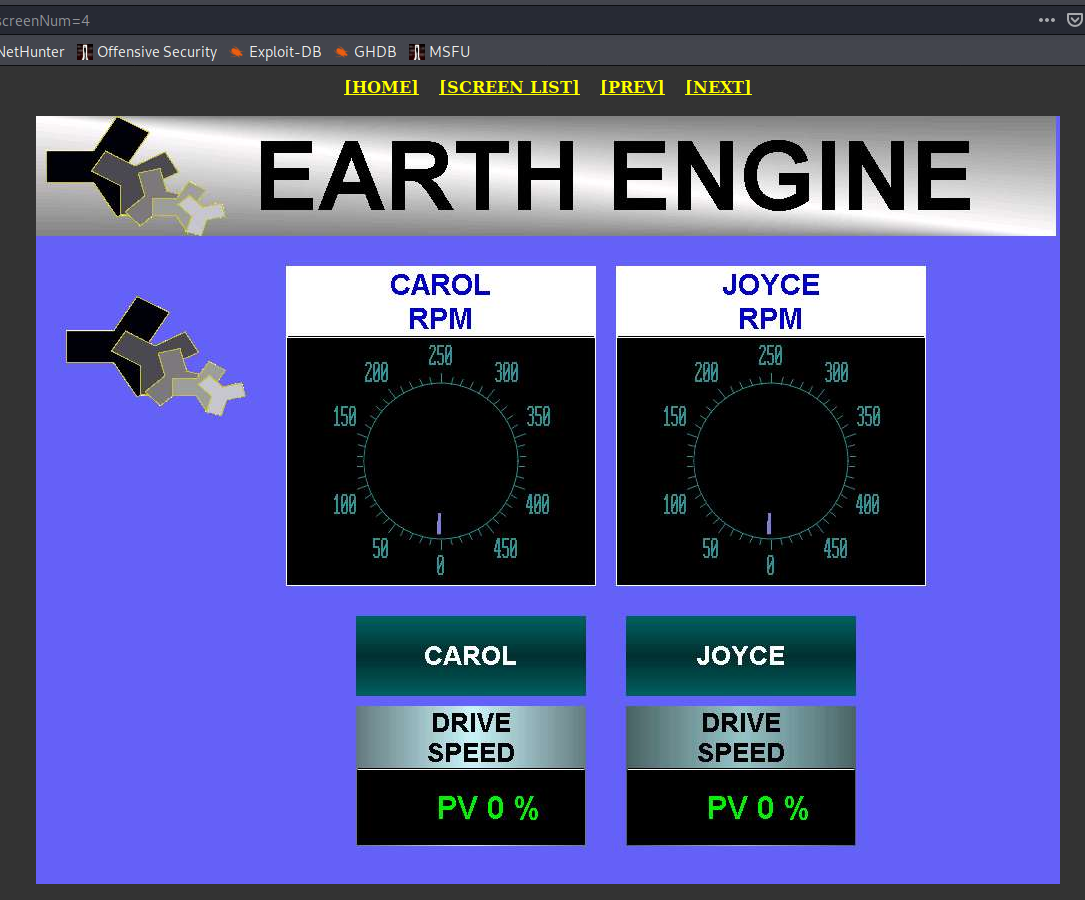
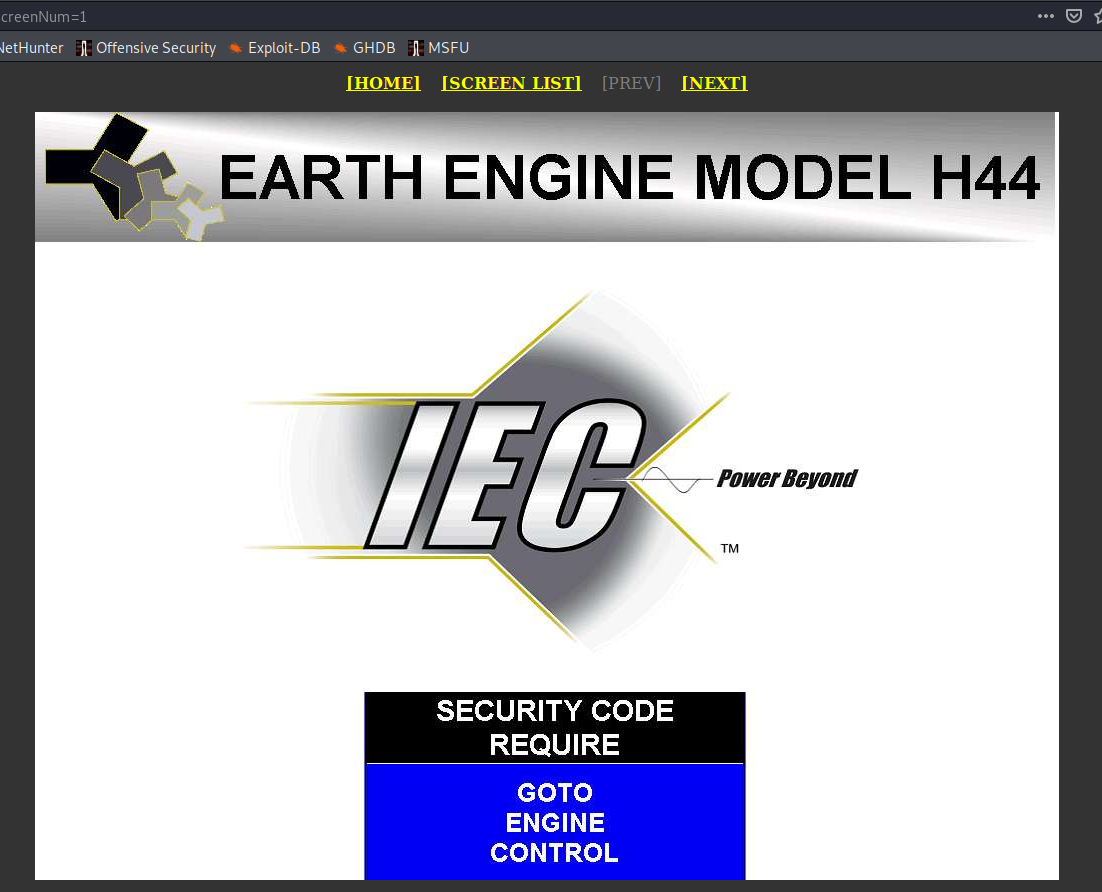
I strongly believe these devices are still super fragile and definitely any part should not be connected directly to the Internet.
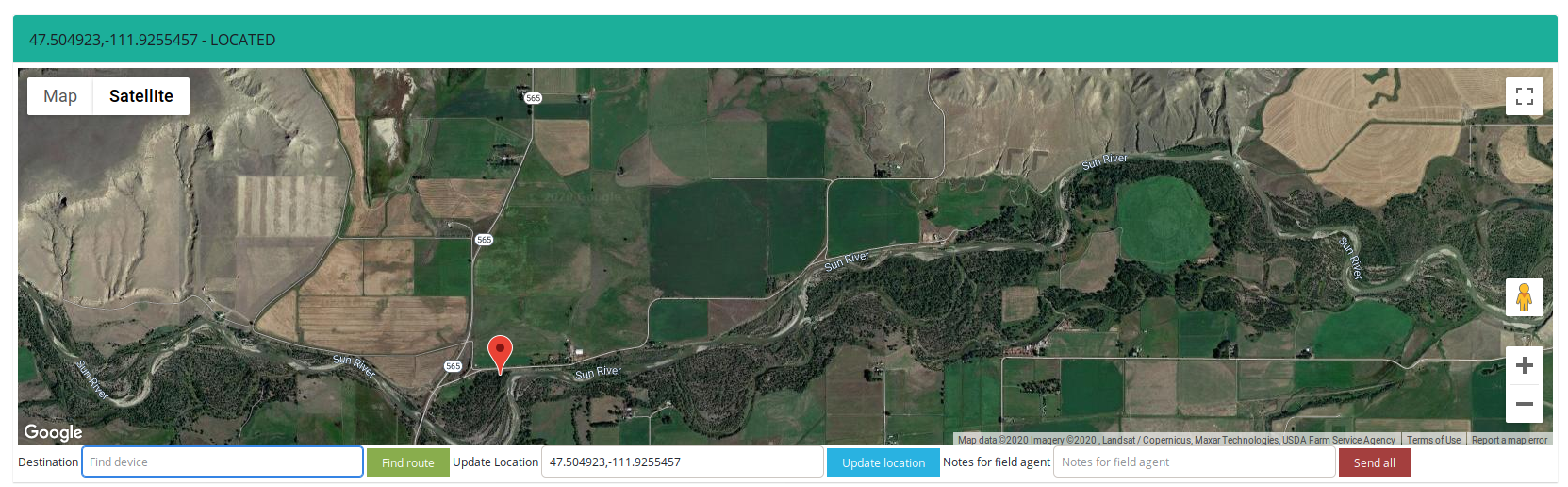
- Sun River, Simms Creek, Adobe Creek canals and dams

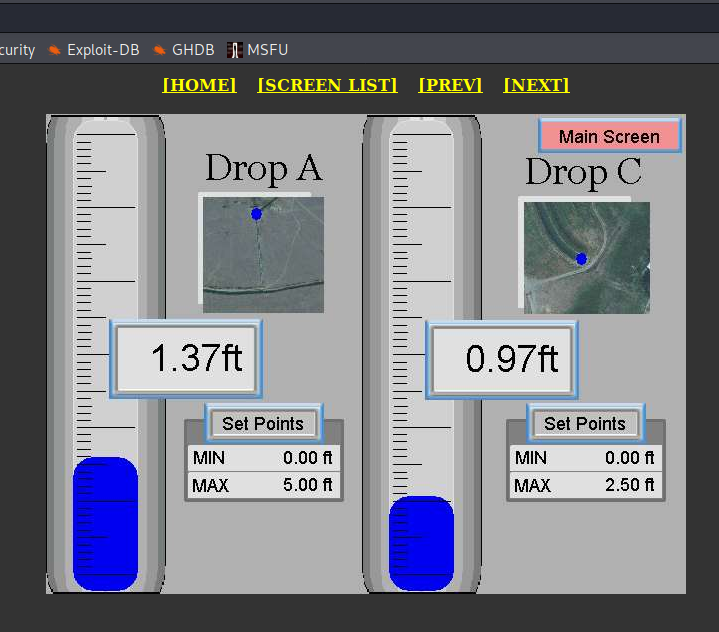
The geolocation of the dams in this case is quite tricky because it support two creeks and canals. Below you can find this same place as on above screen where the main river is Sun River. The Adobe and Simms creeks have their own dames but at the end connects to Sun River.
