Script creates map with cameras based on your geolocation or exact address. It uses Shodan API to find cameras, Geopy to find address and measure distance, and Folium to draw a map.

Introduction
This post will be really quick one, I want to share one of the curiosity I wrote recently. It’s proof of concept to visualize cameras from Shodan API into real map. Some of the cameras are left open with no authentication so you don’t need to have any hacking skills to get access, and depends on where camera is located you can get interesting view in some cases. With lot of luck, it can help you with OSINT investigations or geolocating photos. Imagine you have photo to geolocate and you found open camera exactly pointing to this place, or somewhere nearby, which can give you hint.
ꓘamerka
The most significant points in the script are: Shodan API, GeoPy and Folium library.
Shodan allows us to find any device in given location based on longitude, latitude and radius, responsible for this is filter “geo”. Next, filter “device” is added for displaying only webcams. Whole command looks like this: “geo:37.235,-115.811111,5 device:webcam”.
Thanks to Geopy, you can search by address or particular building. Additionally, it measures distance between camera and initial target.
Folium is amazing GIS (Geographic Information System) library with lot of handy options and it looks really cool. Results from Shodan are passed into Folium to create map with markers referring to each webcam. Markers are in two colors — red means that camera has probably some form of the authentication and does not return 200 OK code, while green color says that it’s open or displays some login panel.
Moreover, markers are grouped, in case there are many in one place. After clicking on any, information like IP, model and distance are displayed.
Governments buildings
Some buildings have to be secured in proper way, especially those related to government. City halls, military bases or training camps should be free from any cameras with public access but no one can control neighborhood and surroundings. I found really interesting article about webcam OSINT in Sweden where author was tracking submarines. It’s possible that someone can accidentally leak some information because of misconfigured camera.
You can search by address
kamerka.py –address “White House” –radius 2Cameras in radius of 2km from White House, which Shodan indexes.
Spying & Reconnaissance
In addition you can check your neighborhood or use it to get reconnaissance before red teaming assessments. Of course, it depends of the luck, because not every camera has public access and majority are used indoor — in shops, warehouses or private pensions.
Second way of searching is giving exact coordinates.
kamerka.py –coordinates “” –darkThe coordinates are from latest Wikileaks dump and shows cameras near one of the secret Amazon warehouses.
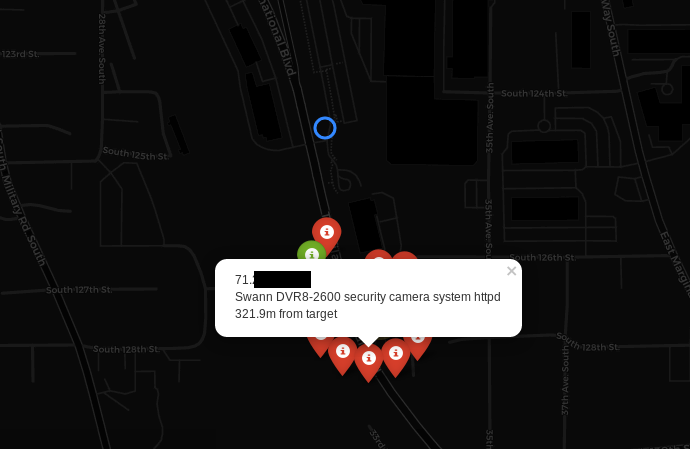
Dark theme can be set by “ — dark” flag. If you have problems rendering OpenStreetMap, you should use dark theme.
Conclusion
Usually people do not care about IoT security and leave their cameras open or not up to date. In results, they are added to botnet and are responsible for Ddos attacks. But it can be used also in spying and reconnesaince techniques. You can search whole world and check if there is any open camera in sensitive place, which may register same events or buildings that shouldn’t be seen. Don’t test any webcams if your are not the owner of the device.
Originally published on 4th of November, 2018




