From now on ꓘamerka is not only simple script for mapping devices, it has evolved to fully equipped reconnaissance web application. It allows to visualize any country with Industrial Control Systems devices or particular territory with Internet of Things devices. Moreover, it supports Google Maps for identifying real location of devices, Shodan for intel gathering , Binary edge for mapping attack surface and WhoisXMLAPI for whois information
Demo
Give me some love on Twitter
(…) nobody really exactly understands all the things it is being used for (…)
(…) it’s changing so quickly, that even the experts don’t know exactly what’s going on
(…) it’s different than it was an hour ago. It’s constantly changing, it’s constantly reconfigured
(…) it’s very hard to get people focused on plan B when plan A seems to be working so well
(…) we take a system that’s basically built on trust, (…) we’ve kind of expanded it way beyond the limits of how it was meant to operate. And so right now, I think it’s literally true that we don’t know what the consequences of an effective denial-of-service attack on the Internet would be, and whatever it would be is going to be worse next year, and worse next year, and so on
Introduction
The quote comes from Danny Hills’ Ted talk and refers to the whole World Wide Web but also suits for the research I have been doing. It illustrates how things in the Internet change rapidly. The whole Web is reconfigured constantly, from small home networks to large manufacturers facilities or industrial factories, and no one is really responsible for the state that Internet, in general, is right now. Popularity of Internet of Things grows very fast hence there will be more and more devices connected directly to the Internet. Some of them operate in infrastructure that should be secured more than other, like hospitals, government offices or power plants. Any IoT device, for example MQTT, camera or even printer may be used to spy on users and gather detailed information about facility that device is running in. Moreover, a lot of devices are directly touching critical infrastructure and are exposed to the Internet - wastewater systems, wind farms, power plants and lot more. Many machines run variety of additional services that are vulnerable to different kind of attacks that may results in total compromise. Also a lot of devices uses default configuration with default passwords, so anyone can take over it. It’s not your device anymore when someone else can get access to it.
Article will present new ꓘamerka GUI, it’s capabilities and couple real life use cases.
From small script to ultimate reconnaissance web application
Exactly one year a two days ago, first version of ꓘamerka was released, it was simple script which presented map with cameras from Shodan based on one query. With time it was updated to supports different social media and more devices. It also had it’s appearance on ICS conference in Atlanta, Georgia and it motivated me to do something unique.
So, after many sleepless nights I can present ꓘamerka GUI powered by Shodan and supported by Binary Edge and WhoisXMLAPI.
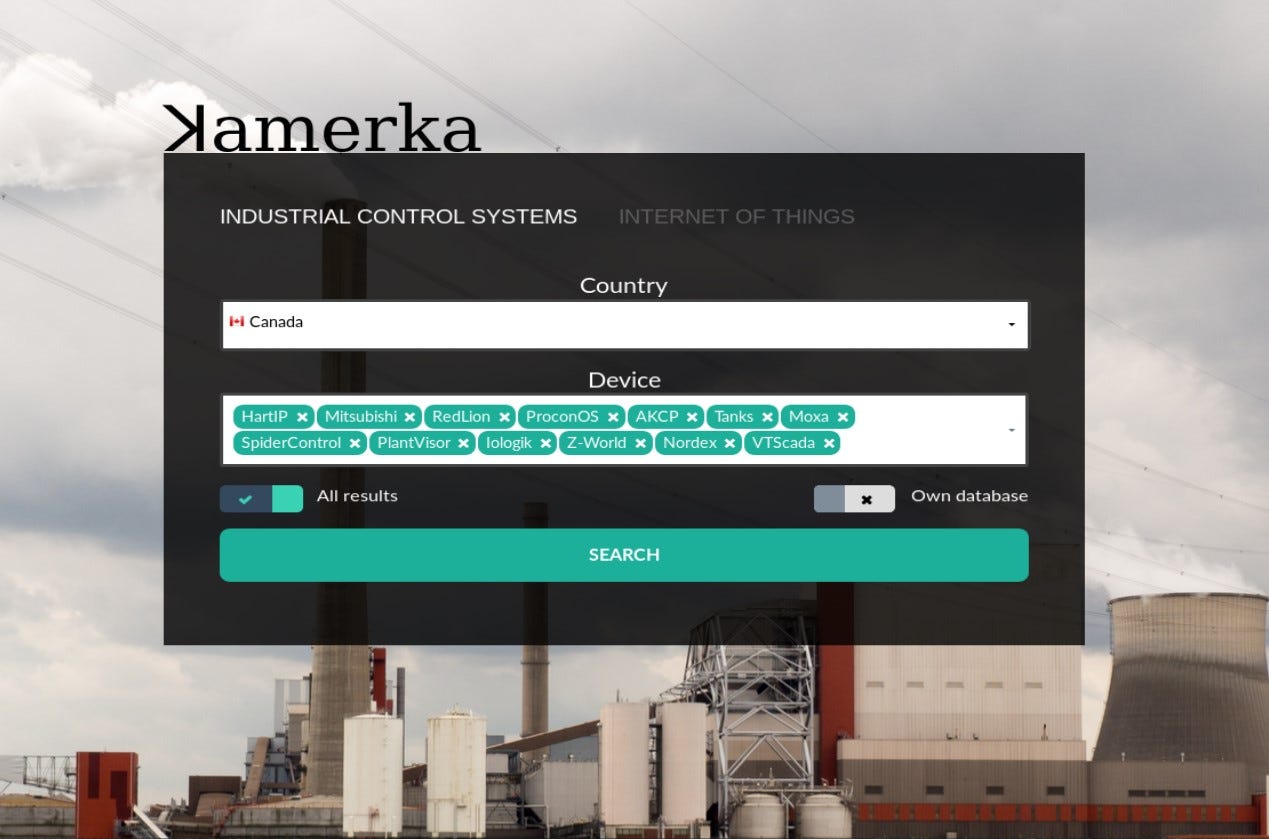
It is completely different that it was at the beginning, it supports variety of new devices — Pl@ntVisor, SpiderControl, Moxa, Nordex and even fuel tanks. Full list of supported devices and queries you can find here.