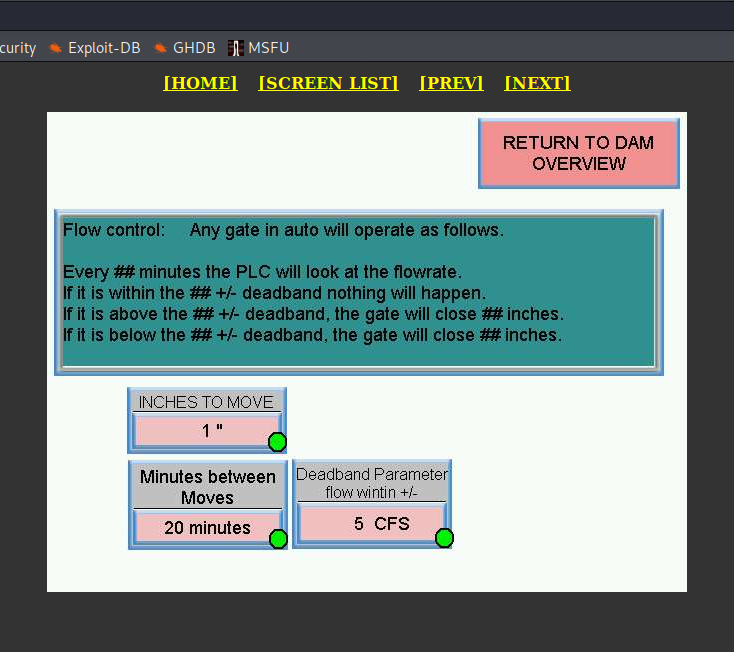
In addition, it exposes control panel for the dam in Sun River.
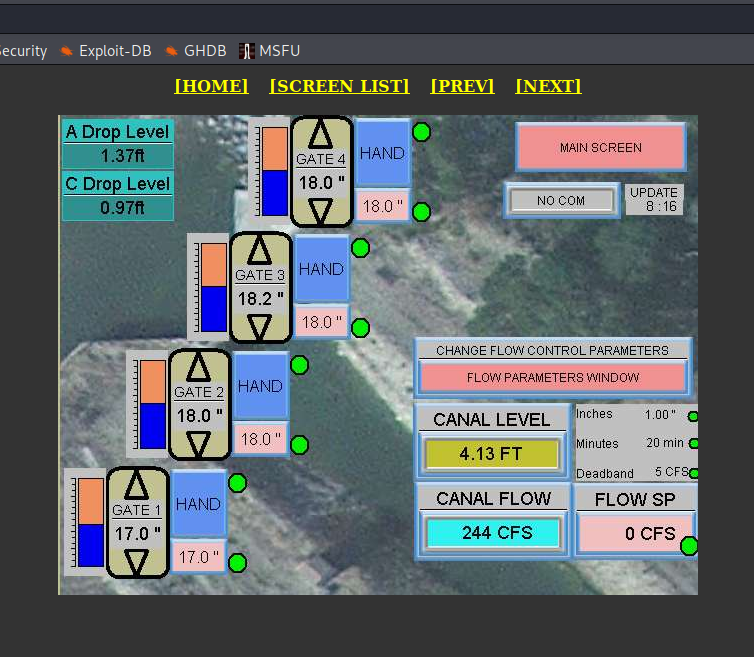
I followed whole Sun River to find this particular dam which consists of four gates and is the biggest dam on the river.
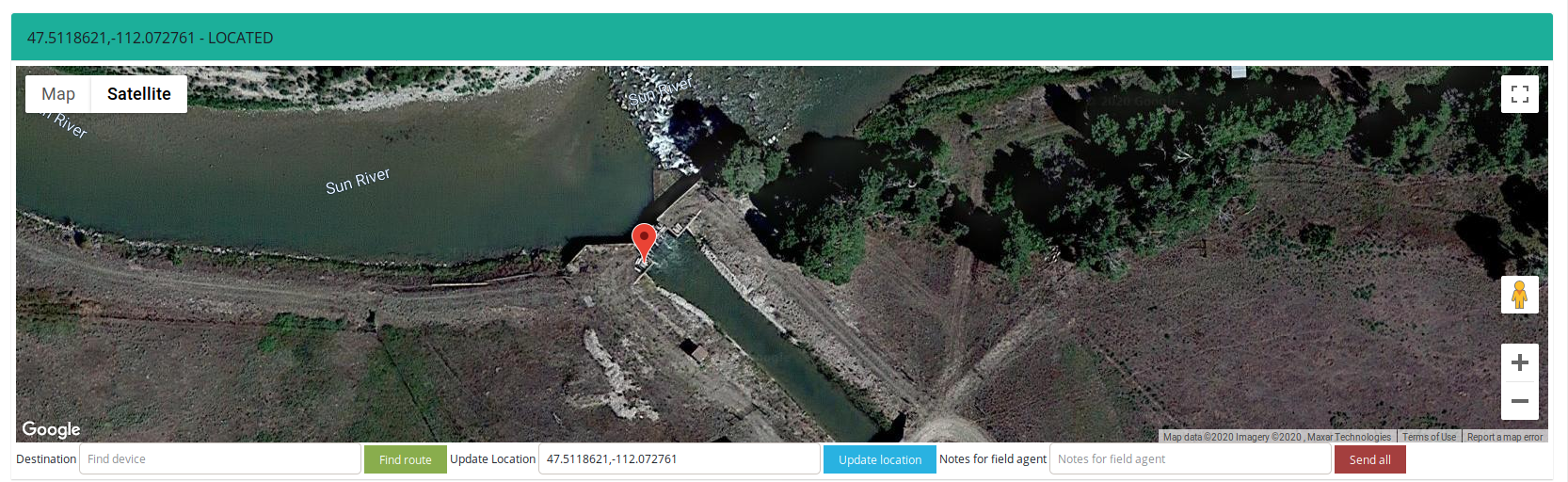
Dams are next sector of critical infrastructure and should be treated with maximum security level. I linked to the article how Iranian hackers gained access to the dam in New York directly via exposed device. What's more, it allows to gather inside knowledge about dams and infrastructure. Also meters are important thing to investigate, it gives knowledge about potential limits applied to each dam.
I have a lot more findings for United States like nutrient management systems in Lockheed Martin facility, Air Treatment system in Sheboygan Falls, Wisconsin that belongs to Millipore Sigma, Water treatment plant in North Cocopah, Pumps of Oklahoma or tank storage systems.
Russian Federation
I searched through all possible queries I could find regarding HMI, and also for screenshots in Shodan but I didn't have much luck. As mentioned earlier, majority of devices are operated manually which makes the whole footprint of exposed ICS sustainable smaller.
- Planetary Spectroscopic Laboratory, unknown meters via VNC, Russian Space Science Internet
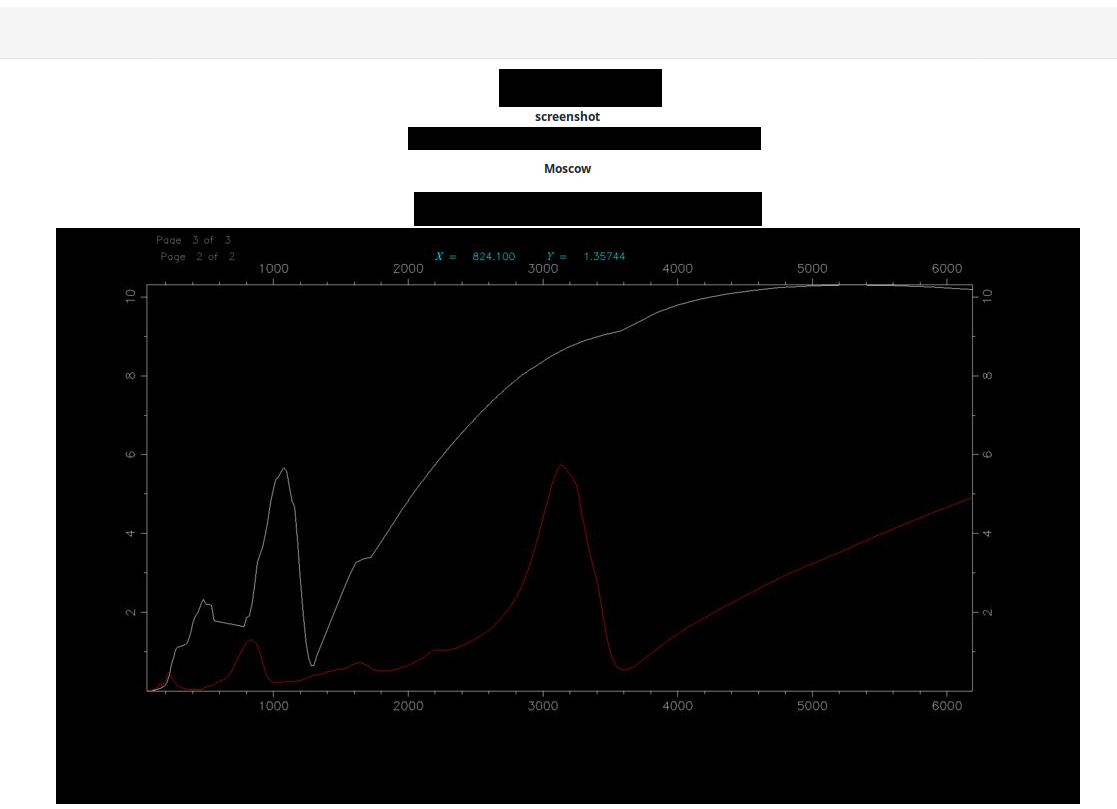
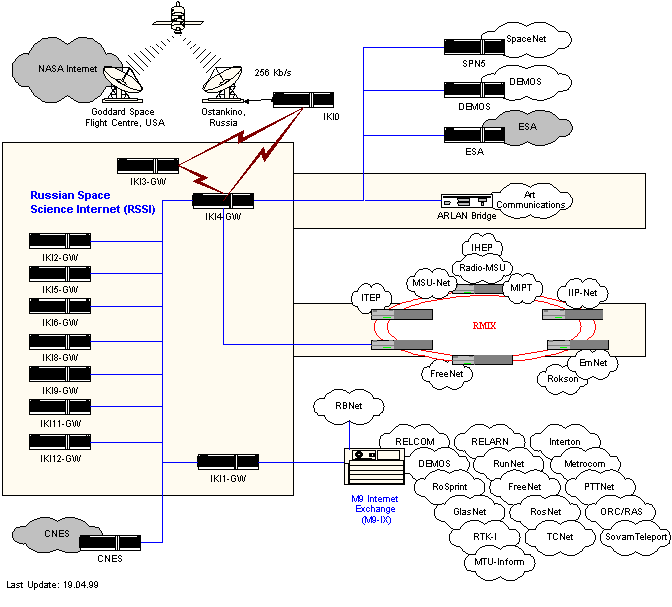
The Russian Space Science Internet supports all science flight missions and space research programs in Russia.
The Russian Space Science Internet supports all scientific programs and research projects in Russia.
The Russian Space Science Internet supports all telecommunication programs and projects in Russia and elsewhere.
RSSI presents infrastructure topology on it's website, so in case of intrusion and information gathering it's quite handy.
- Unknown device
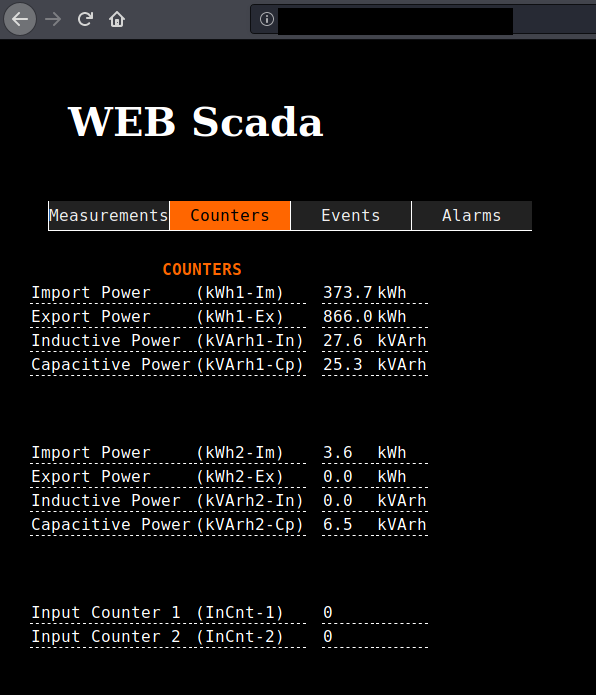
- Unknown device
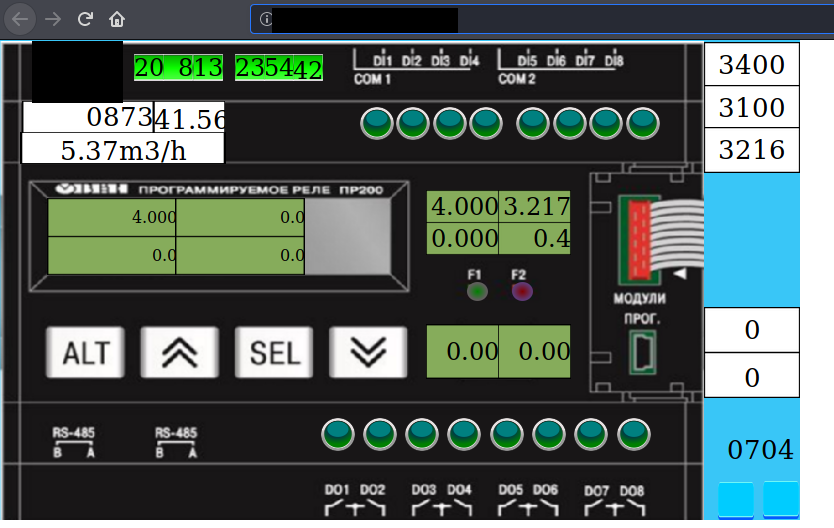
- Unknown device
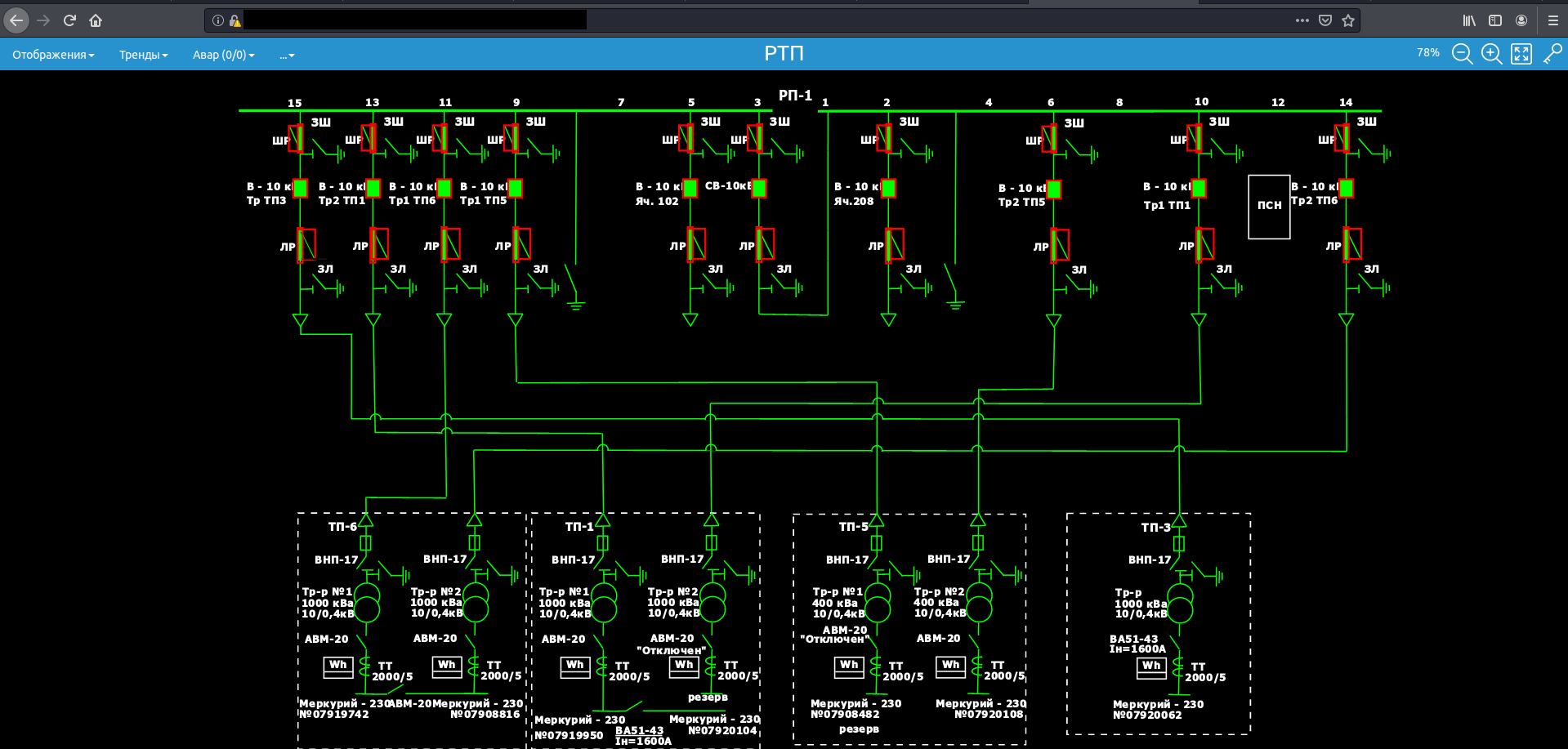
- Unknown device
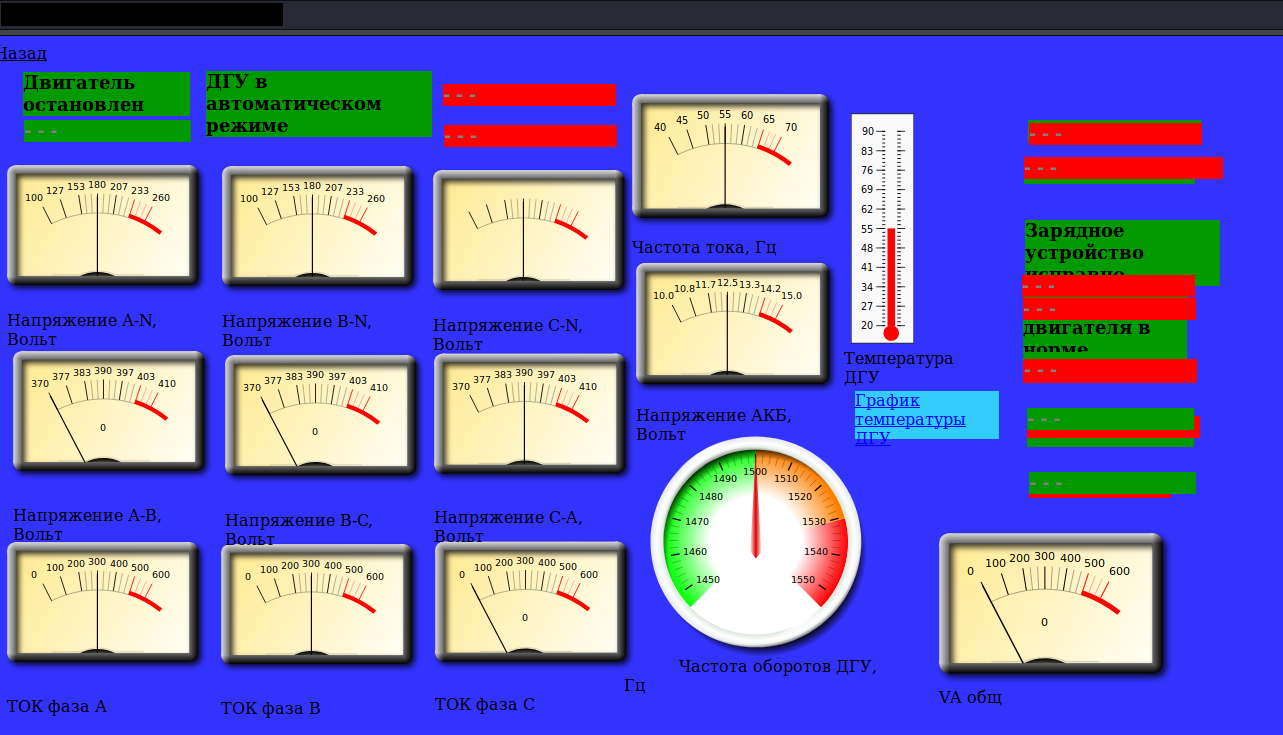
When we look on both countries in this aspect, US looks like a playground for Russians. They can collect valuable intelligence like diagrams of critical infrastructure, satelite images, emails, password and much much more. If they do constant monitoring