The main purpose of ICS module of ꓘamerka is to map attack surface, in terms of Industrial Control Devices, for any country. Most used products, ports, protocols or city with the biggest amount of exposed devices are part of attack surface. It’s really important to understand what device is used for and where it is located. (I will show how to geolocate some devices a bit later)
ꓘamerka has also separate section for cities or territory, you can pass the coordinates and choose from different devices.
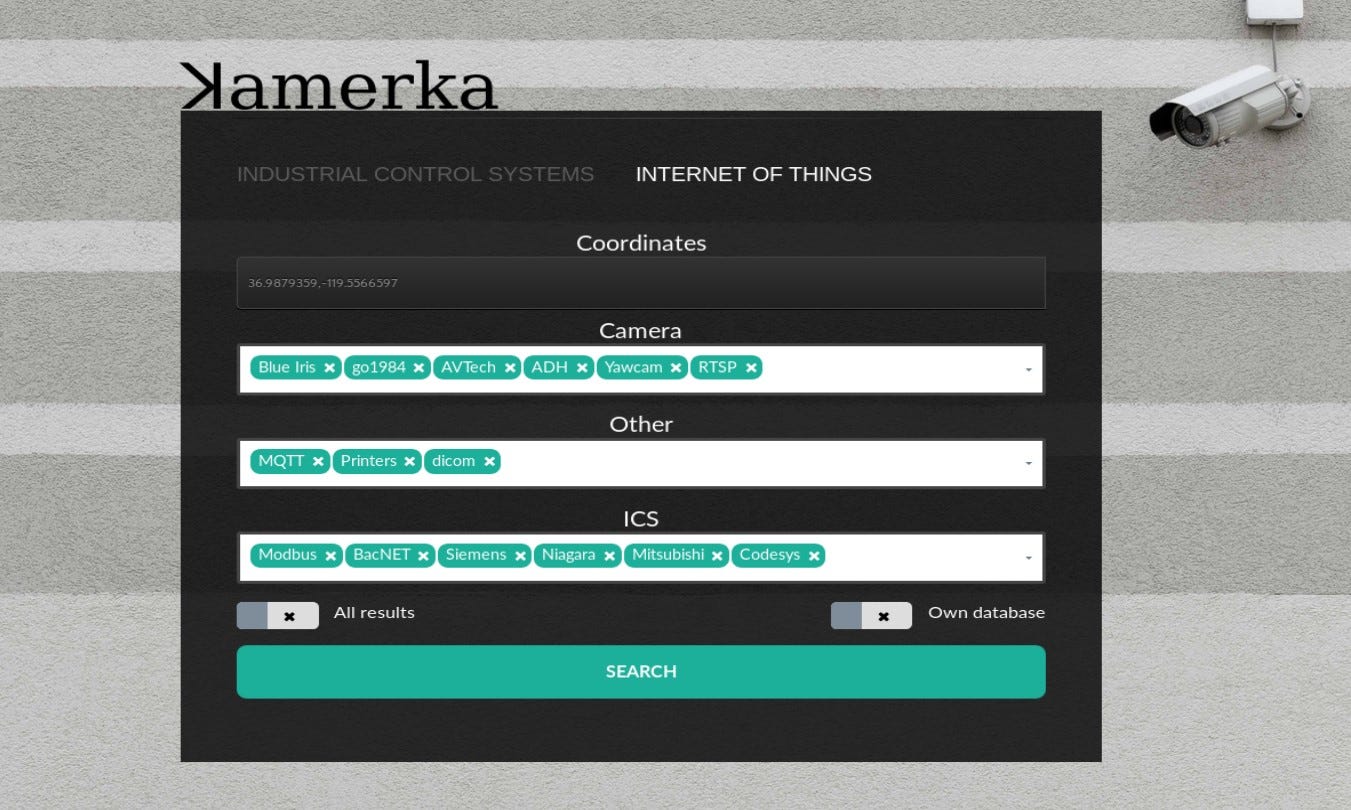
Also, IoT module has been updated and supports new type of cameras and devices like — DICOM (Digital Imaging and Communications in Medicine), Yawcam, go1984, Blue Iris and more.
Worth to note that “All results” checkbox, if turned on, will download all results from Shodan, otherwise only first 100 will be checked. For example, mapping whole Canada can cost lot of credits, so to avoid that you can turn this option off. Other option “Own database” is not used currently but shows that it’s possible to implement other geolocation database than Shodan’s default one. As far as I know it uses MaxMind database but if someone has access to more precise one, please let me know.
It keeps track of every device it found and display it on clear dashboard.
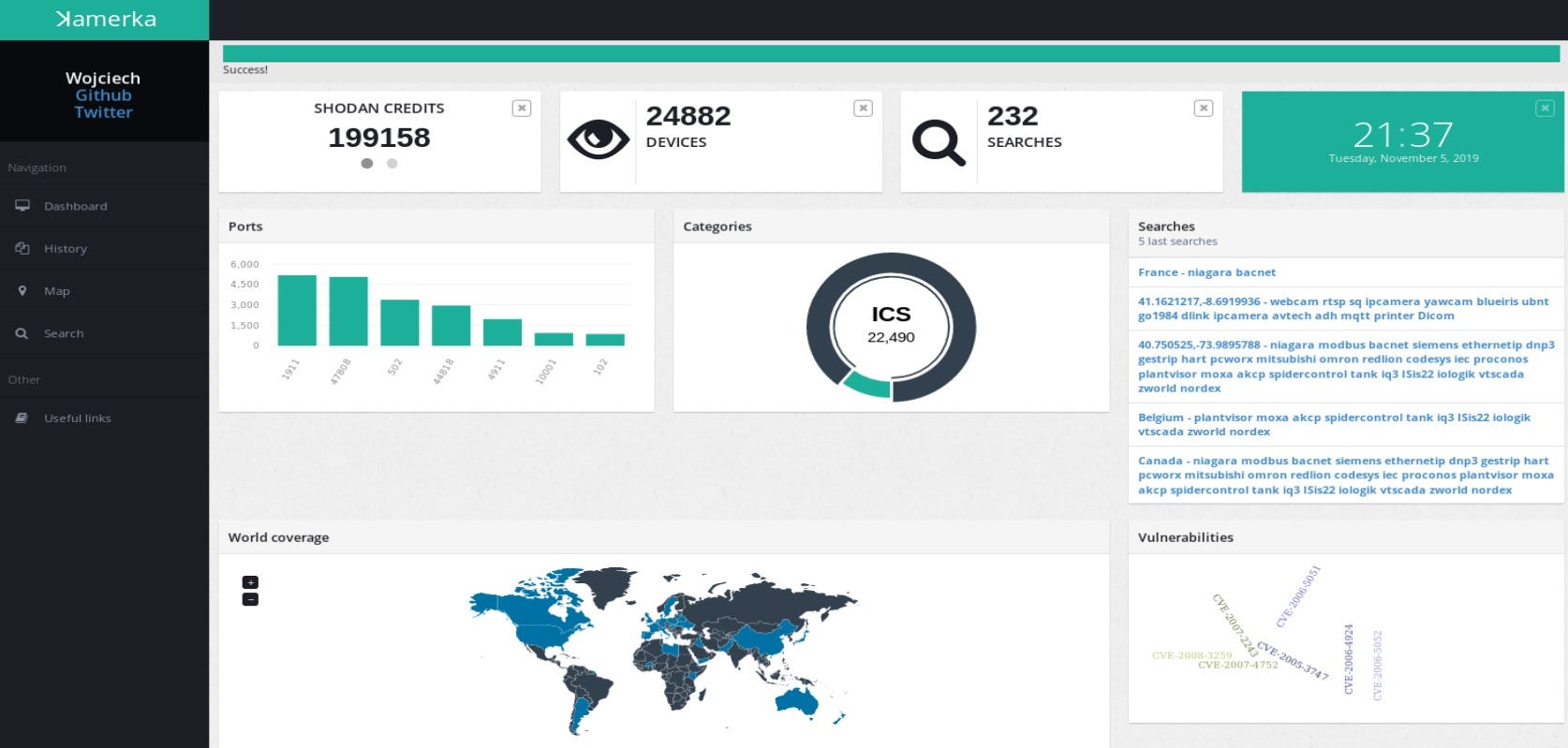
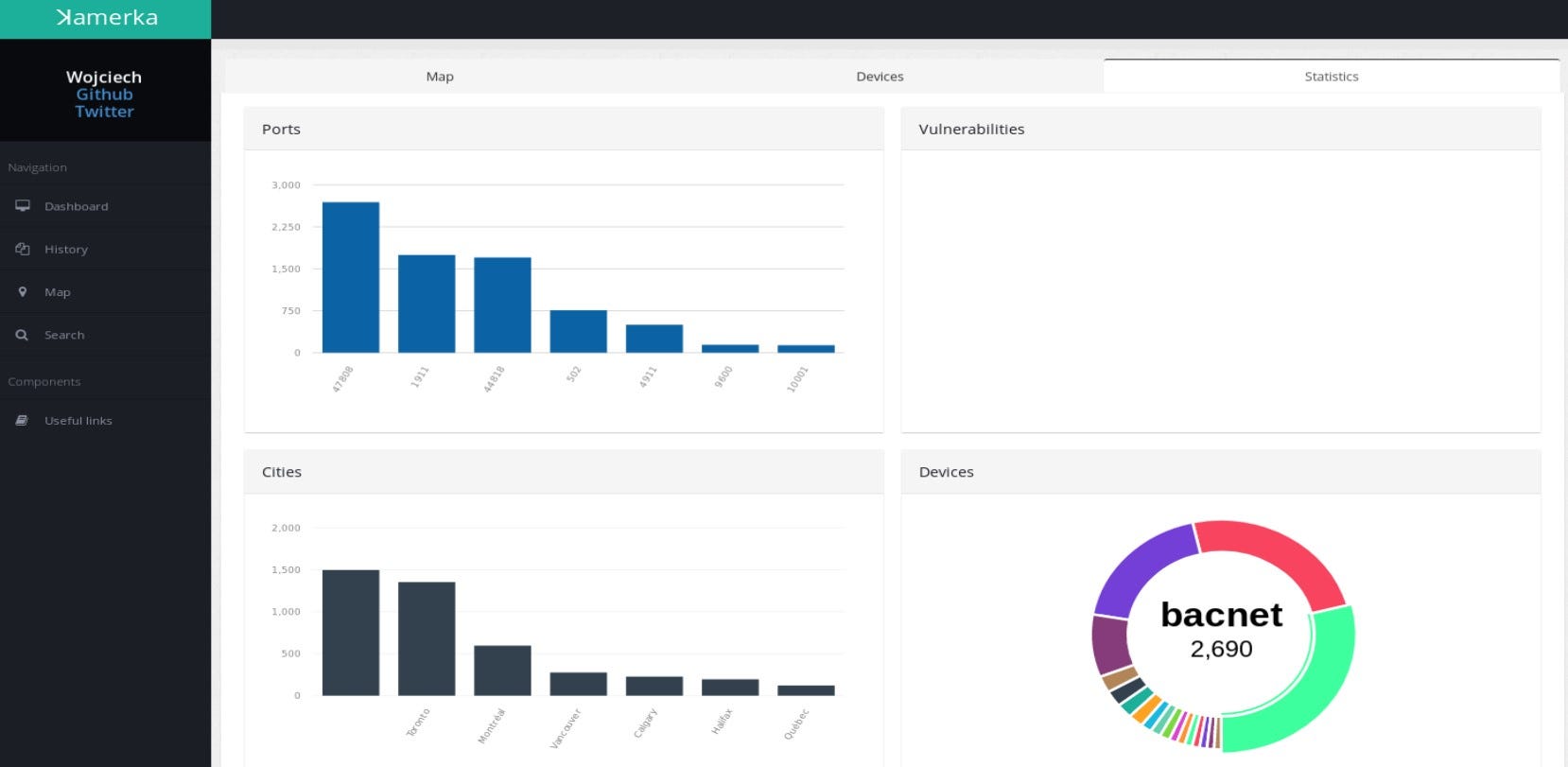
Here you have access to your Shodan/Binary edge credits, amount of searches and devices, most used ports, categories of search, world coverage, vulnerabilities and your last 5 searches. The statistics are general for all searches. Also different statistics are displayed for each results in separate tab. I could explain each view but it would be super boring and you can go to description and demo here. So instead, I will show it on real life examples.