of exposed US critical assets they can also go for easy win and quickly breach the perimeter if such vulnerable device will appear. After that establish a stealthy persistence and slowly gain more and more intel about facility.
Exposed Management Systems
It is another important field to secure especially when critical infrastructure buildings come into play. You can find many buildings which expose their management system, from courthouses, police departments to government/military complexes.
United States
- Drug Enforcement Agency, Bakersfield, California
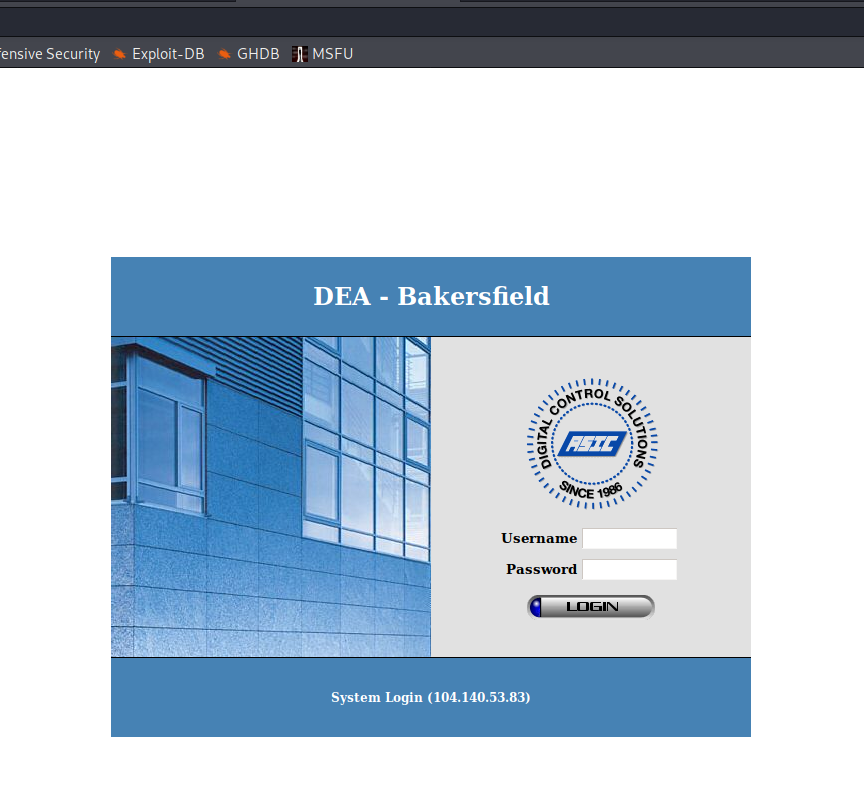
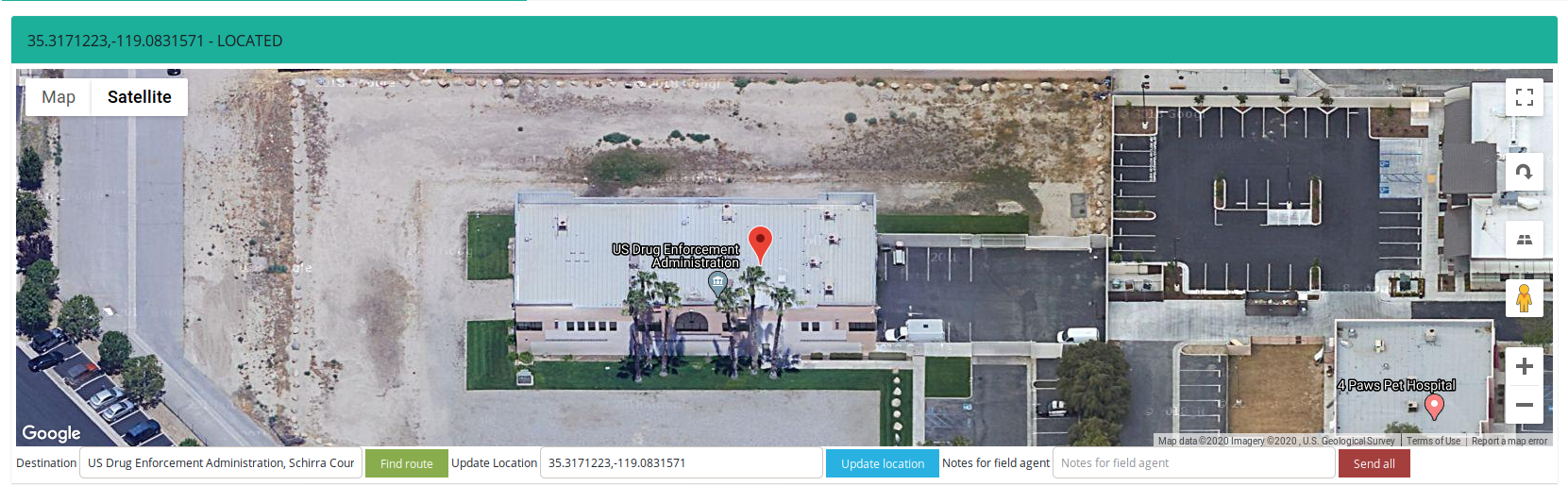
As you can see, even the most fragile facilities, because DEA in my opinion is one of them, could expose the building management system. First of all, you can get access and manage the building by guessing or bruteforcing credentials. Second, due to other vulnerabilities on the host you can gain access to the internal network. If segmentation was not properly done or you are able to find credentials inside the network then lateral movement will be much easier.