Devices in New York
Let’s start from mapping territory, as an example I will show exposed devices near Manhattan, New York.

Map supports clusters and displays amount of devices in this coordinates, if you click on any icon, link to detailed information about device will be shown.
As mentioned earlier, statistics for particular territory or country from you searches are also displayed in separate tab.

Let’s try to target one example device.

When you found potential device that can be geolocated, map and details will be displayed. Moreover, as you can see above you can scan for different devices in neighborhood with your own query, devices then will be automatically added to the map. Flickr photos are also supported, you can just click on scan button and display all Flickr photos on map. In some cases it makes finding and targeting easier.
In this case we have exact address of one of fuel tanks in Brooklyn. ꓘamerka can extract location indicators from device response, these indicators are “Station name” for Niagara, “Device”, “Location” and “Description” for BacNET and full address for fuel tanks. What is cool, the indicators are saved in database and you can search for critical infrastructure based on your keywords.
Google Maps in ꓘamerka includes routes drawing, so you can basically check how accurate geolocation database is. Sometimes it points to next street and in some cases to the nearby city but with this solution you can handle this.
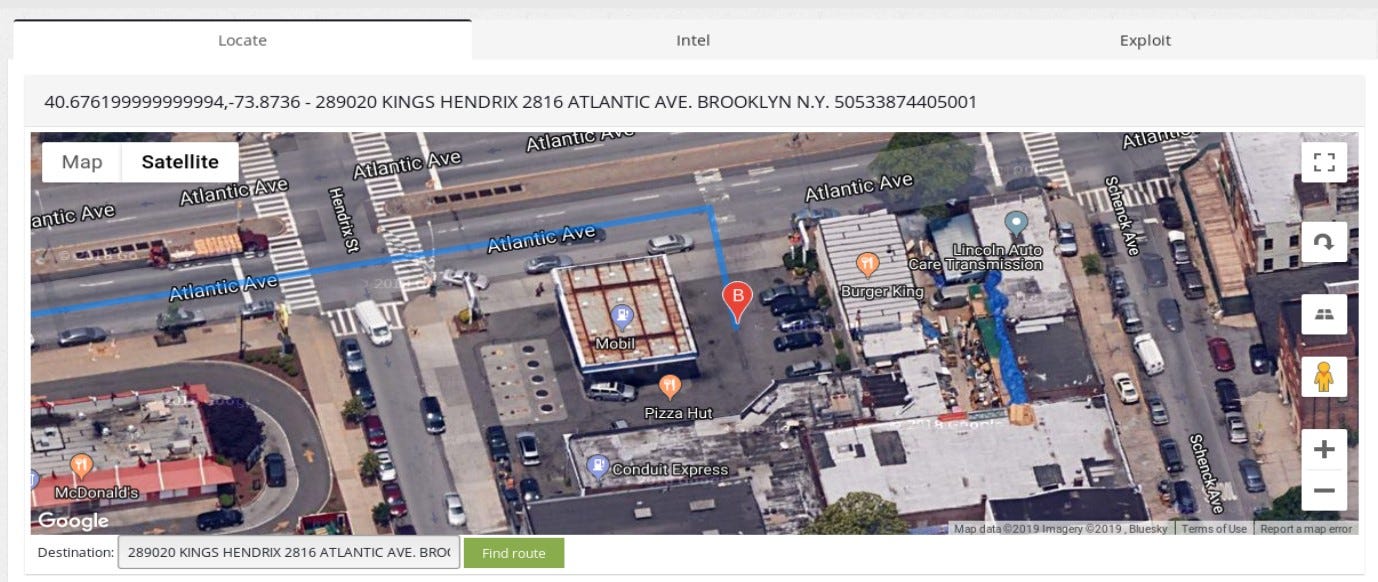
It actually is a Mobil station, we can clearly see the gas station and one of their fuel tank is connected directly to the internet, we can lookup what is inside based on the device response.
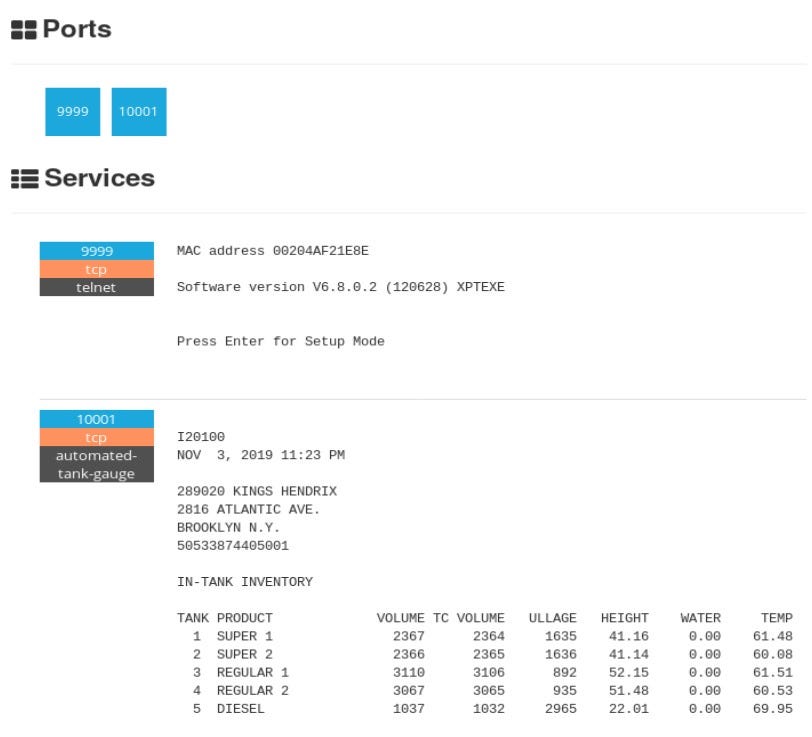
You can clearly see what products are kept, their volume or temperature. In addition, there is telnet open which can help to gain access.
Gathering offensive intel
To demonstrate offensive intel that ꓘamerka provides, let’s take a look on one of the findings from Denmark. Being precise, it’s a detention facility or jail.
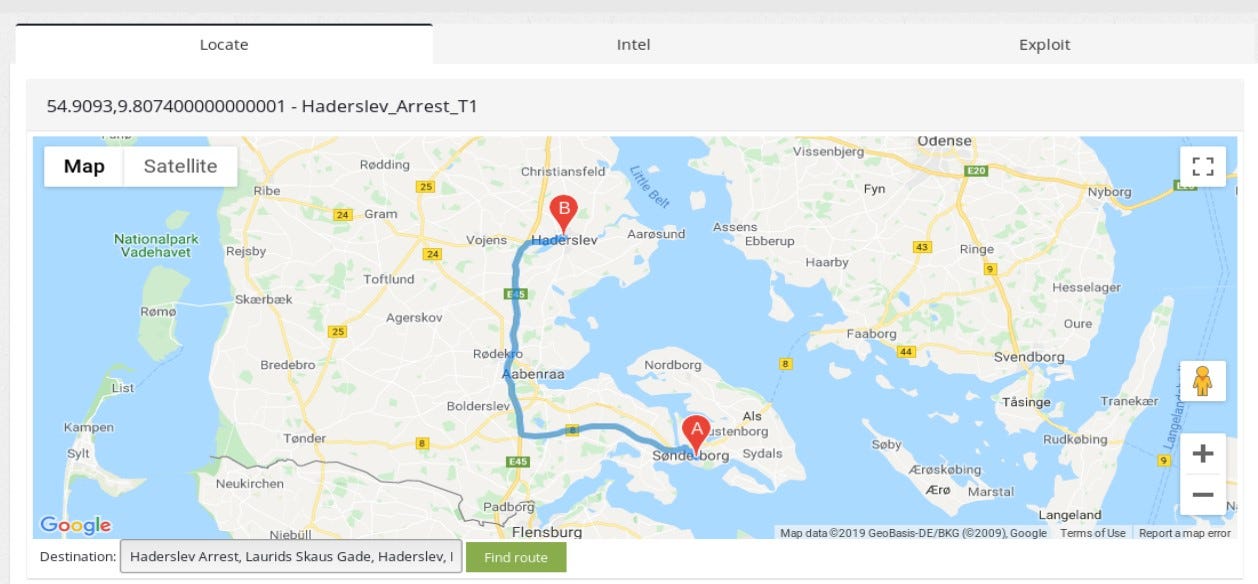
Geolocation in this case, it’s not super accurate but extracted indicator allows to narrow the search to nearby city Haderslev and concrete place.

Of course, ꓘamerka supports Google Street View in maps, so you can actually lookup the place to be 100% sure and gather intel on physical security.
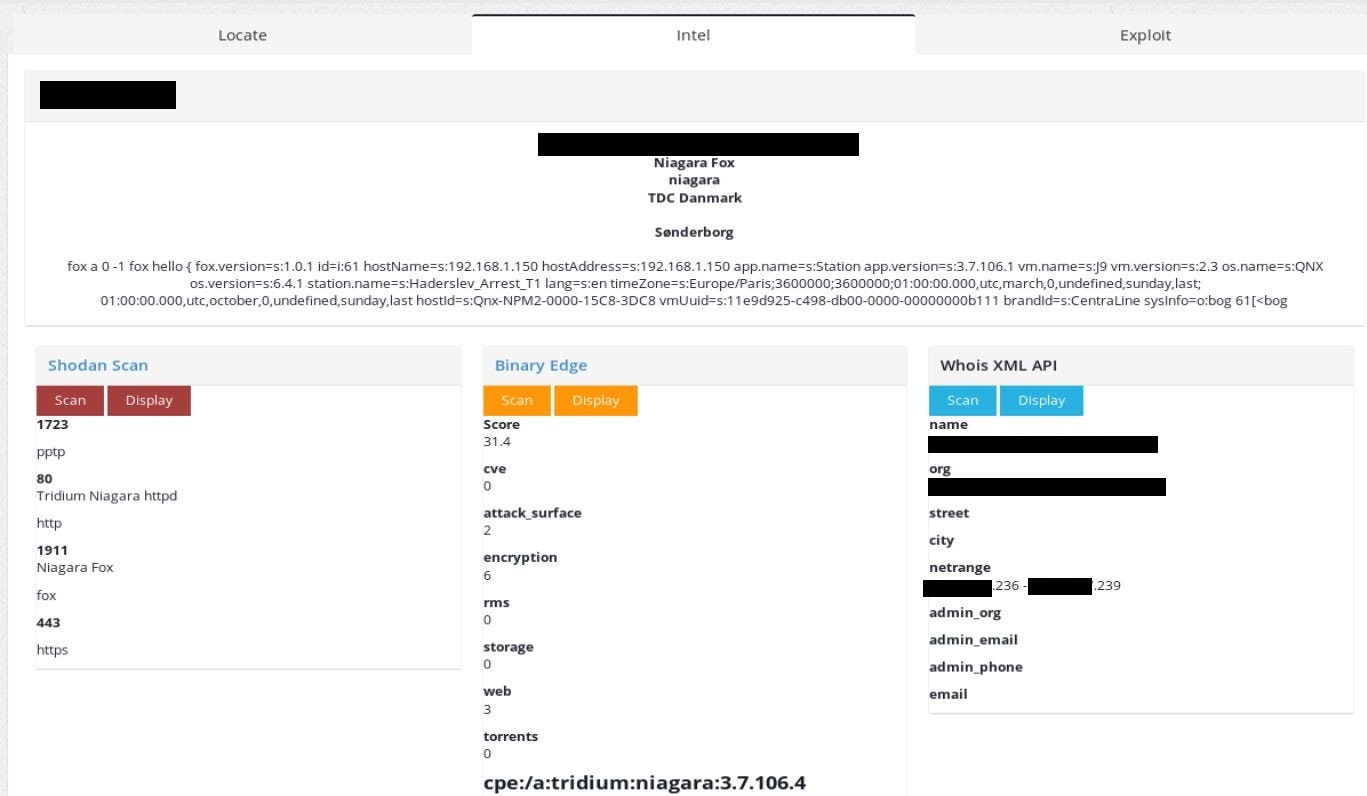
The chapter title is not random, with ꓘamerka you can lookup other ports that are listening on the machine, together with Binary Edge IP score, which is really awesome. It shows potential attack vectors based on the extracted information from device. I really recommend you to get acquainted with the Binary Edge rating and how it may help you to map the attack surface.