- Boeing facility, Helena, Montana

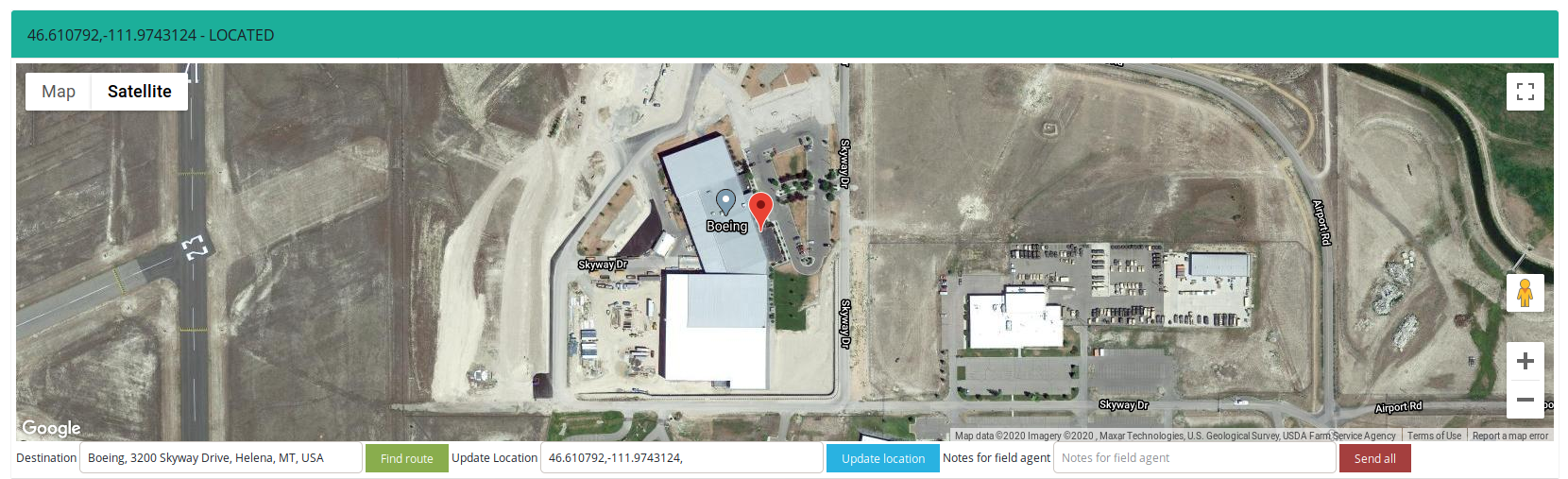
Spying on government supported vendors that produce equipment for military is essential to know enemy capabilities and new technologies they currently work on.
Now more than 257,000 square feet, the Helena facility has become a vital part of the supply chain, specializing in complex machining of hard metals for Boeing's 737, 747, 767 and 787 airplane models – and now the 777X. The new parts machined in Helena for the 777X will include side-of-body chords and terminal end fittings which connect the wings to the fuselage.
It's also part of the critical infrastructure, disrupting facility operation might cost lot of money and pause in supply chain.
- Oregon Military Department
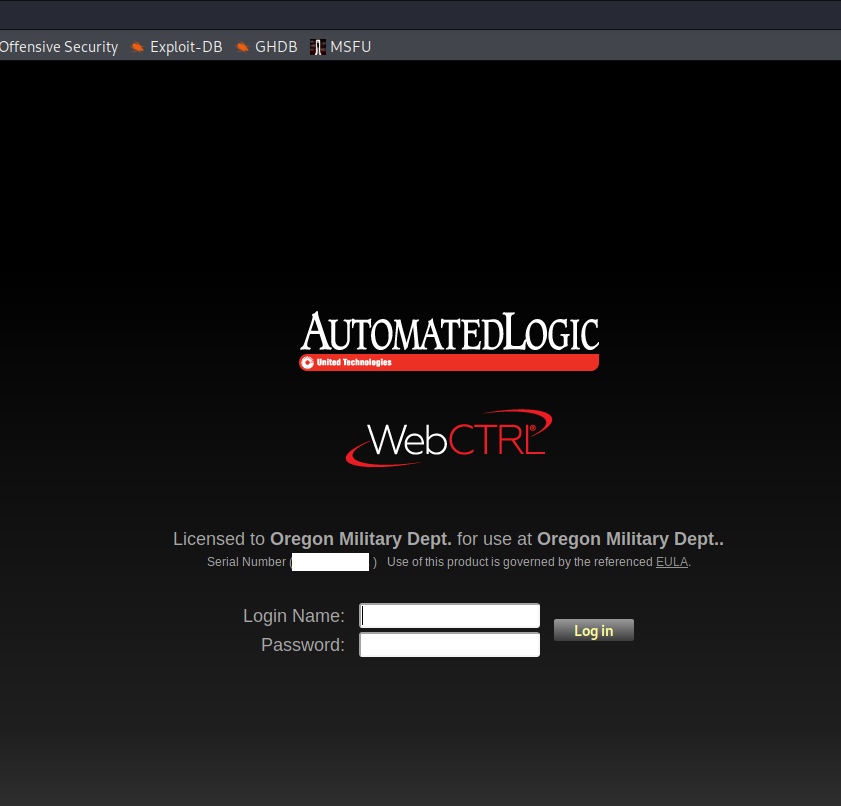
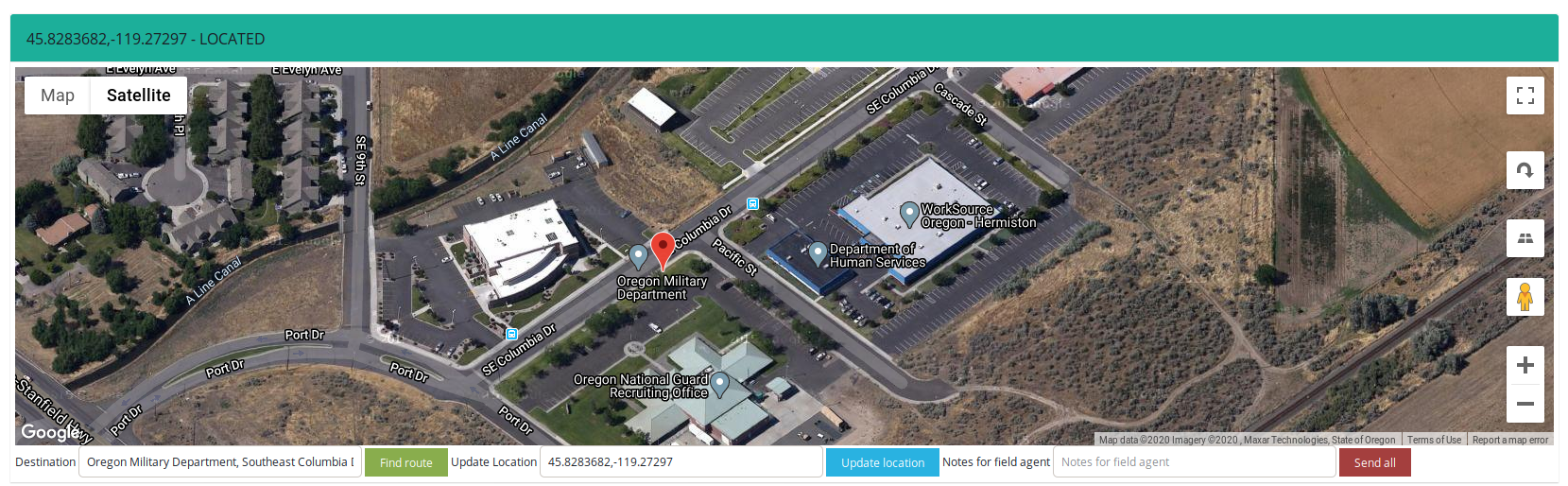
Under the authority and direction of the governor as commander-in-chief, the agency is responsible for planning, establishing, and enforcing rules and procedures governing the administration, supply, and training of the Oregon National Guard (consisting of the Oregon Army National Guard and the Oregon Air National Guard)
- Sikorski Military Completions Center North Horseheads, New York
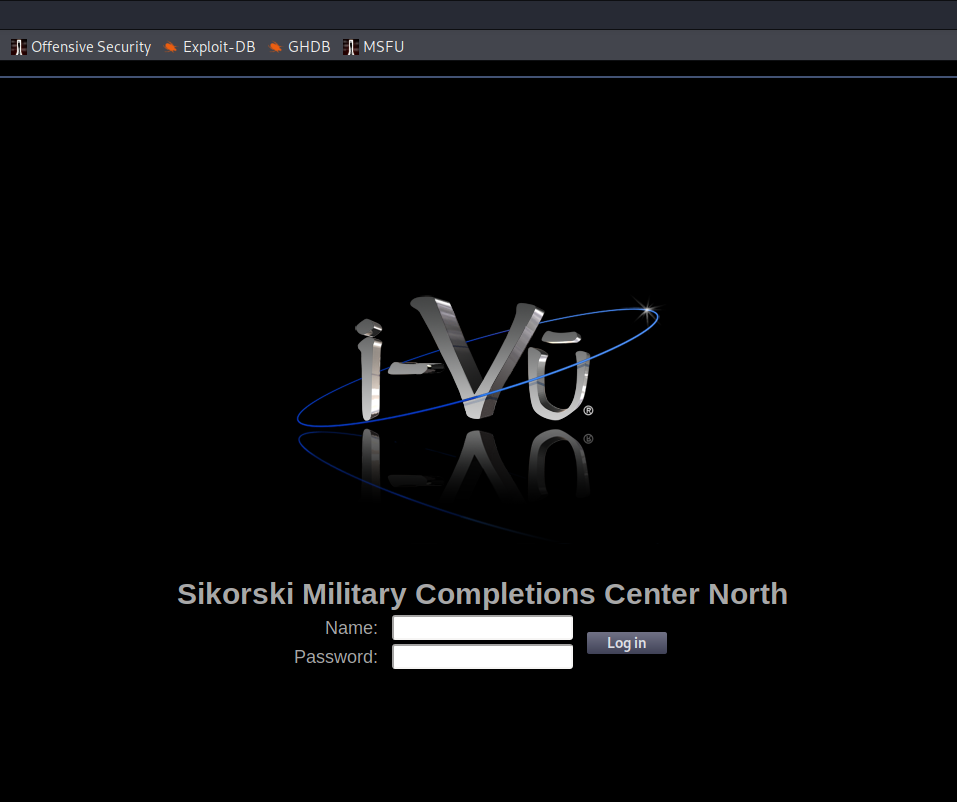
Sikorski Military Completion Center has been closed down in 2012. They were producing unmanned helicopters like Fire Scout or specially modified Black Hawks.
The Sikorsky Military Completions Center is a diversified aerospace company, globally recognized for our industry-leading aircraft products, which include helicopters, fixed-wing reconnaissance aircraft, and unmanned aircraft vehicles. The Sikorsky HAWK WORKS serves as the primary completion center for all BLACK HAWK and Naval Hawk derivative aircraft. - https://www.corporategray.com/employers/30733/public_profile
Currently Lockheed Martin is owner of Sikorski but the name is still left on building management system panel. Due to this I'm not hundred percent sure about geolocation but I believe it is based in Horseheads, New York.
These facilities are strategic places for military and private supply chain or serves interest of US national security. Spying, disrupting activities or gaining access to the internal network of any of these building would be quite rewarding for Russians.
Russian Federation
Due to low use of automation in Russia, there are not many exposed management systems that could be easily located. There are plenty of WAGO or Moxa interfaces in the cloud but without additional indicator that would point to specific place or facility it is hard to tie them to critical infrastructure. However, ꓘamerka was able to identify some management system that pose the risk if compromised.
- ComAP, unknown location
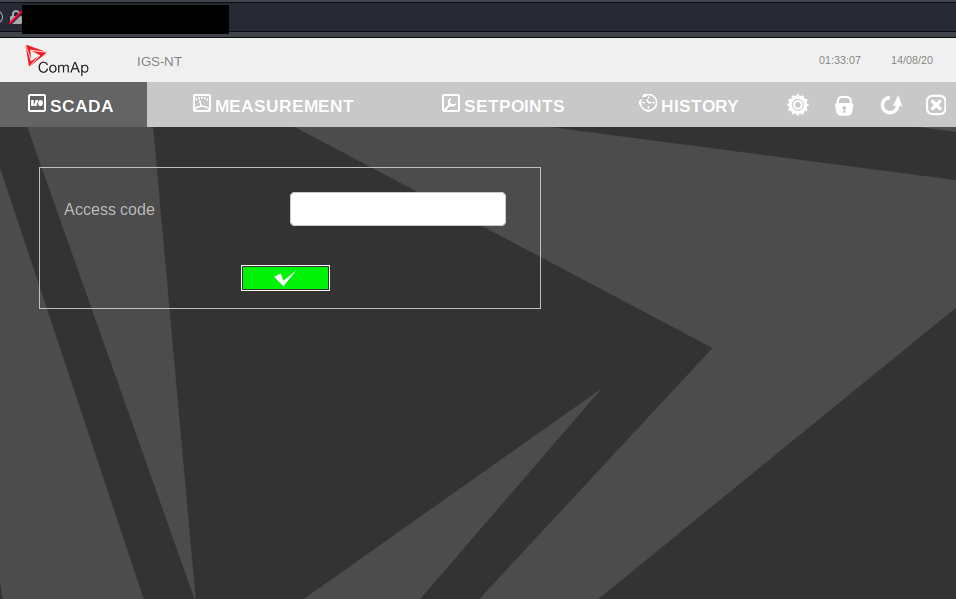
ComAp designs and manufactures control products for power generation and engine control, along with associated accessories and software. We’re leading the way in providing intelligent electronic control products and solutions that are highly flexible, intuitive, and scalable. - https://www.comap-control.com/about-us
It's worth to add that ComAp is company from Czech Republic.
- A3C gas station, unknown location
- Wind turbine, unknown location
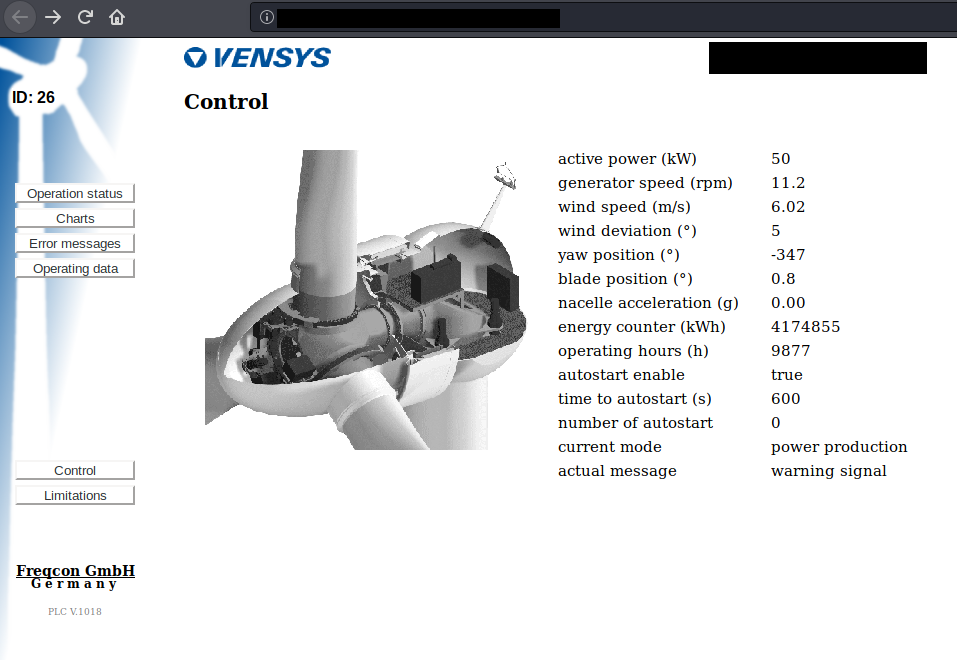
Vensys is a German manufacturer of high quality wind turbines.
- Lubynskay(?)