The last option can give insight who owns the netrange that device operates in. It’s also useful to be aware of this since it can help to locate device and scan whole netblock or nearby IP address in order to get access to machine. Corresponding IPs can be in the same network and more vulnerable so with lateral movement, one can get access to the main device, which is located in detention facility in this case.
State of Industrial Control Systems in Canada
You could read about state of ICS in Poland and Switzerland and about exposed critical infrastructure in United States. In today’s episode we are going to Canada, country of maple syrup, hockey and moose running on the streets.
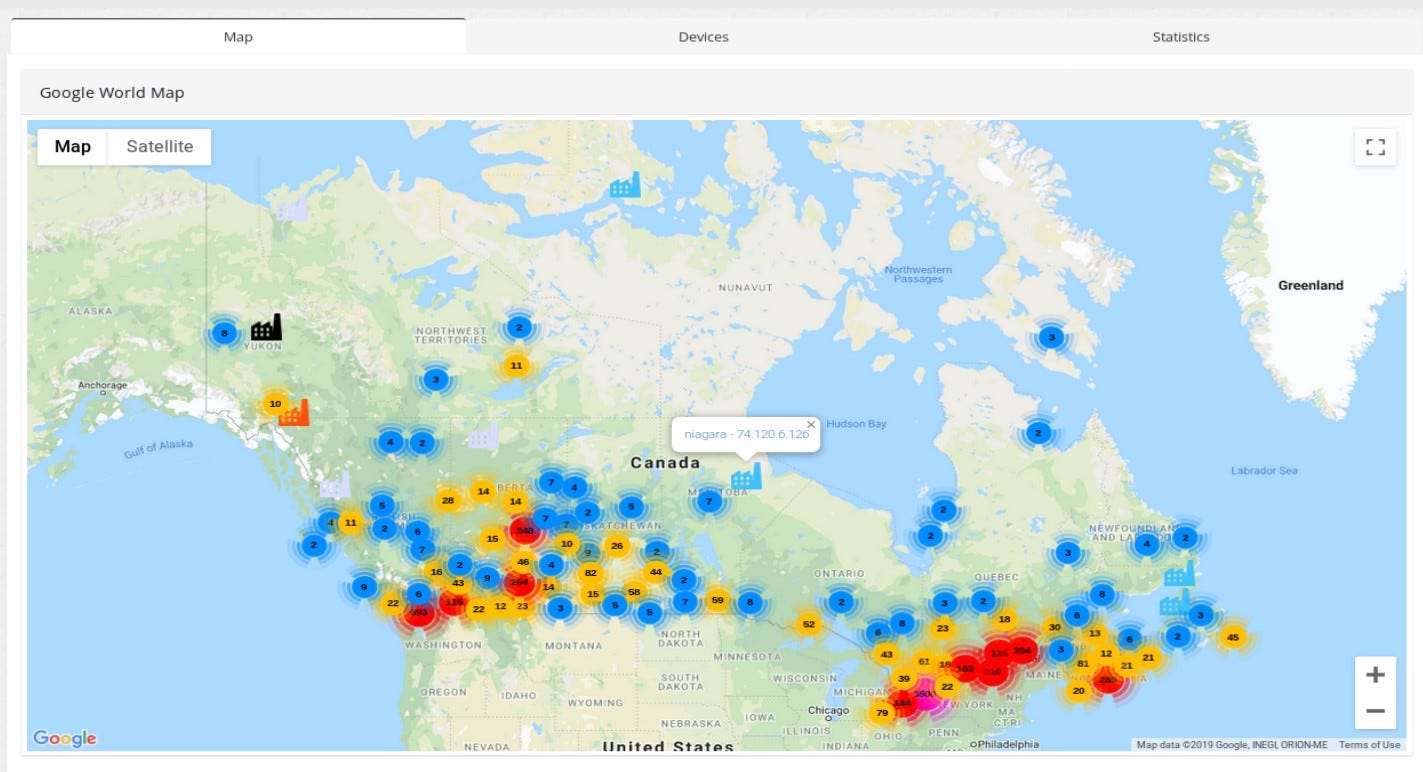
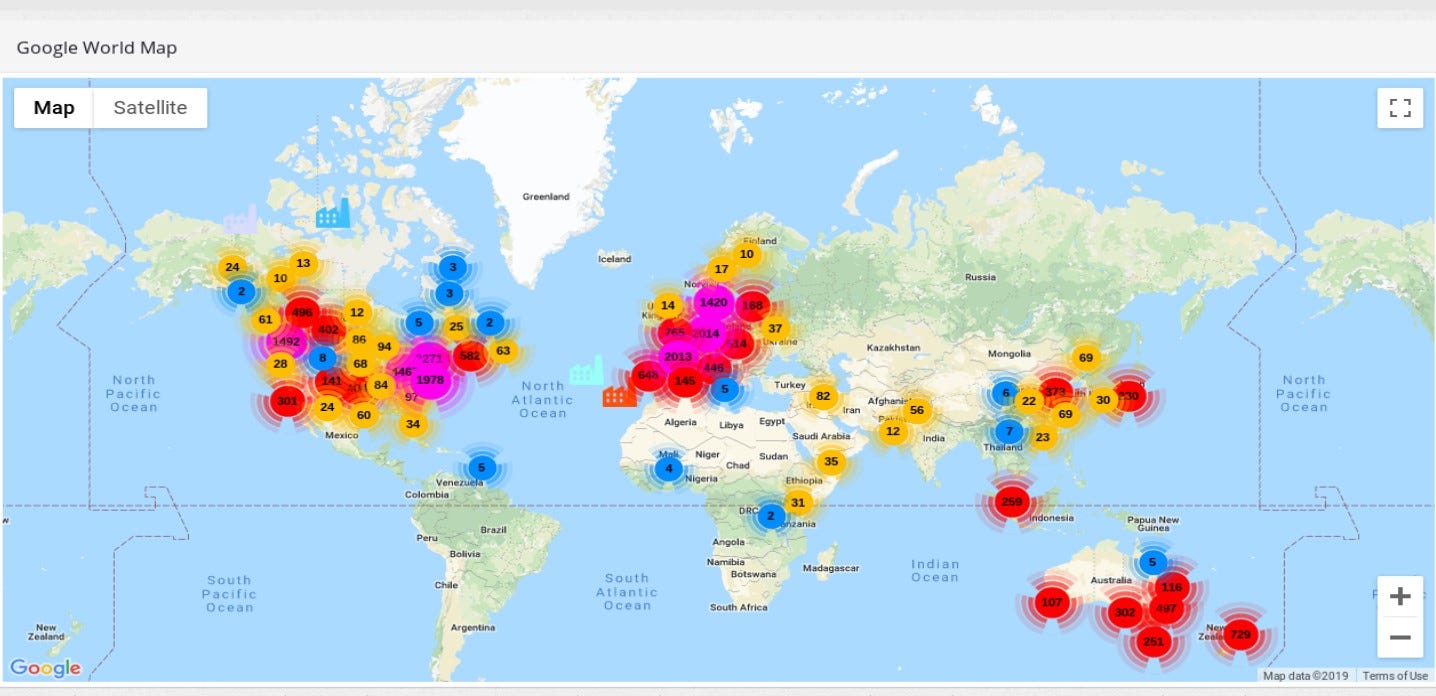
These are all exposed devices in Canada, based on the ꓘamerka & Shodan queries.