- Komorsan web panel
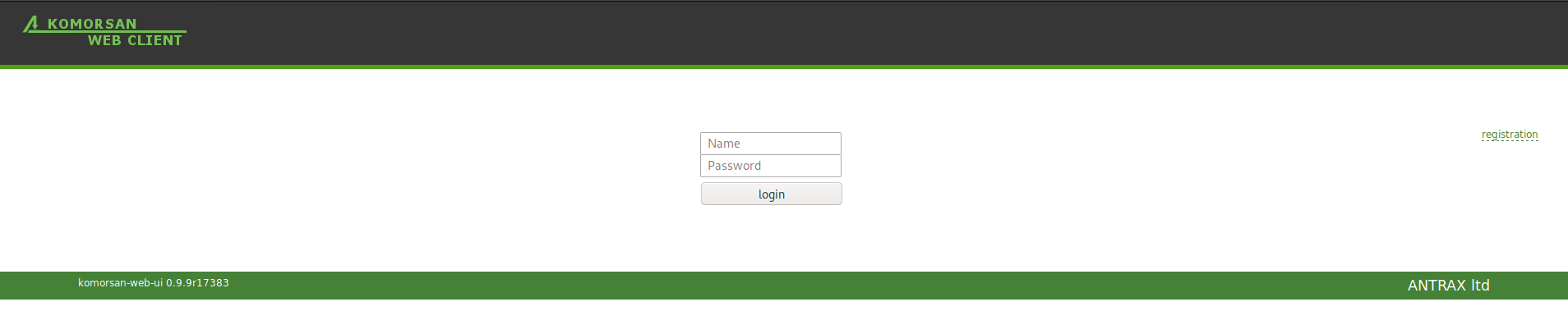
System of power distribution network diagnostics – KOMORSAN 2.2 - is designed for immediate detection of faults and transmission of fault data to dispatching point and targeted customers. The KOMORSAN 2.2 system improves reliability, productivity and efficiency of distribution network. - https://www.a3.energy/products-bottom/monitoring-and-control-software/network-monitoring-system-komorsan-detail
- Simatic Sm@rt Client
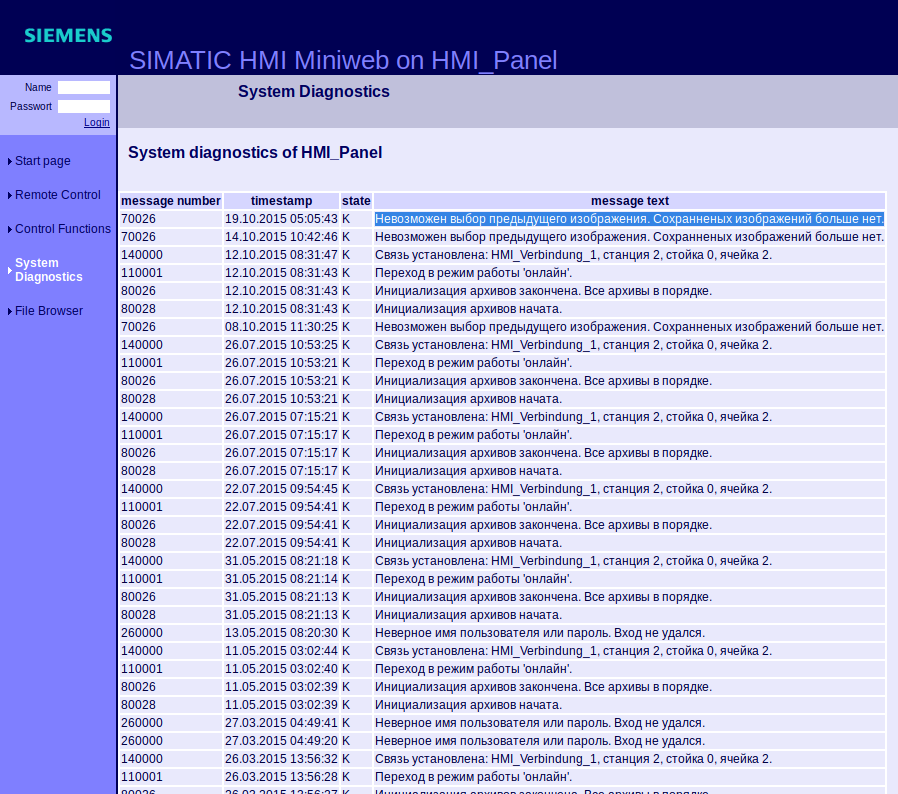
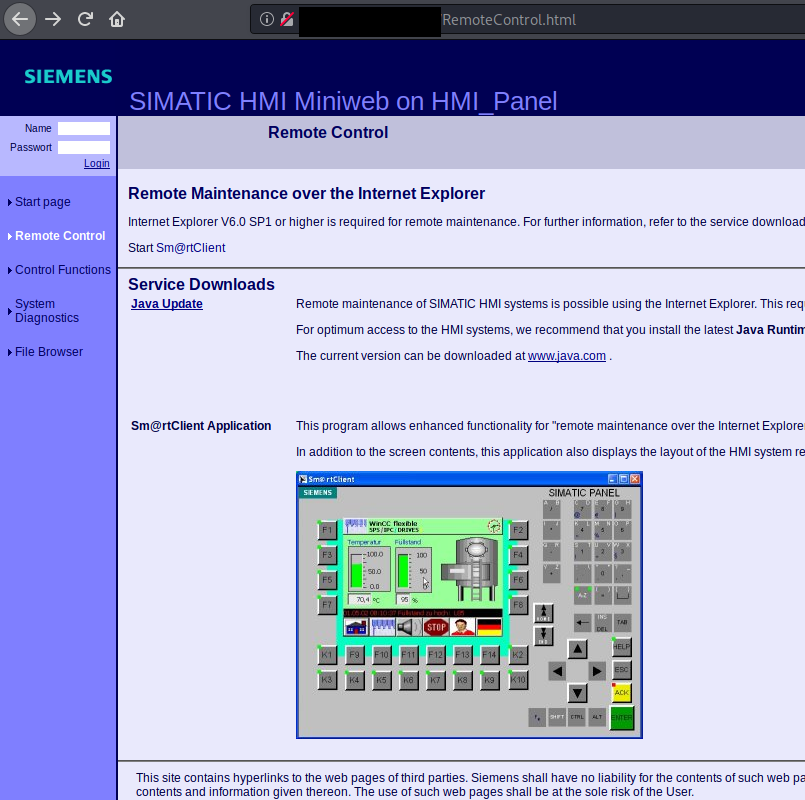
It's definitely harder to find exposed Human Machine Interface in Russia than in United States. Americans have limited possibilities in this field however they have not lost the battle. They can access single devices and based on the meters, alarms or events estimate what device is use for.
The trivial example can be Energomera C805m meters used in power facilities in the retail electricity markets.

or another unknown device
United States actors have to use slightly different techniques to obtain more valuable intelligence about critical infrastructure in Russia. On majority of the exposed devices additional services are running, for example RDP vulnerable to Bluekeep, weak password on VNCs or databases like MSSQL.
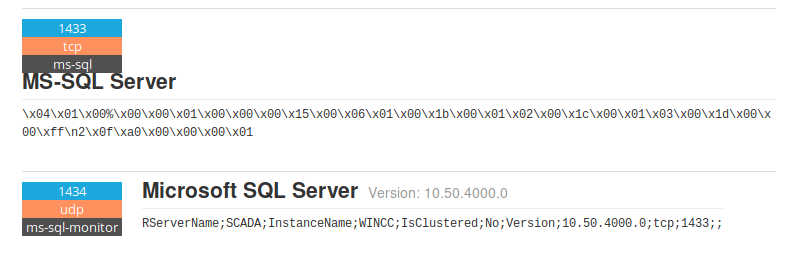
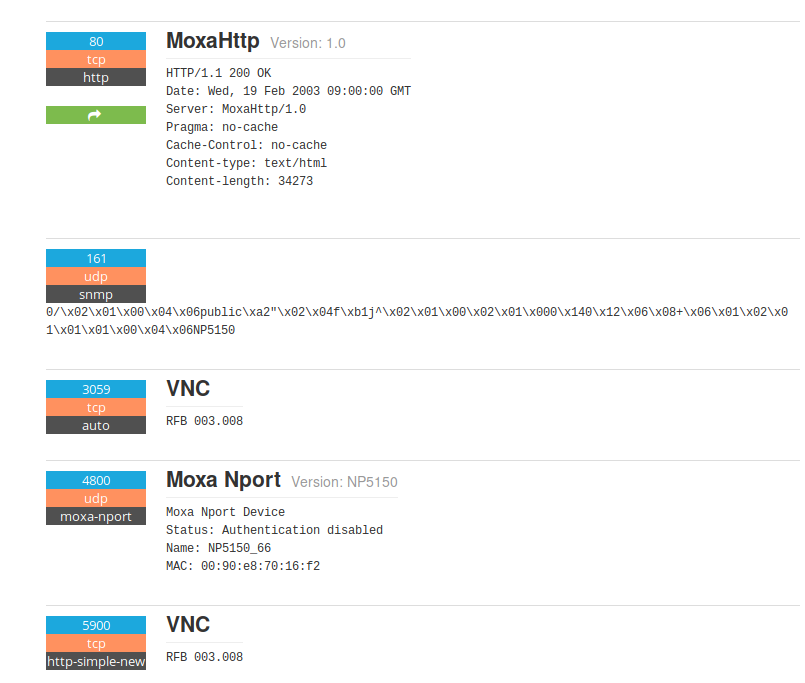
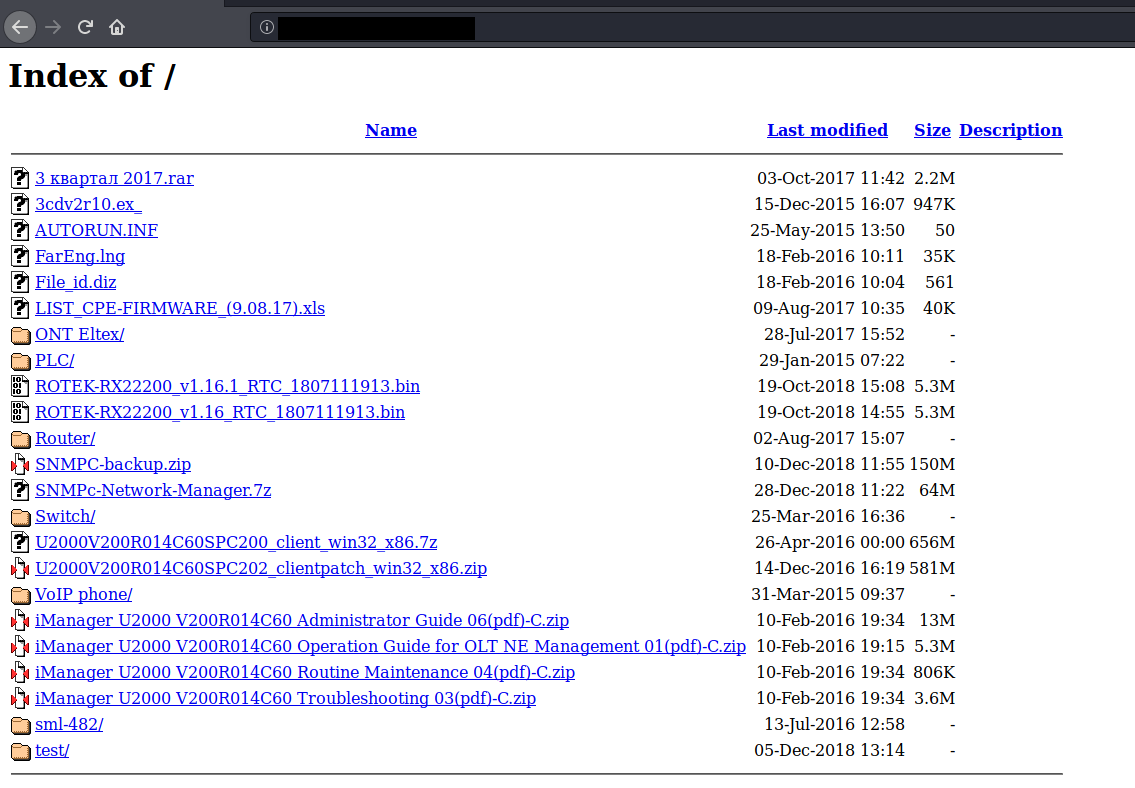
another things that US can do to spy on Russia infrastructure is to look for any leaks related to ICS or Scada and find backups, manuals or firmwares.