The article in not about Canada critical infrastructure but I chose couple of examples to show interesting findings. One of this devices can be a BacNET disclosing exact location and usage — “Airport Executive Central Plant”, does not sound as it should be publicly available.
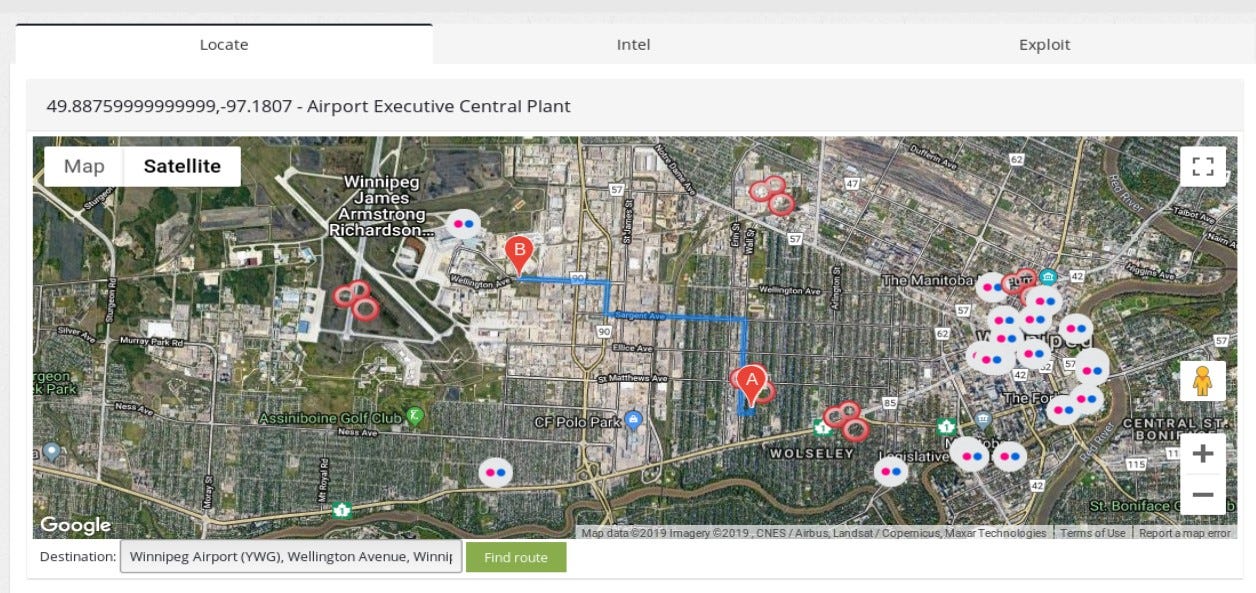
Location points on Winnipeg city, there is only one airport there so I assume with high confidence that device operates in this particular facility. Name of the device indicates that it’s central plant on airport, having access via some vulnerability or misconfiguration like default password would allow to change settings in the plant, which may wreak havoc on the airport and cost lot of many for the facility.
Interesting case of Dawson City- support ꓘamerka with manual research
Beside from map and statistics, ꓘamerka lists all of the found devices and supports search in any field. Extracted indicators are available and searchable as well.
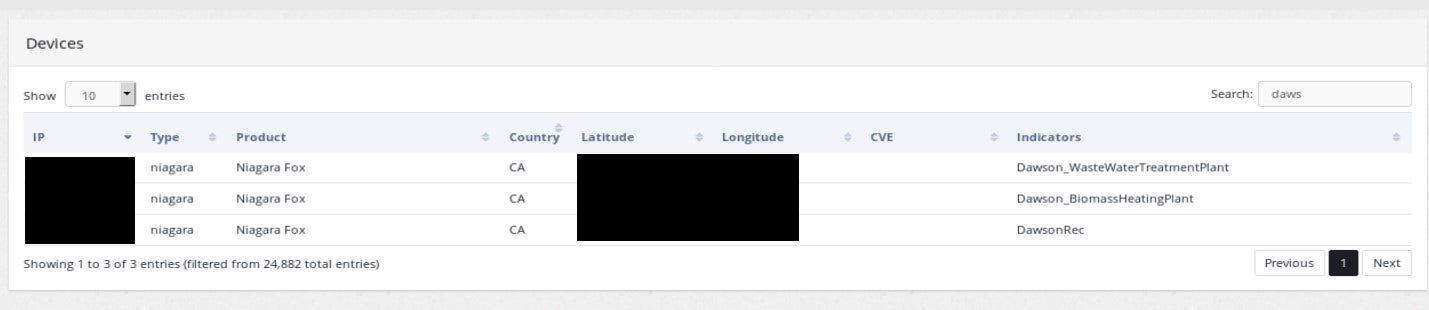
Dawson City is located in Yukon, Canada, the unpacked indicators points to three places — “Waste Water Treatment Plant”, “Biomass Heating Plant” and something titled “DawsonRec” it might be recreation center(?).