Niagara Fox & exposed Cameras
Niagara Fox devices were main topic of my first research into intelligence gathering in United States and you can read it below.
Intelligence Gathering on U.S. Critical Infrastructure
There are thousands of exposed Niagara Fox station to the Internet which reveal their exact position in "station_name" field that is very useful to pinpoint device to specific facility.
I just will show you one example how you can geolocate such building and devices in ꓘamerka.
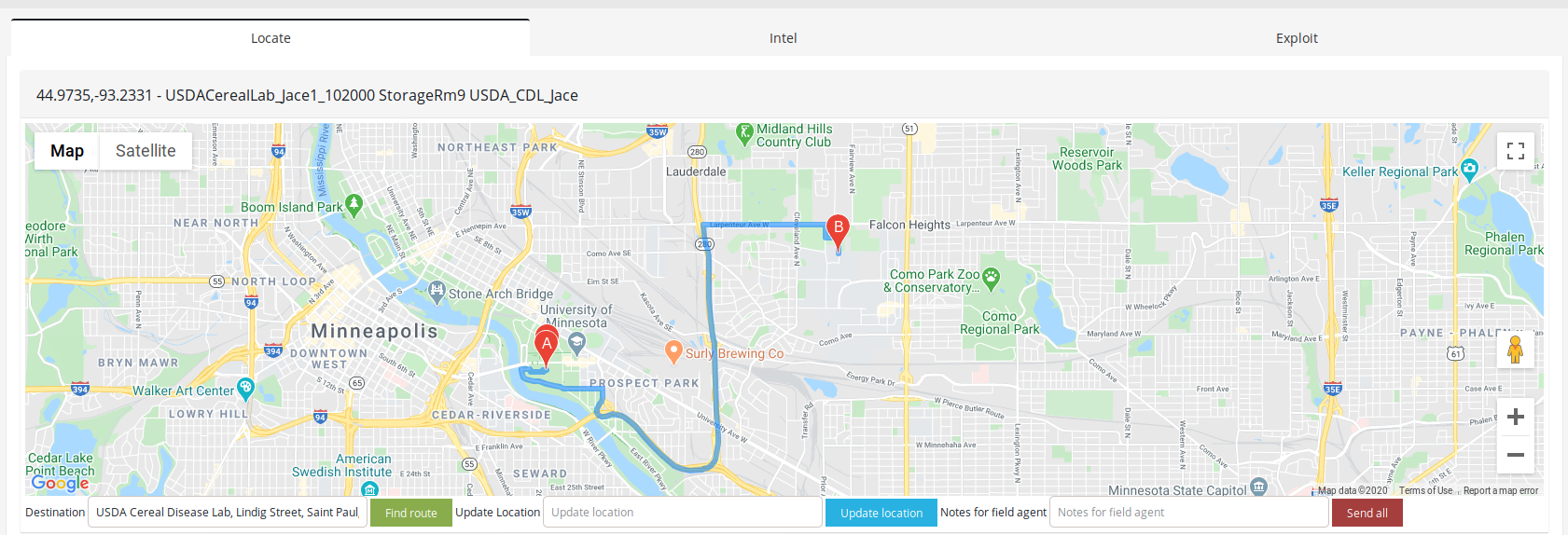
As you can see on above screenshot, ꓘamerka extracted indicator, i.e. value from "station_name" from the device - USDACerealLab_Jace1_102000 StorageRm9 USDA_CDL_Jace.
Next, you can search for the building in "destination" field in the panel which gives you route to the facility.
At the end you zoom it, grab coordinates from google maps and update them in next field in ꓘamerka.
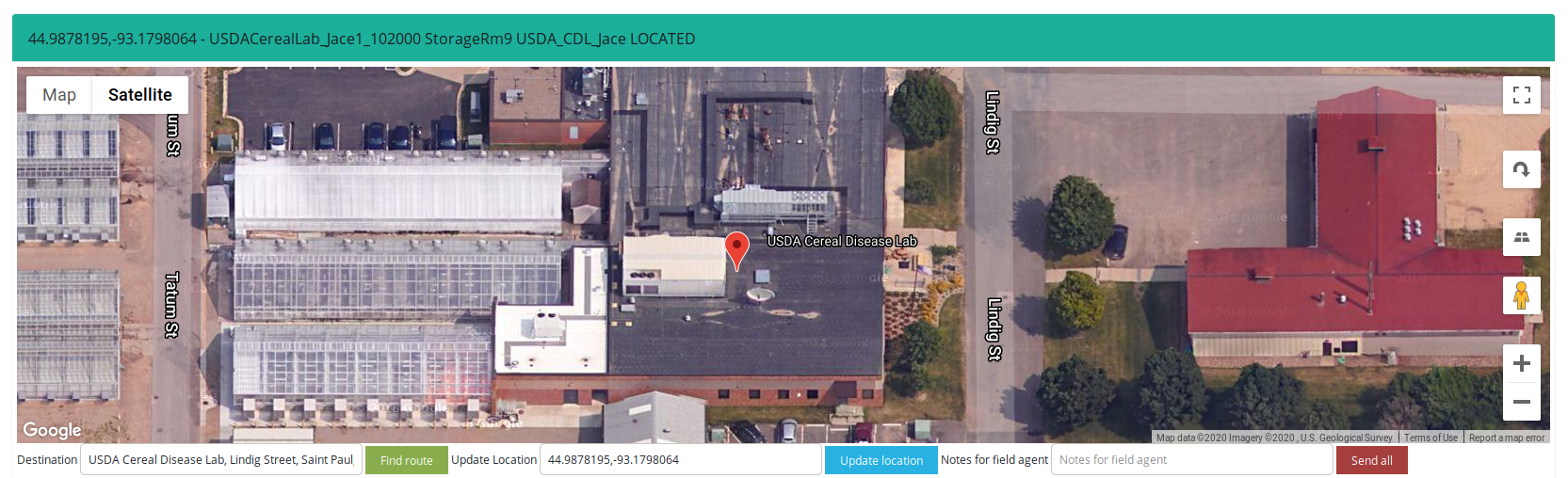
When you know what facility it works in, you should check for other information like network, other ports or less technical - intel about range of activities in the lab and people involved to send more trustful phishing messages.
Except of this one finding, Niagara Fox reveals station names for following interesting places
- Military Entrance
- USPS central plant
- Government complex in Monroe Country
- Lockheed Martin facility
In Russia there is literally only couple of these devices. I was told that the main reason is that Chinese equipment is much more cheaper than American. Same thing is for network devices - switches and routers.
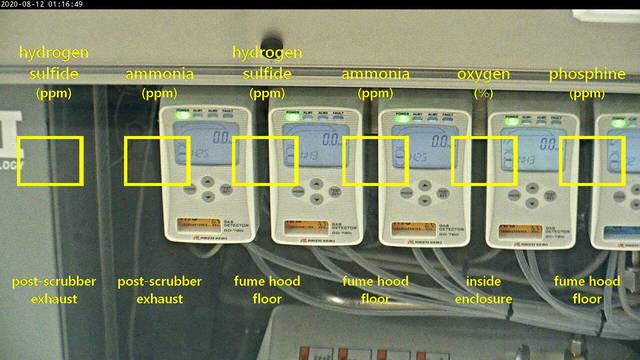
But both countries have something in common and it's exposed cameras in different places. In United States there are around 2300 exposed cameras with screenshot that Shodan has indexed, in Russia - ~400,
United States


Russian Federation





No word from CIS.
UPDATE
CERT RU works to make devices secure and I shared database with them.
Conclusion
It is one of the longest article on the blog but I feel like I barely touched the topic for both countries. There are endless possibility to spy on foreign critical infrastructure and I just showed couple of techniques that in my opinion can be used gather valuable intelligence. In addition, it is helpful to perform phishing campaigns and network reconnaissance. I am also aware that presented techniques might be dummy for multi millions government espionage techniques, however with ꓘamerka you can set up a small ICS espionage system and geolocate exposed devices in different facilities on your own. I'm quite sure if I will be working exclusively on this subject for 3-4 months, I would be able to gather essential intelligence, weak points and potential entry points into critical infrastructure for both countries.
This time $50 goes to InfraGard in Los Angeles to keep America critical infrastructure safe.
InfraGard is a partnership between the FBI and members of the private sector. The InfraGard program provides a vehicle for seamless public-private collaboration with government that expedites the timely exchange of information and promotes mutual learning opportunities relevant to the protection of Critical Infrastructure.
To make it fair, another $50 goes to RUSCADASEC
RUSCADASEC is an independent non-profit initiative on developing the open Russian-speaking international community of industrial cyber security / ICS / SCADA cyber security professionals