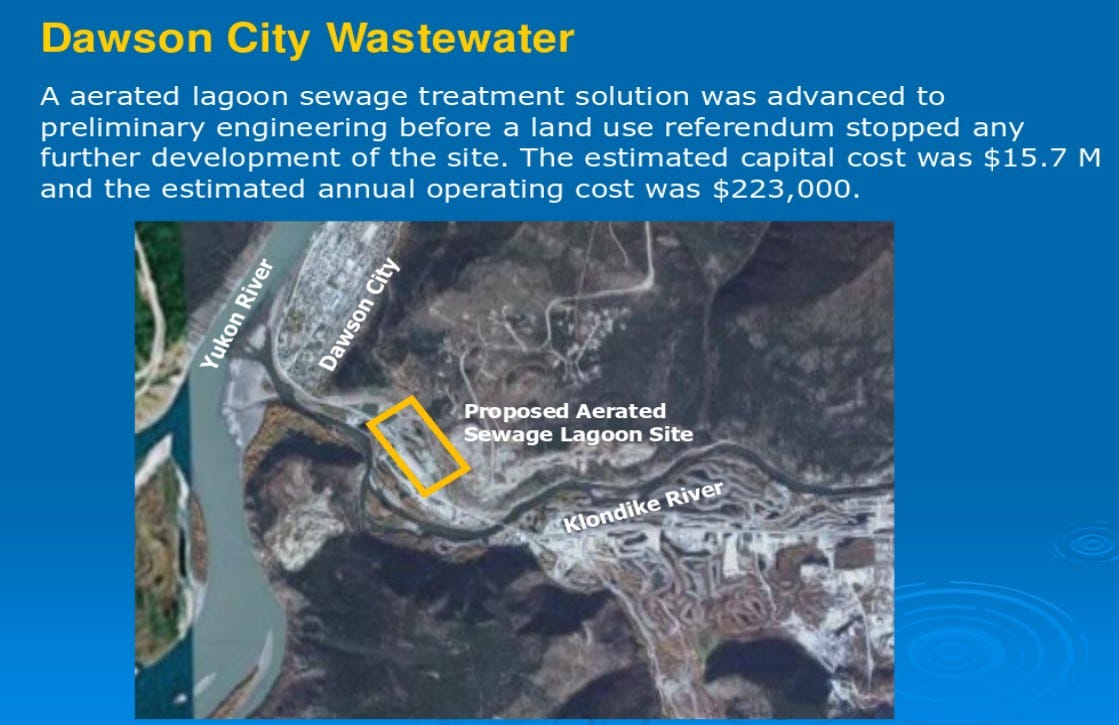
Waste Water Treatment Plant location points couple kilometers from Dawson City but Google does not keep track of any WWTP in Dawson and it shows small building in the center of city. So how to locate the actual plant?
From the publicly available sources, we can get info that this plant will be discharged

Because of the costs, waste water plant will be replaced and renovated. I strongly assume that one of the reasons why this plant is exposed is also a money saving procedure. With remote access, technicians can access plant without on site visit which is more expensive.
In addition, many other information are publicly available about the plant. Even when Google does not know the place, you can always go to official city website and look for location of their infrastructure.

Presentation shows details about planning of waste water treatment plant.
As we all know, sewage systems are one of the infrastructure that require additional security measures.
Other device that was listed by ꓘamerka is “Biomass Heating Plant”, it also does not sound good to find this kind of devices exposed to the Internet. After quick research we know that Dawson City is really cold place in winter, so heating is super important there and also part of critical infrastructure in this case.

OK, then we need to connect IP to the real device and establish a geolocation point.

Document describes heating infrastructure in Dawson City in details. It’s another example when sentence “Information does not have to be secret to be valuable” works.
To sum up, the main culprit in these scenario is of course money. There is no money to make infrastructure secure and probably no plan B in case of outage resulted by cyber attack.
New vulnerabilities are released every week or month and some of them are critical. Exposing your device, especially involved in critical infrastructure, make it potentially vulnerable to new threat which results could be devastating. Turning off the heat in winter season could paralyzed the city and tampering with waste water treatment plant could left many people without access to clean water.
Support for new devices
As mentioned in previous chapter, new devices have been added. You can lookup whole list with corresponding queries here . Some of the devices are very unique and only couple are exposed per country or only in one specific country. Example could be Moxa Iologik device that it’s most popular in Italy.
Pl@ntVisor is mostly used in refrigeration and air conditioning systems
In some cases to find real location, you need to look deeper — inside of the exposed configuration. Here, device exposes location by server name and server location fields.
Moxa Iologik — data acquisition and control device https://www.moxa.com/en/products/industrial-edge-connectivity/controllers-and-ios/universal-controllers-and-i-os/iologik-e2200-series

The IQ3 controllers are Building Management System controllers that use Ethernet and TCP/IP networking technologies

Meteo control IS2 also allows unauthorized access.

and discloses real location

So with this update you can search for dozens of new devices. It’s also easy to add new ones so I plan to fill it with every possible from Critifence database and create my own one with all of the queries.
Further Development
I see a lot of possibilities for further development - more queries, integration with Nmap and PLCscan, offensive capabilities, more social media sources or automated separation critical infrastructure from other devices. Also some devices publicly accessible can change to critical infrastructure if you have enough information about the target. By this I mean that elevators or lifts are not dangerous per se but if you know that there is major event in this place and gather crowds of people then it might be dangerous for their live.
The end goal for ꓘamerka will be to map and visualize attack surface for cities (or their strategic places) and country critical infrastructure.
Because there is a lot to discover.

Conclusion
Nowadays, ransoming cities or states for their data is common practice for cyber criminals but with rapid expansion of Internet of Things and Industrial Control Systems it may change to ransom cities for the services like electricity, waste water, heating and other critical infrastructure needed to keep people safe and comfortable. I realize it’s not a simple task to take over whole power plant but it can start from small misconfiguration like exposing device to the Internet, using default credentials or running other vulnerable software. No one is responsible for security of city, is it National Security or local issue and only local government should be involved? Anyway, I doubt that there are many cities with plan B in case of cyber attack on critical infrastructure.
Originally published on 6th of November, 2019
Please subscribe for early access, new awesome things and more.



